B. Authorise the service account domain wide - NoSubstitute/userDelegationWebApp GitHub Wiki
Before the script is allowed to do anything we have to add it to the domain wide section in API Access Control
- With your superadmin account open API Access Control / Domain Wide Delegation Only superadmin can authorise domain wide access.
- In step 6 we copied the unique ID of the service account. We need that number value now.
- Click Add new.
- Paste the unique ID in the field for Client ID.
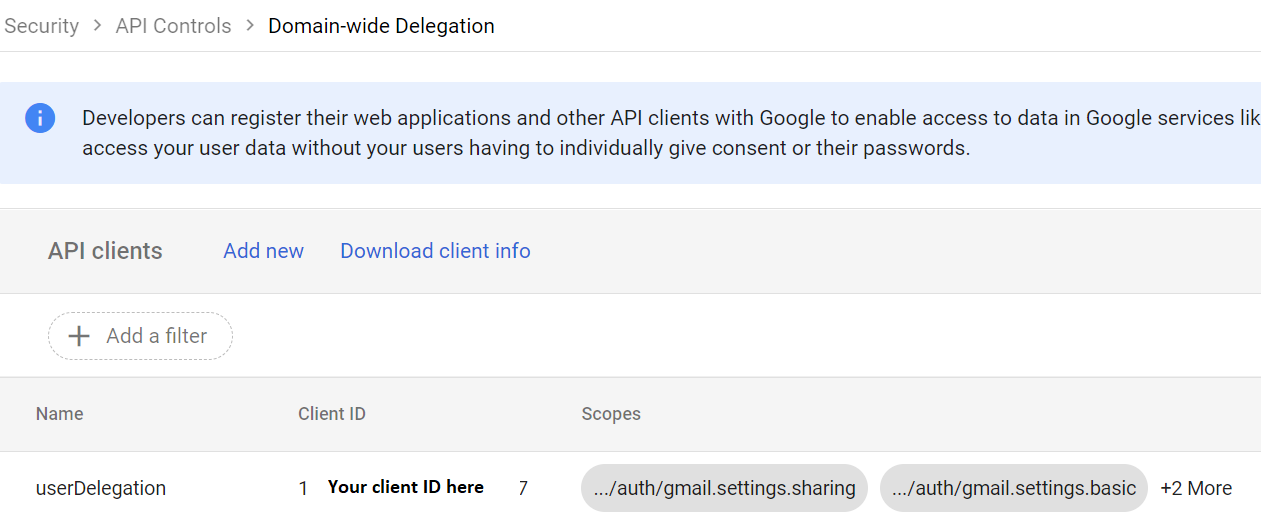
- Paste this comma separated line of scopes into the field of OAuth scopes.
https://www.googleapis.com/auth/gmail.settings.sharing,https://www.googleapis.com/auth/gmail.settings.basic,https://www.googleapis.com/auth/userinfo.profile,https://www.googleapis.com/auth/userinfo.email - AUTHORIZE
- The window should close and show you the list of domain wide authorised client ids. Your userDelegation should be listed there.
You can now close everything but the Apps Script editor.
Add a reference to the delegated admin and password to restrict access
On line 2 of the file code.gs there are two settings which restricts access to the web app.
if (Session.getActiveUser().getEmail() == "[email protected]" && e.parameter.key == "SomePasswordHere") {
Replace [email protected] with the email of user you are giving this web app to, and also add a password to be provided in the URL of the web app.
Only that unique user with that password will be able to access the web app. The security measure is both because there is currently no limitation on which email accounts the user is allowed to delegate, but also that no unauthorised user should gain access to the web app.
Remember to adjust the user and password if/when you create more deployments of this web apps for separate admins.