Lab 2.2 Syslog Organization on log01 - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
This technical journal will cover/link to the following information:
-
Augment your documentation to include how to change a vyos password
-
Describe how to forward authentication events from vyos to a remote syslog server
-
Make sure to capture any difficulties or observations as reflections
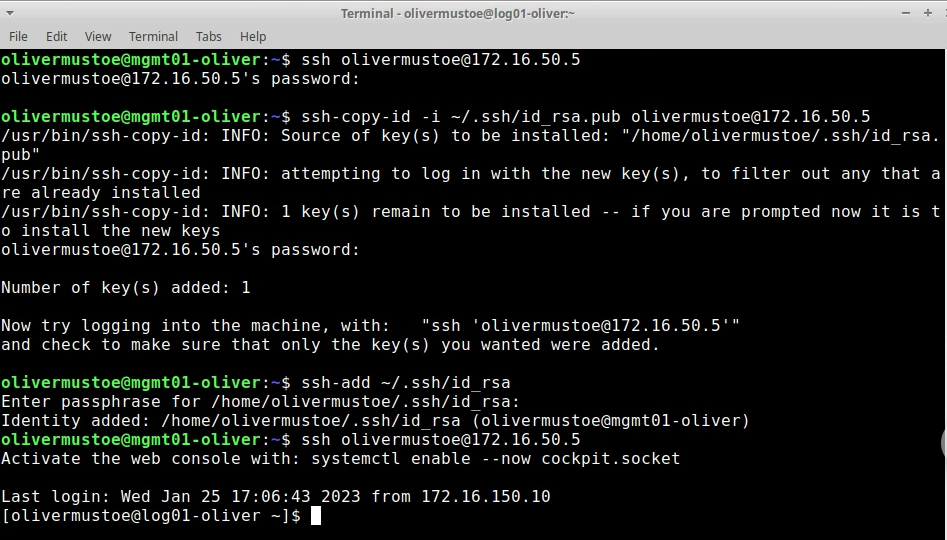
SSH keybased authentication setup
The following commands can be used for passwordless SSH:
# Sets up keys
ssh-keygen -t rsa -b 4096
# Delivers keys to designated host
ssh-copy-id -i ~/.ssh/id_rsa.pub {USER}@{IP}
# Add key to ssh-agent (can add -t flag to specify time)
ssh-add ~/.ssh/id_rsa
(NOTES: {USER}@{IP} is the user/ip of the host you wish to passwordless SSH into.)
Below shows the process of setting up SSH keybased authentication to a host with a user of "olivermustoe" and a IP of "172.16.50.5" (keys already generated):
Authpriv logging on Linux
Prereqs: Following information expects a syslog client setup. Output of logs will be set according to the settings outlined in Time settings.
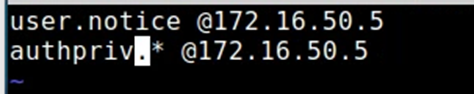
Inside "/etc/rsyslog.d", add the following to the .conf file (in this case "sec350-client.conf"). First line in screenshot should already exist:
authpriv.* @{LOG_server_IP}
Then the service should be restarted:
sudo systemctl restart rsyslog
After trying to login/successfully logging in, information should populate in "/var/log/remote-syslog/{HOSTNAME}/{DATE}.sshd.log" like the following:
Reflection
This week in SEC-350 was a lighter, but still informative week compared to the last week. I have dealt with logging before, but usually in the context of troubleshooting a problem. Because the problem is not usually time sensitive, I have never thought to make any sort of logs more robust in the time zone management, so this is good info to know. During the custom log organization, one of my collogues had a problem with their logging not changing. One of the major differences I saw between his and mine was that I created the file initially as root, and effectively filled in the content via VIM (initially tried to cat redirect it into the file, but that ran into issues.) While I am unsure if those were the causes, I will perform the action in a similar manner moving forward to ensure I don't run into issues. I have used SSH key authentication many times in the past, but never did it when it wasn't a requirement for the lab. As I move forward through the course, I will make sure to add this to my designated machines for faster system administration.