Lab 10.1 Linux Permission Vulnerabilities - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
In this lab we learned about Linux file permissions.
Notes
First we could use the command stat to see information about a file, such as the octal code (below is an example where the octal code is "4755.)
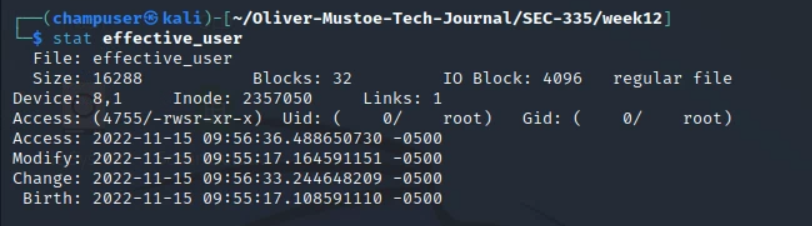
This command can be useful to see what file permissions are and what files have the SUID bit set (which means that the program runs with the owner of the files permissions instead of the user who is running it permissions. The leading 4 in the octal code indicates a SUID executable.)
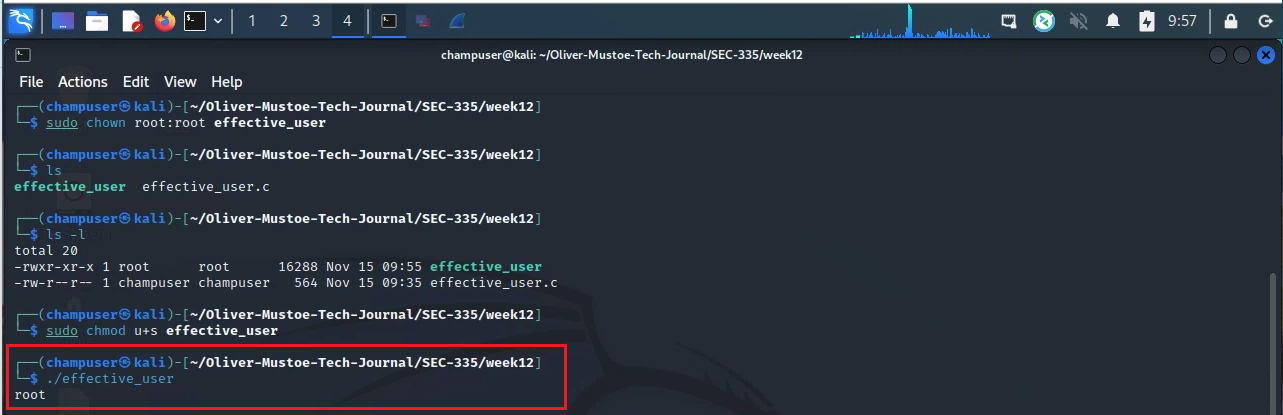
The following commands can also be used to change the ownership of a file (first command) and adding the SUID bit to the program (second command) (results can be seen in the screenshot!):
sudo chown root:root effective_usersudo chmod u+s effective_user
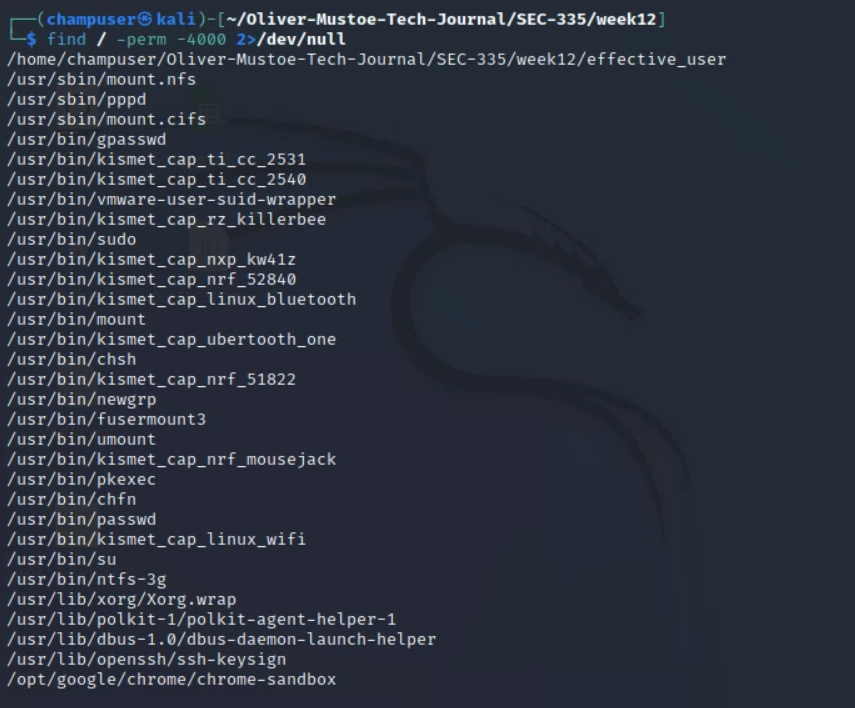
I could use the following command to find programs with the SUID bit (no errors, see screenshot for example output):
find / -perm -4000 2>/dev/null
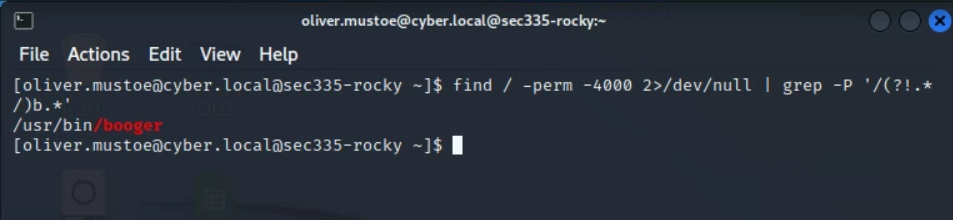
Can also be used with grep and the "-P" flag (Perl-compatible regex) to check just for the file names, example to find all files that start with "b":
find / -perm -4000 2>/dev/null | grep -P '/(?!.*/)b.*'
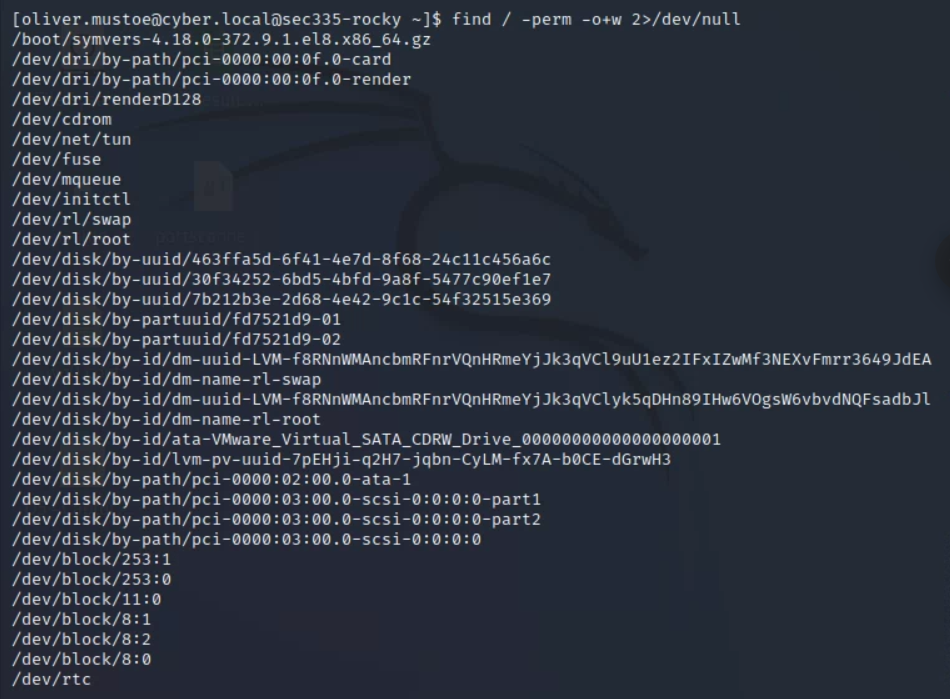
And I could use the following command to find world writable files (no errors, can egrep -v this (especially for "sys" and "proc" as they )
find / -perm -o+w 2>/dev/null
Sources
- https://www.thegeekdiary.com/what-is-suid-sgid-and-sticky-bit/
- https://docs.oracle.com/cd/E19683-01/816-4883/6mb2joatb/index.html
- https://askubuntu.com/questions/679344/how-can-i-find-world-writable-files-and-folders-and-set-the-sticky-bit
- https://www.redhat.com/sysadmin/suid-sgid-sticky-bit
- https://unix.stackexchange.com/questions/93327/using-a-perl-compatible-regex-with-gnu-grep-p
- https://stackoverflow.com/questions/8374742/regex-last-occurrence