AD and Wazuh agent on Windows - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
This journal details the setup of a Active Directory Domain on a Windows host as well as how to setup that system with Wazuh logging.
Table of contents:
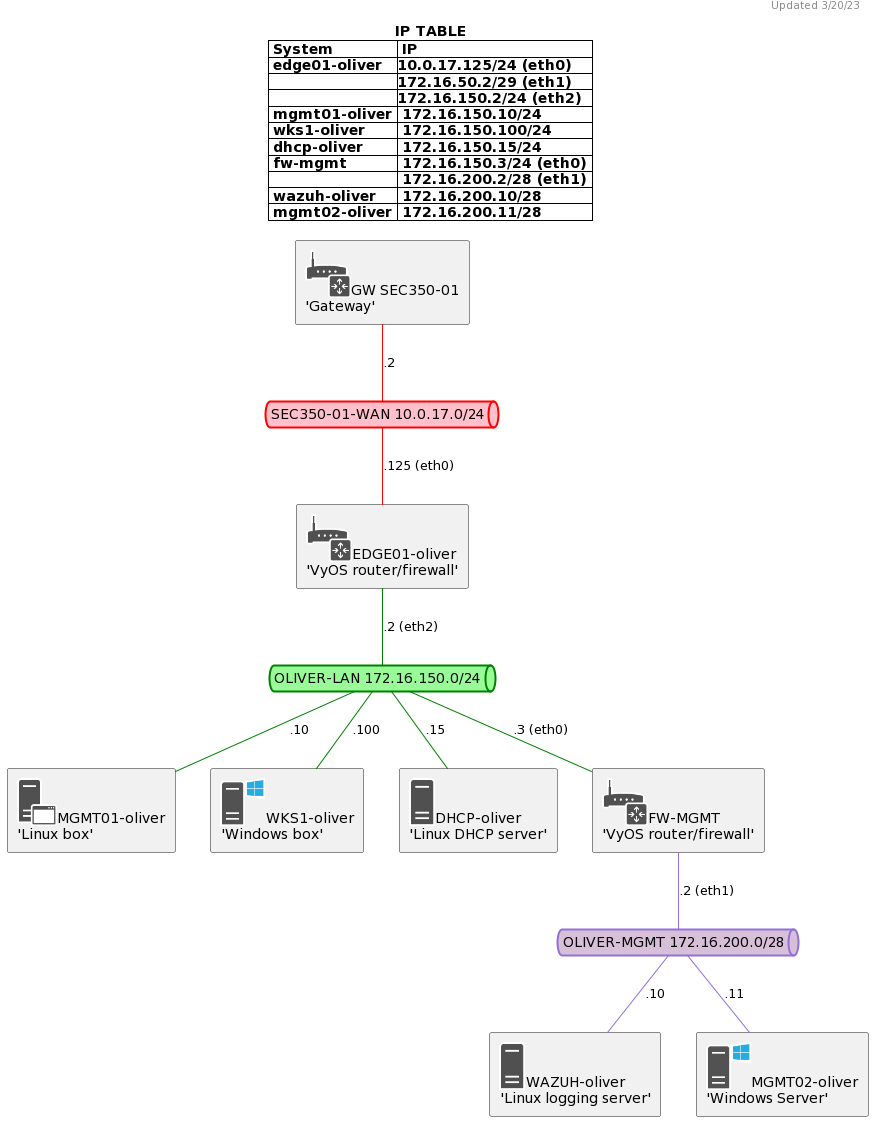
Below is the assumed minimum architecture of your environment (see Vyos configurations for the firewalls here):
Active Directory install
First I installed an Active Directory and forest on mgmt02 with the commands below:
# Setup AD
Install-WindowsFeature -Name AD-Domain-Services -IncludeManagementTools
Install-ADDSForest -DomainName “oliver.local”
Then I waited for the system to reboot, after it did I made a new Domain Admin user called 'oliver.mustoe-adm' with the following commands:
# Wait for reboot, make adm user
$password = Read-Host -AsSecureString
New-ADUser -Name oliver.mustoe-adm -AccountPassword $password -Passwordneverexpires $true -Enabled $true
Add-ADGroupMember -Identity "Domain Admins" -Members oliver.mustoe-adm
Add-ADGroupMember -Identity "Enterprise Admins" -Members oliver.mustoe-adm
I would then re-login as my admin user. After creating that I setup DNS, added the primary zones, as well as adding a PTR record for the domain controller itself:
# Setup DNS and make records (is /24 because of windows)
Install-WindowsFeature DNS -IncludeManagementTools
Add-DnsServerPrimaryZone -NetworkID 172.16.200.0/24 -ReplicationScope “Domain”
Add-DnsServerPrimaryZone -NetworkID 172.16.150.0/24 -ReplicationScope “Domain”
Add-DnsServerResourceRecordPtr -Name "11" -ZoneName “200.16.172.in-addr.arpa” -AllowUpdateAny -AgeRecord -PtrDomainName "mgmt02-oliver.oliver.local."
(I would also, after the installing Wazuh, make a regular user. I do not believe that it would have affected the Wazuh install so I would have been fine to do it right after DNS:)
# Make regular user
$password = Read-Host -AsSecureString
New-ADUser -Name oliver.mustoe -AccountPassword $password -Passwordneverexpires $true -Enabled $true
All above commands in one block for copy paste ease:
# Setup AD
Install-WindowsFeature -Name AD-Domain-Services -IncludeManagementTools
Install-ADDSForest -DomainName “oliver.local”
# Wait for reboot, make adm user
$password = Read-Host -AsSecureString
New-ADUser -Name oliver.mustoe-adm -AccountPassword $password -Passwordneverexpires $true -Enabled $true
Add-ADGroupMember -Identity "Domain Admins" -Members oliver.mustoe-adm
Add-ADGroupMember -Identity "Enterprise Admins" -Members oliver.mustoe-adm
# Setup DNS and make records (is /24 because of windows)
Install-WindowsFeature DNS -IncludeManagementTools
Add-DnsServerPrimaryZone -NetworkID 172.16.200.0/24 -ReplicationScope “Domain”
Add-DnsServerPrimaryZone -NetworkID 172.16.150.0/24 -ReplicationScope “Domain”
Add-DnsServerResourceRecordPtr -Name "11" -ZoneName “200.16.172.in-addr.arpa” -AllowUpdateAny -AgeRecord -PtrDomainName "mgmt02-oliver.oliver.local."
# Make regular user
$password = Read-Host -AsSecureString
New-ADUser -Name oliver.mustoe -AccountPassword $password -Passwordneverexpires $true -Enabled $true
Adding PC to Active Directory:
To add wks01 to the domain, I first had to add the following firewall rules on fw-mgmt to allow the needed ports through the firewall with the following Vyos commands:
configure
set firewall name MGMT-to-LAN rule 30 action 'accept'
set firewall name MGMT-to-LAN rule 30 description 'Windows AD'
set firewall name MGMT-to-LAN rule 30 source address '172.16.200.11'
set firewall name MGMT-to-LAN rule 30 source port '53,88,135,137-138,389,445,464,636,3268-3269,1024-65535'
set firewall name MGMT-to-LAN rule 30 protocol 'tcp_udp'
set firewall name LAN-to-MGMT rule 50 action 'accept'
set firewall name LAN-to-MGMT rule 50 description 'Windows AD'
set firewall name LAN-to-MGMT rule 50 destination address '172.16.200.11'
set firewall name LAN-to-MGMT rule 50 destination port '53,88,135,137-138,389,445,464,636,3268-3269,1024-65535'
set firewall name LAN-to-MGMT rule 50 protocol 'tcp_udp'
commit
save
| Port | Description |
|---|---|
| 53 | DNS |
| 88 | Kerberos |
| 135 | RPC |
| 137-138 | Authentication |
| 389 | LDAP |
| 445 | Replication and login services |
| 464 | Kerberos password |
| 636 | LDAP |
| 3268-3269 | Active Directory port |
| 1024-65535 | RPC for LSA, SAM, NetLogon |
Sources:
- https://cloudinfrastructureservices.co.uk/active-directory-ports/
- https://documentation.sailpoint.com/connectors/iqservice/help/integrating_iqservice_admin/ports_used_with_ad.html
- https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/config-firewall-for-ad-domains-and-trusts
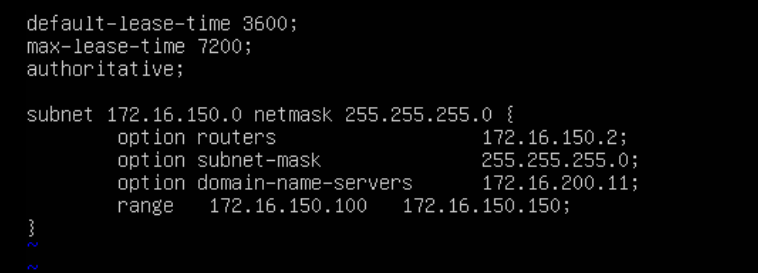
Here I also could have set the DHCP configuration (/etc/dhcp/dhcpd.conf) on my DHCP server like the following (in my installation I did this post-domain adding, but it makes more sense to place the configuration here):
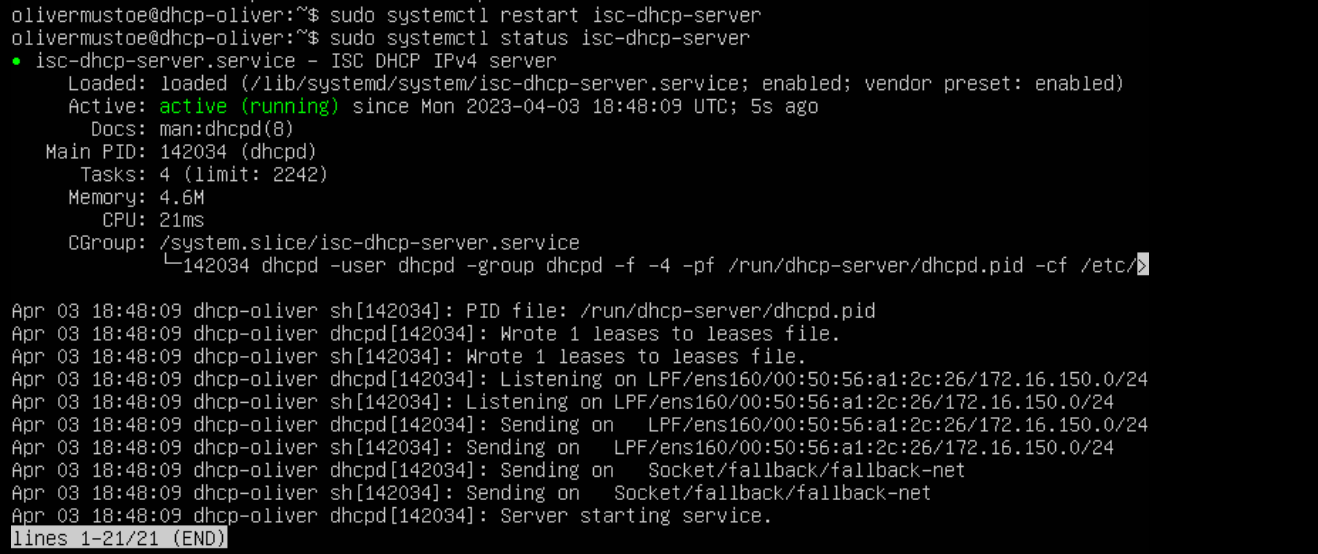
And I restarted DHCP with sudo systemctl restart isc-dhcp-server:
Then I added wks01 with the following (also need to change the DNS server to 172.16.200.11, wks01 if DHCP config wasn't changed and the lease renewed):
Add-Computer -Domain “oliver.local” -restart
Wazuh agent on Windows installation
I then added a Wazuh group for windows (using my Wazuh reference):
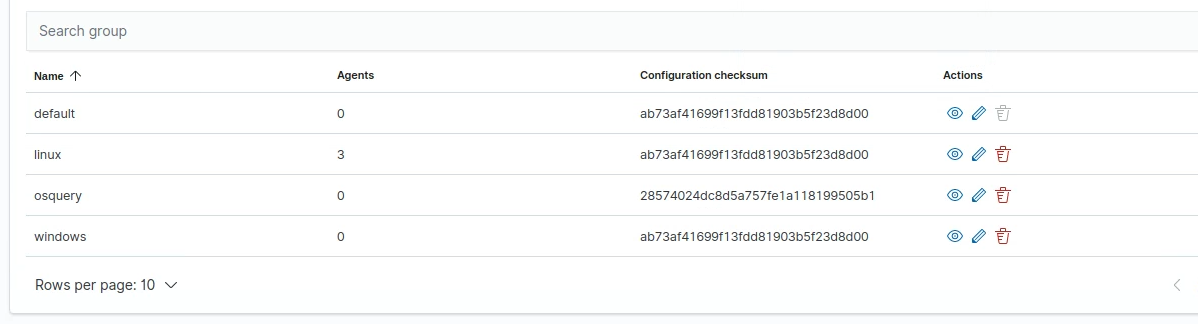
Then went to agents and got the needed commands selecting Windows and the Windows group like the following (assigned sections 1-3, 4 and 5, not seen below, are the commands listed later in this page) (see Wazuh reference):
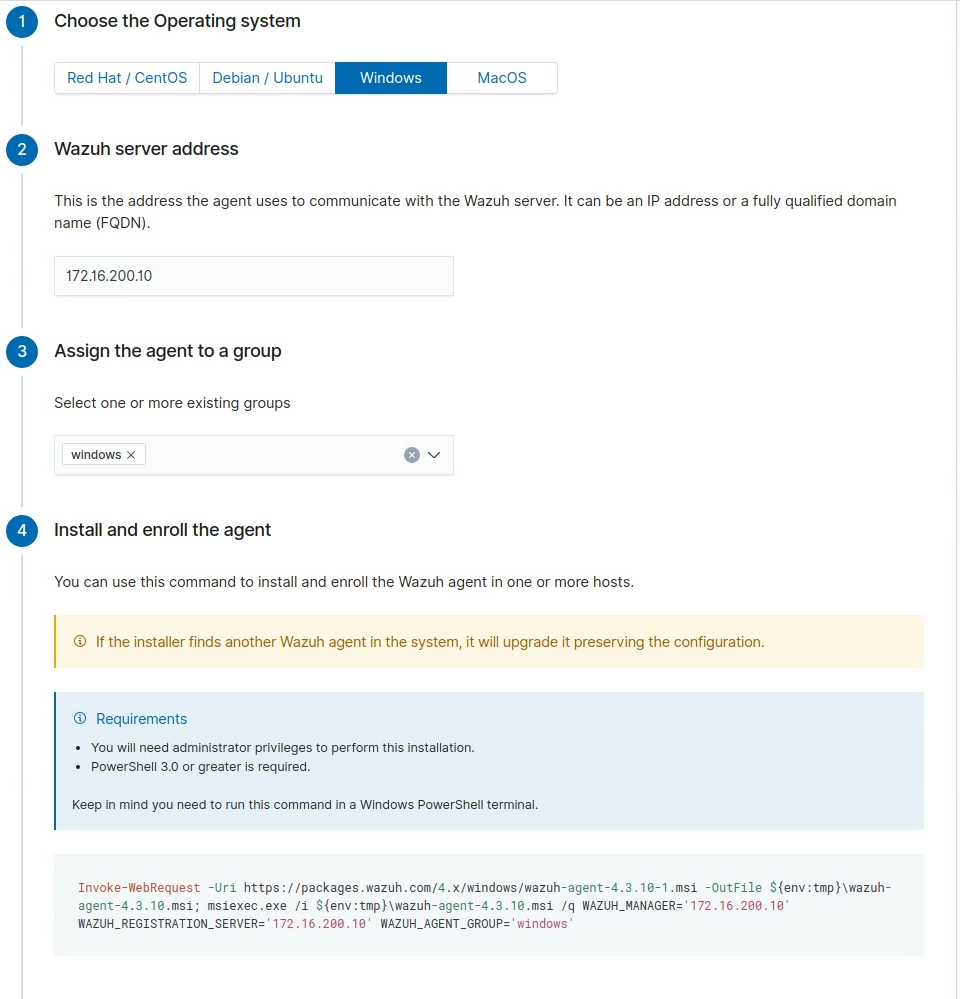
Then I SSH’d into wks01 from mgmt01 and ran the below command in powershell to install the agent:
Invoke-WebRequest -Uri https://packages.wazuh.com/4.x/windows/wazuh-agent-4.3.10-1.msi -OutFile ${env:tmp}\wazuh-agent-4.3.10.msi; msiexec.exe /i ${env:tmp}\wazuh-agent-4.3.10.msi /q WAZUH_MANAGER='172.16.200.10' WAZUH_REGISTRATION_SERVER='172.16.200.10' WAZUH_AGENT_GROUP='windows'
Then I ran the following in an administrative powershell session:
NET START WazuhSvc
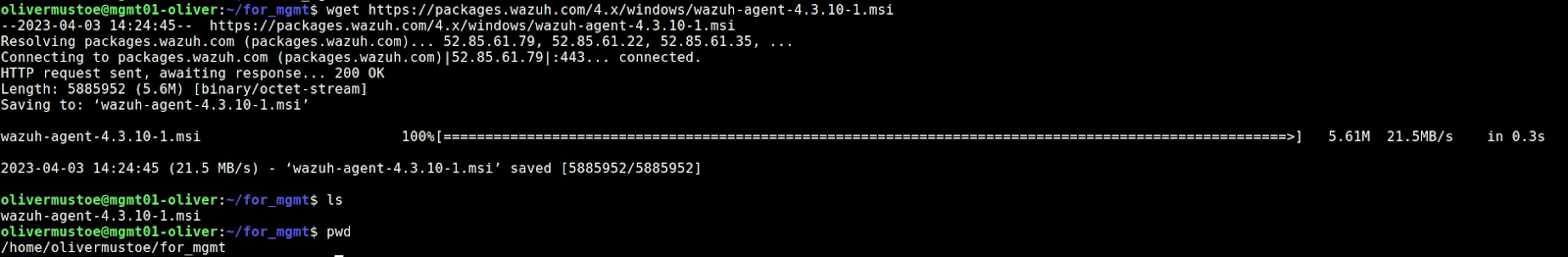
Then on mgmt01, downloaded the Windows Wazuh agent msi:
mkdir for_mgmt
cd for_mgmt
wget
https://packages.wazuh.com/4.x/windows/wazuh-agent-4.3.10-1.msi
And ran the following commands on mgmt02 to download the msi with sftp and install the Wazuh agent (powershell, admin shell):
sftp [email protected]:/home/olivermustoe/for_mgmt/wazuh-agent-4.3.10-1.msi ${env:tmp}\wazuh-agent-4.3.10.msi
msiexec.exe /i ${env:tmp}\wazuh-agent-4.3.10.msi /q WAZUH_MANAGER='172.16.200.10' WAZUH_REGISTRATION_SERVER='172.16.200.10' WAZUH_AGENT_GROUP='windows
NET START WazuhSvc
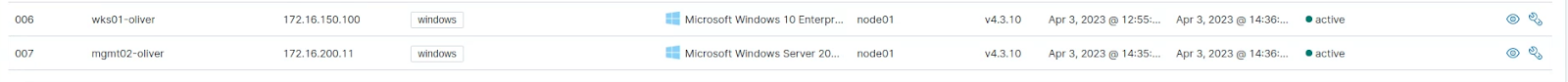
Agents shown in Wazuh agents panel:
Troubleshooting:
- After adding wks1 to the domain with Powershell, rebooting, the computer gave me an error of “The Security Database on the Server Does Not Have a Computer Account for This Workstation Trust Relationship:” I fixed by removing wks01 from ad with `Remove-ADComputer wks01-oliver’, adding the ports 1024-65535 to the firewall, loading a snapshot of wks01, and re-adding it to the domain. I believe this to be an RPC issue.