ICMP - LogeshVel/learning_resources GitHub Wiki
The ICMP packet does not have source and destination port numbers because it was designed to communicate network-layer information between hosts and routers, not between application layer processes.
- ICMP is Layer 3 protocol (IP layer)



Types
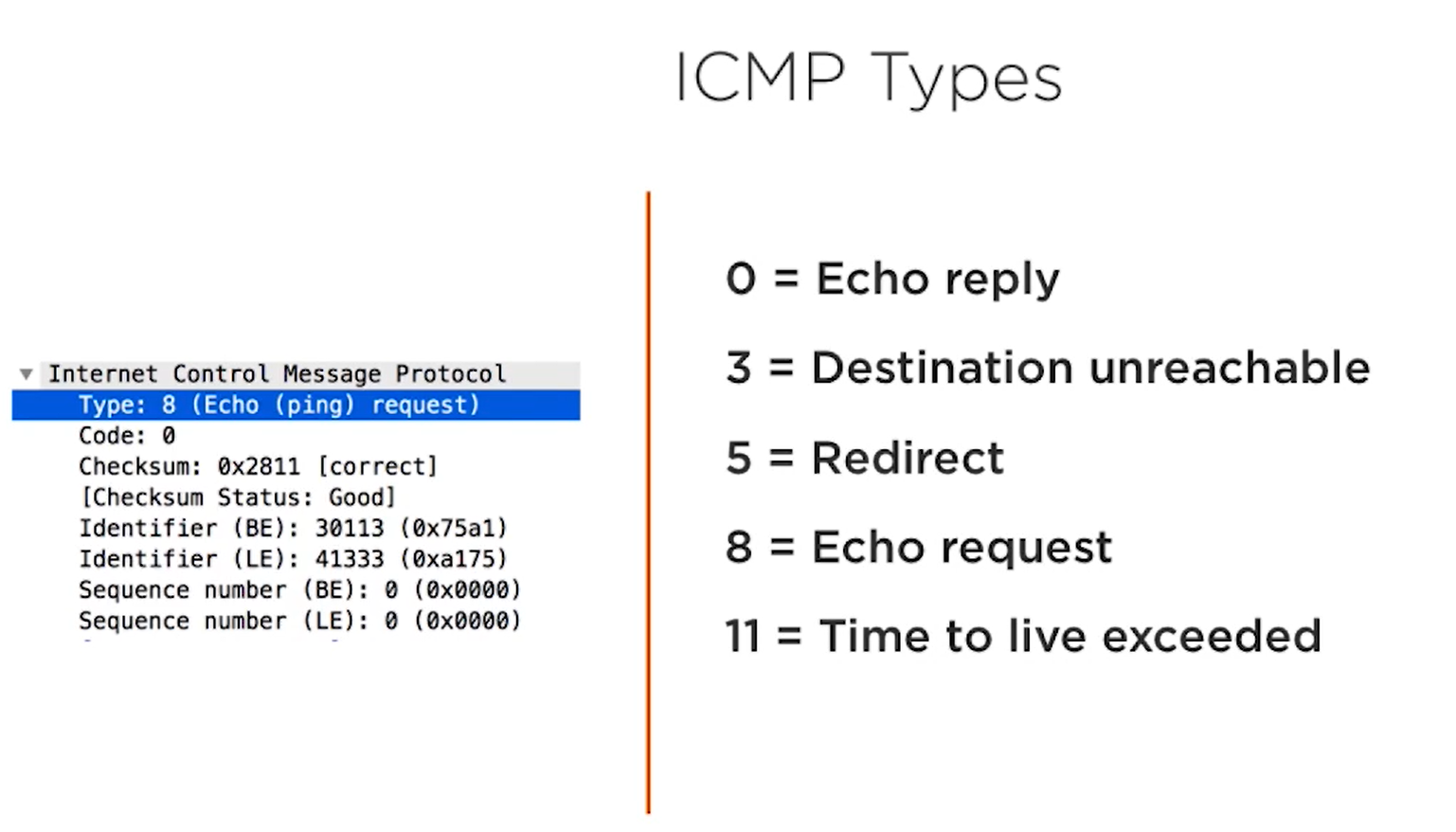
Codes
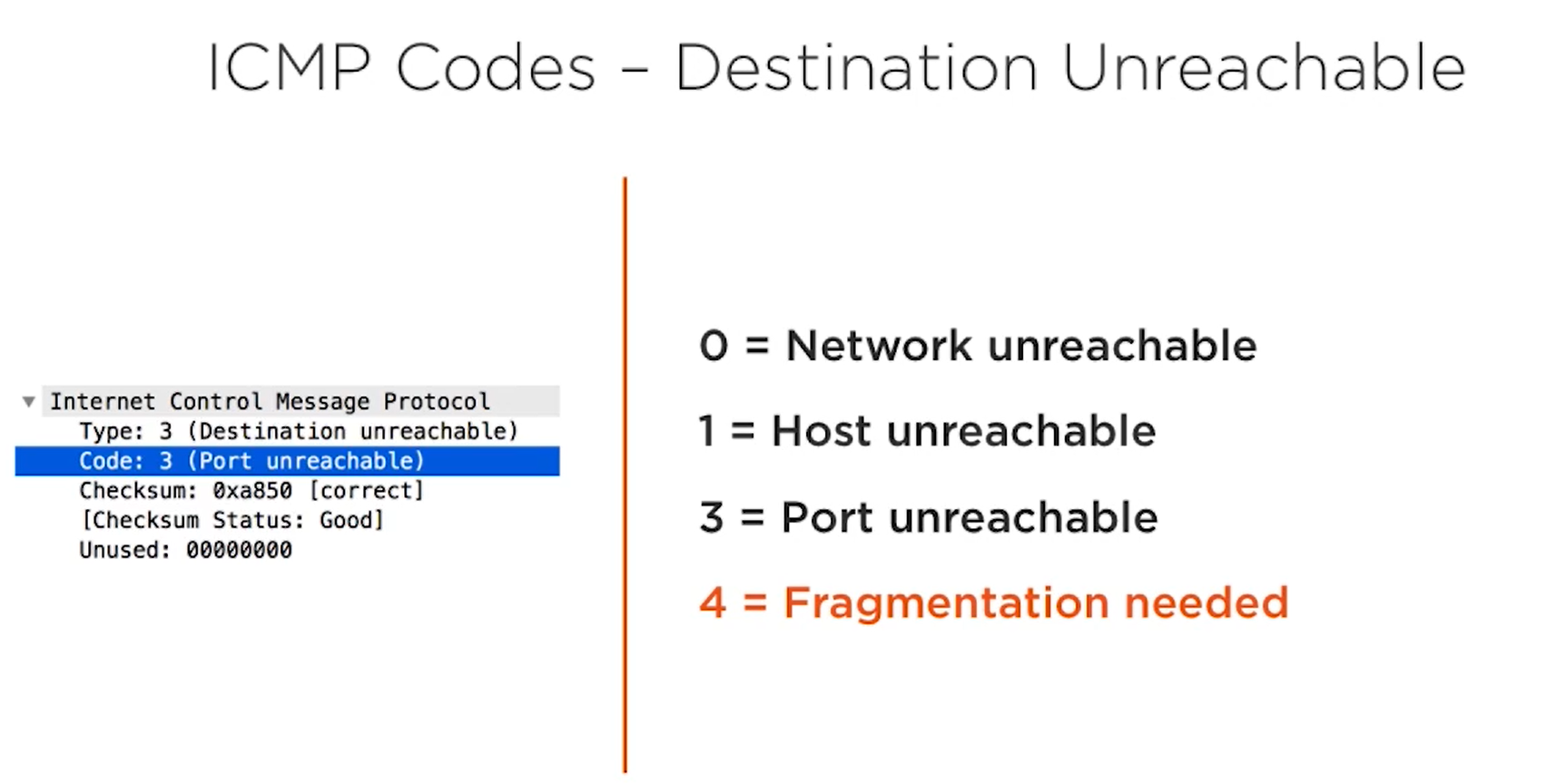



Destination unreachable
Network unreachable means, there is no route to the target network itself. (ex: 10.10.10.0/24 network has no route)
Host unreachable - the network is reachable and able to get into the network but in that network we are not able to find the target Host. (seems the host is not reachable. Ex: 10.10.10.10)
Port unreachable - we could find the network, and get into the host but the host transport layer port is not available.
Fragmentation needed - this means the packet size exceeds the MTU but when the router tries to fragement it, router saws that the Don't Fragment bit is set so the router replies with the Destination unreachable with the Fragementation needed message.
PCAP
ICMP Echo-request
-
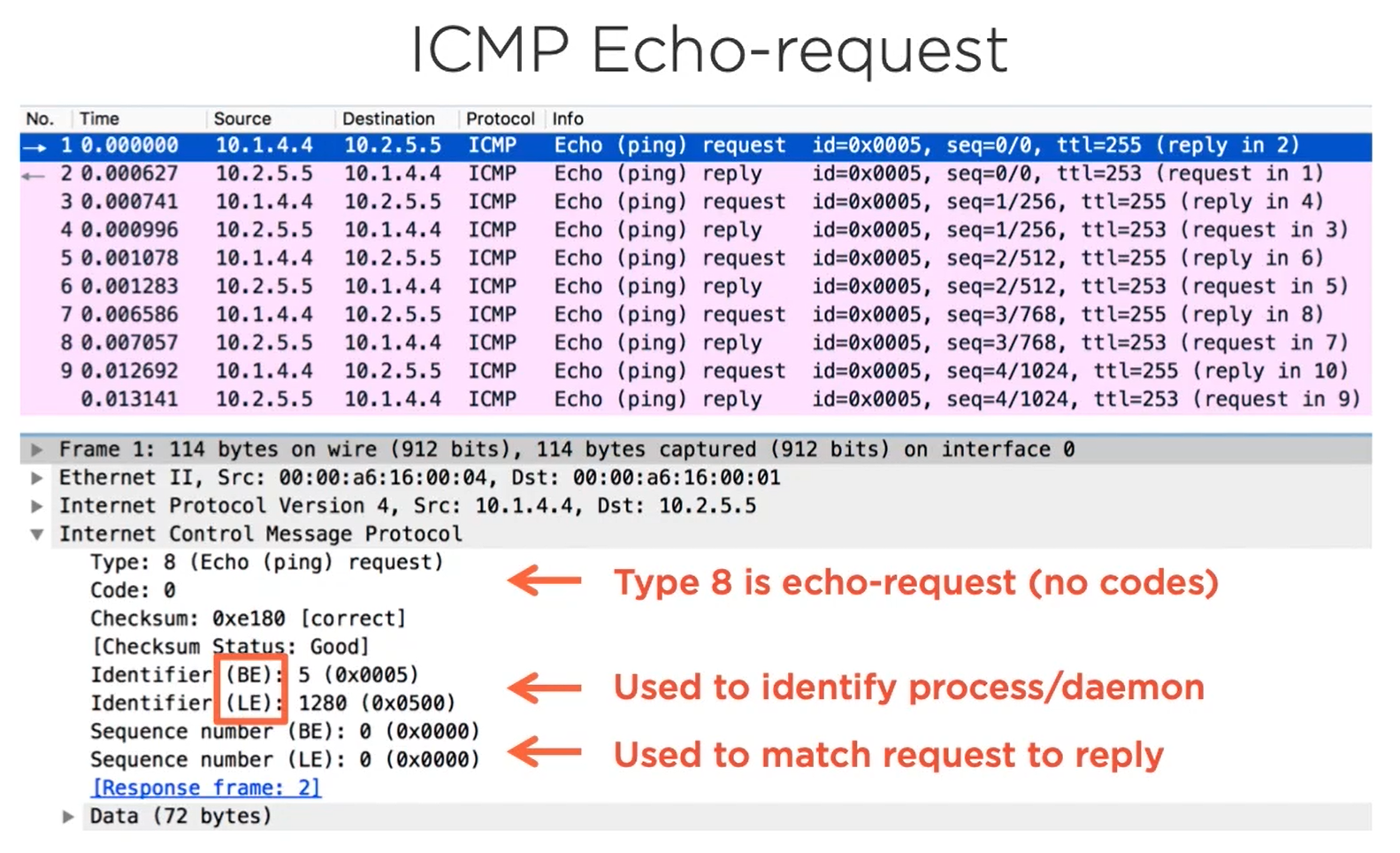
The Identifier is often used by operating systems to identify the process or daemon that originated the traffic. Suppose you and I were both logged into the client. Together we would each have our own shell process. So if we pinged the remote server at the same time, our identifers would be different. This is how the operating system differenciates the replies to their original requests at a process level.
-
The sequence number serves a similar purpose as the identifier, except that it differenciates the replies to their original requests at a packet level once the identifier is matched. To specify the process that originated the Echo request, the sequence number measures which exact echo request, received the replies in which did not. Some networks may deliver packets out of order, which is why this field is important.
-
I need to briefly mention what this BE, LE monkey business is all about. B. E and LE refer to the endians of a machine, BE meaning Big endian and LE, meaning **Little endian **. Endian is the order in which bytes are stored in the CPU. Big Endian stores more significant bytes first, that is to the left. Little Endian stores the most significant bytes last to the right. The Different CPU hardware uses different formats.
Endians
Big Endian - Starts placing the values from the MSB
Little Endian - Starts placing the values from the LSB


ICMP Echo reply

If you are interested, here is a full list with all ICMP codes and types.
Example
Echo request and reply


Echo request and reply type of ICMP has no codes
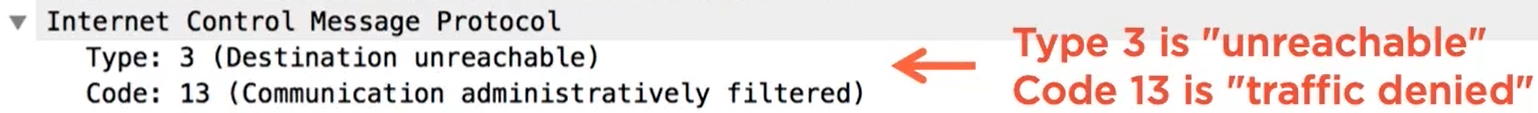
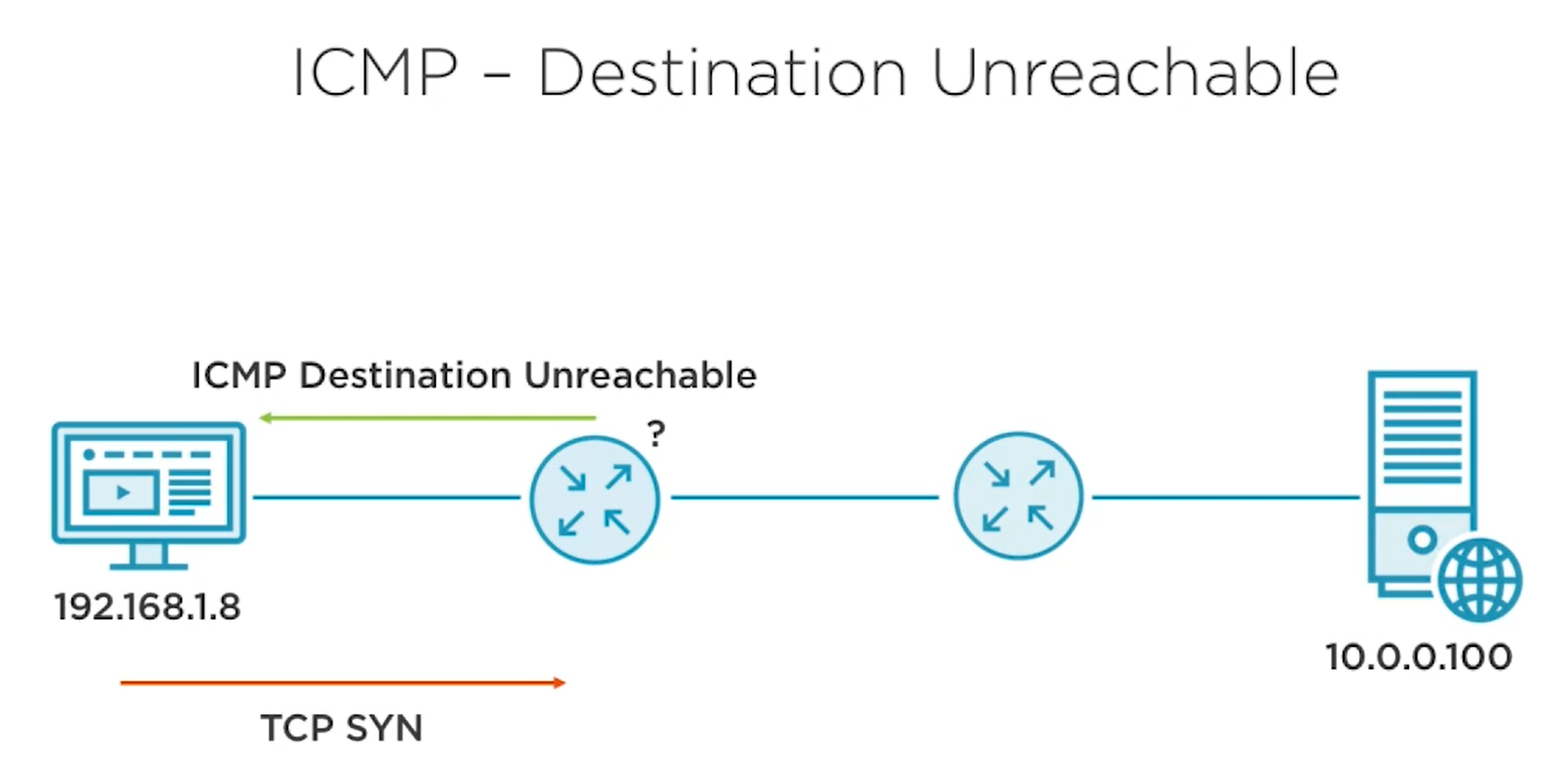
Destination Unreachable


Traceroute
It traces the route from the source to the destination.
Traceroute works by using the IP TTL. Starting from 1 it increases the TTL to traverse the network. It uses the UDP port 33434 and also increaments this value by one for the next time
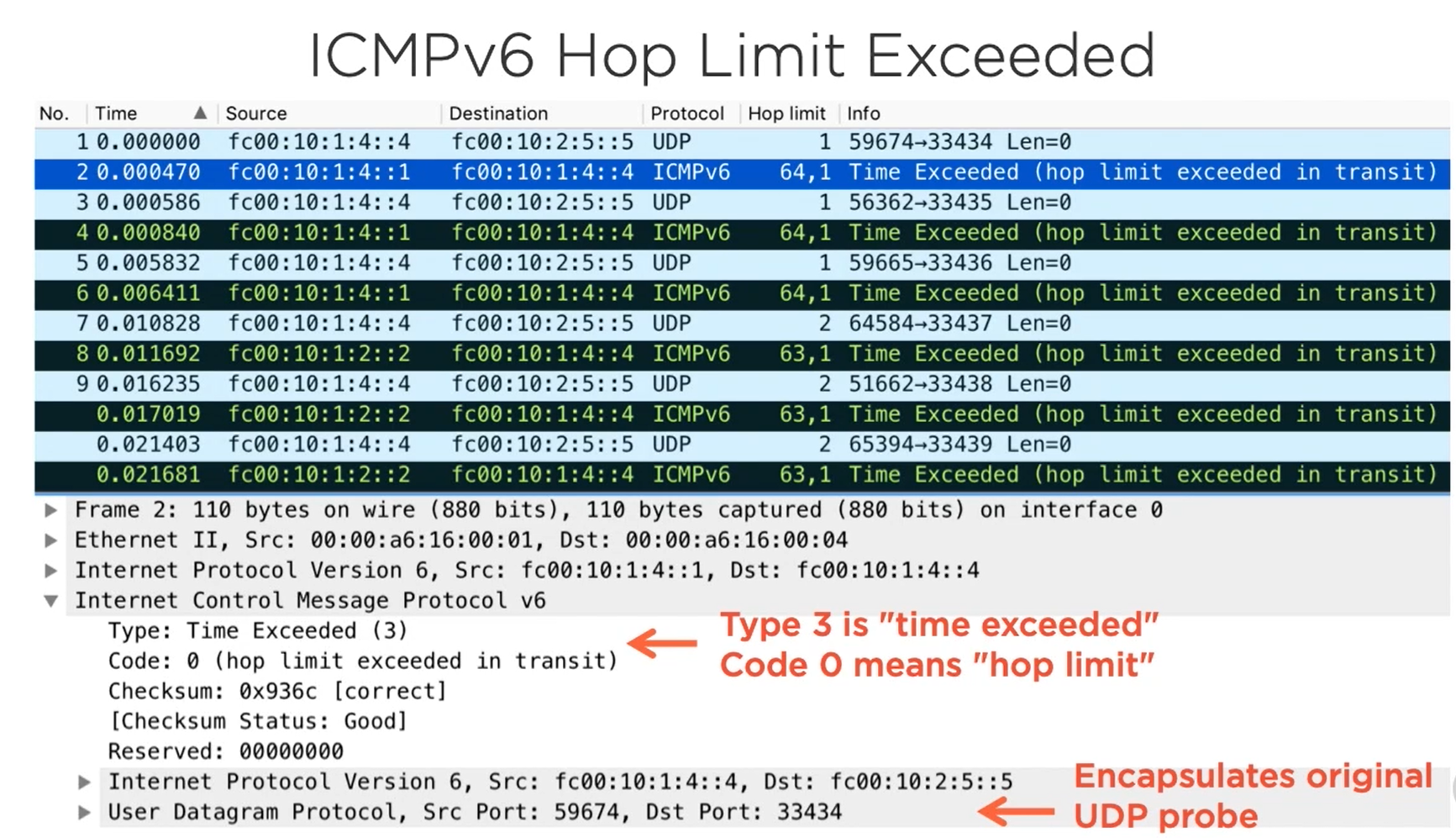
Traceroute uses UDP port with no Application data (payload) and gets the ICMP message back(either TTL execeeded from the intermediate host or port unreachable from the target host - if target is reachable) and notes the host in the table
-
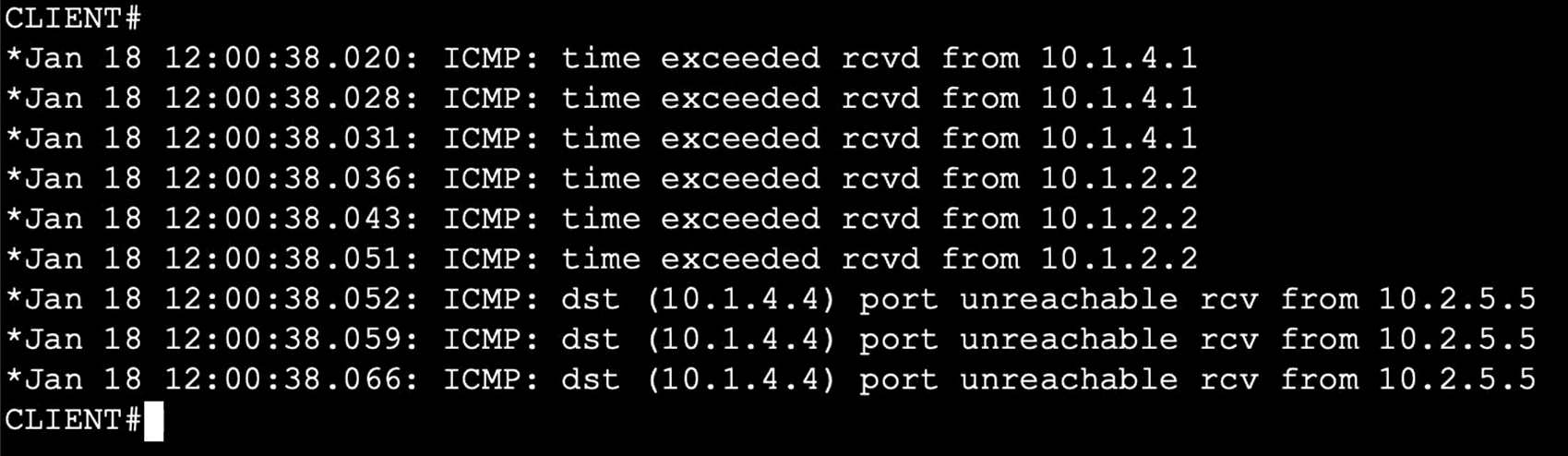
First sends with the dest UDP port 33434 and TTL as 1. The Default gateway will drop that packet and sends the ICMP TTL exceeded msg. Now our machine makes the note of that 1st host from the rply packet.
-
Now, increments the TTL and port by one.(TTL 2, Port 33435). Now the second host will drop the pkt and sends the TTL exceeded msg. Our machine makes note of the second host from the reply packet.
-
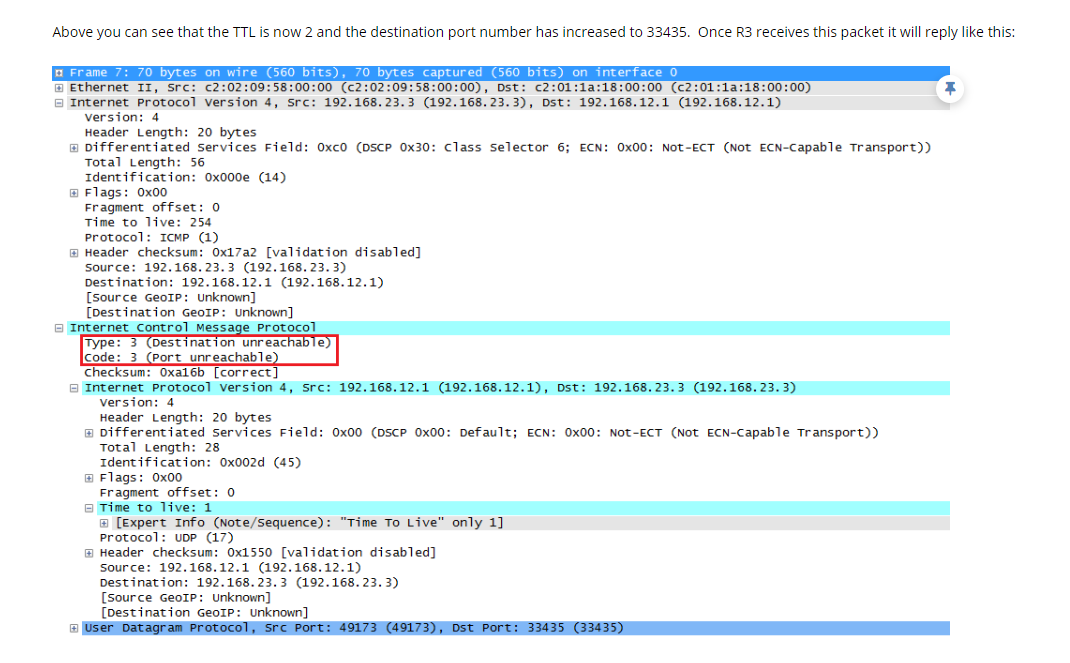
By doing so.. at the end the TTL value is enough to hit the destination, if the destination is reachable then the dest host will try to read the packet and it saws the Dest port and it will reply with the Port unreachable (since it won't listen on that port). Once getting the reply packet Traceroute cames to know that the destination host is reachable but the port is closed.





ICMP debug logs
Note: this client is Cisco IOS router

UDP traceroute probe pcap

TTL exceeded pcap
We can clearly see that the ICMP packet just cuts and paste the corresponding UDP probe packet in the reply(encapsulates).

Traceroute Port-unreachable


Fragmentation

-
If a large packet with DF set to zero arrives at a router that has an egress link with an empty you smaller than the packet, the router will break the pack it up into fragments. Since each fragment is a new IP packet, the target host has to **reassemble **them once they're all received. The fragments have identifiers, known as **offsets **that specify their sequence for reassembly.
-
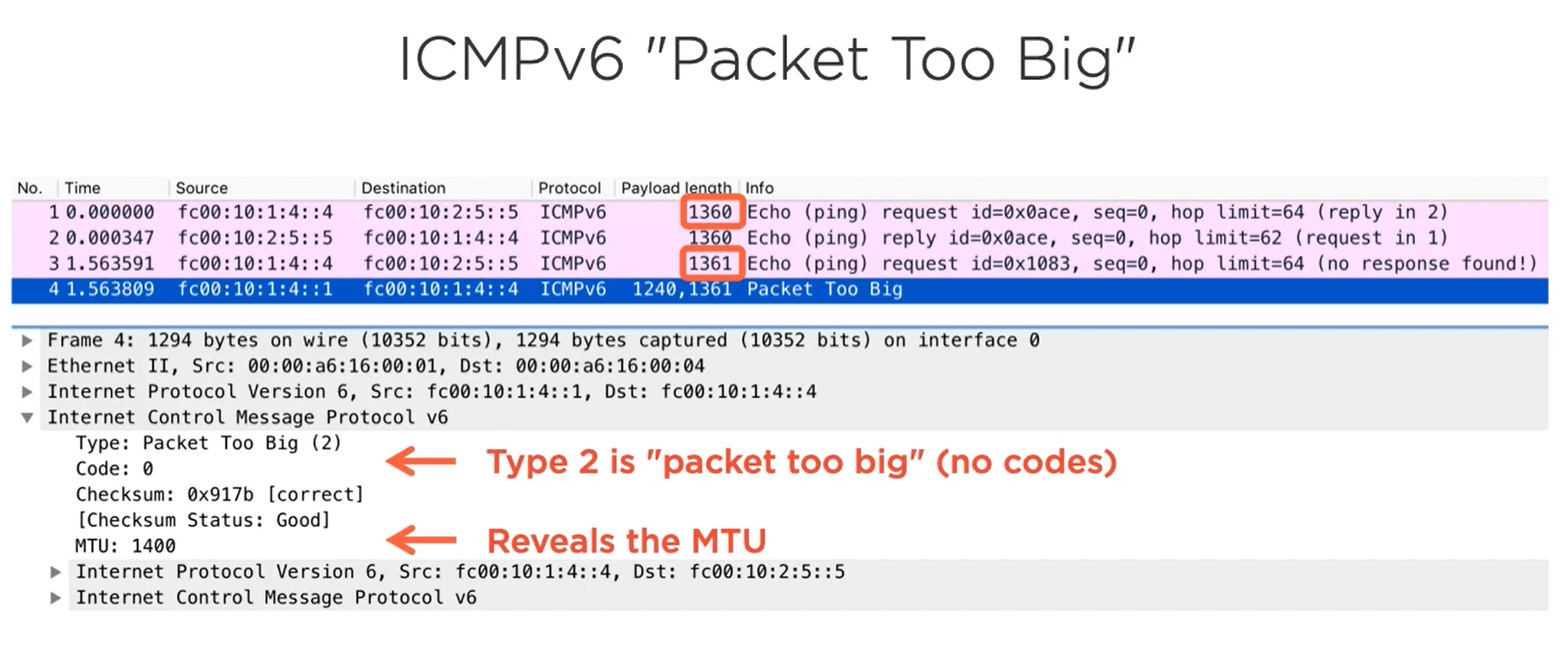
Now imagine that same large packet arrives at the router with DF set to one. The router is no longer allowed to fragment this packet. The router will do one of two things. It could send a packet to big unreachable back to the sender, which is usually the preferred behavior. This packet indicates that the packet was too large and fragmentation was required but was disallowed because DF was set toe one in plain English. The packet says Look, I want to route this packet but I can't fit it over my link and you specifically told me not to break it up. The alternative behavior is for the router to silently discard the packet which happens when ICMP unreachable Sze are filtered from the network

ping with mtu(mtu discovery)
we can use the below command to find whats the MTU size along the path to the destination. If we send large MTU size then it will timeout so we have to try different scenarios to find the exact MTU of the Path to the destination.
This method is called ping bracketing. Try to guess the value from some value. If the ping success in that value then add some even value to the MTU if again sucess repeat the step. if the ping fails reduce the MTU to half from the added even value.
Ex: 1500 default MTU starting from here.
If ping sucess with 1500 then i will add 100 to it. packet size is 1600 if ping failed, reduce the size to half of the added value now size is 1550. try to ping success? or not? repeat the step.
ping sweep(mtu discovery)
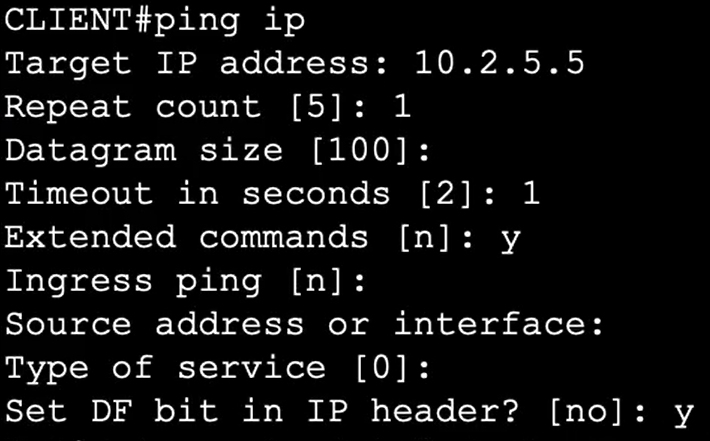
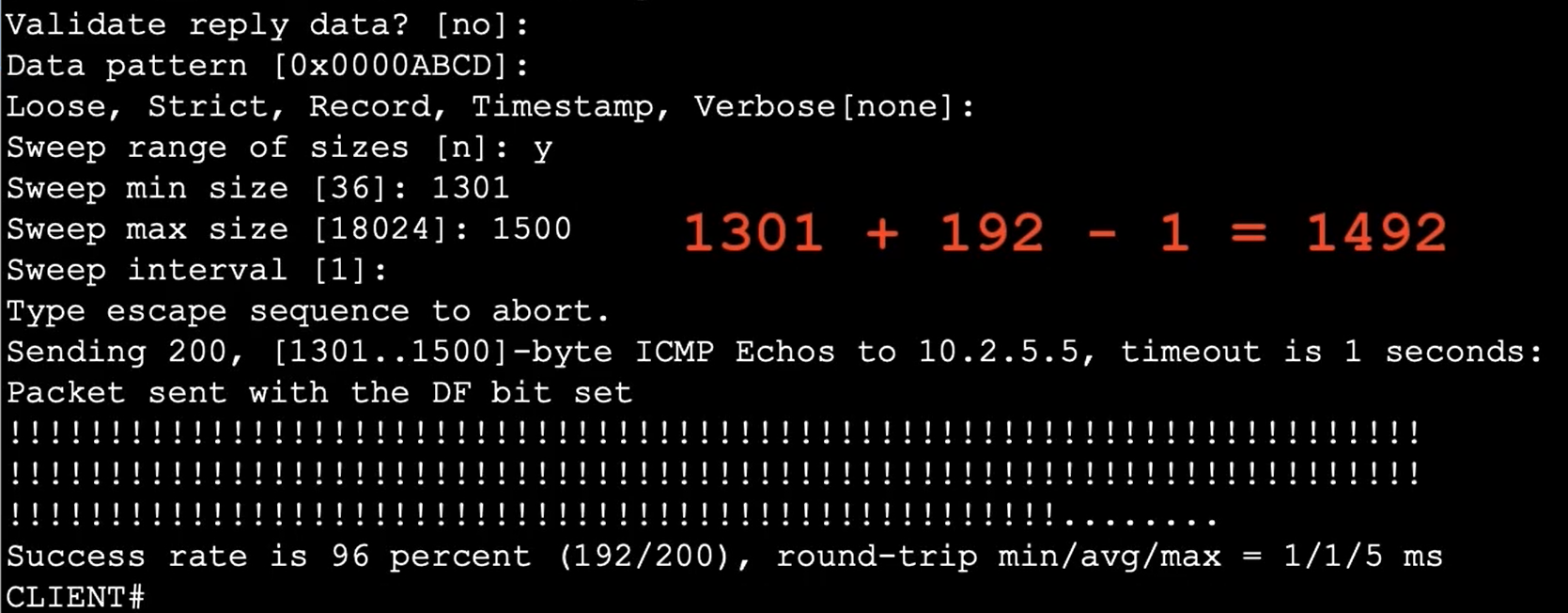
Here in the sweep each time we have increased our size from min to max to find where the ping is failed. So we came to know that the the exact MTU size.
- 1492 is the MTU size
Cross verifying using the Ping bracketing
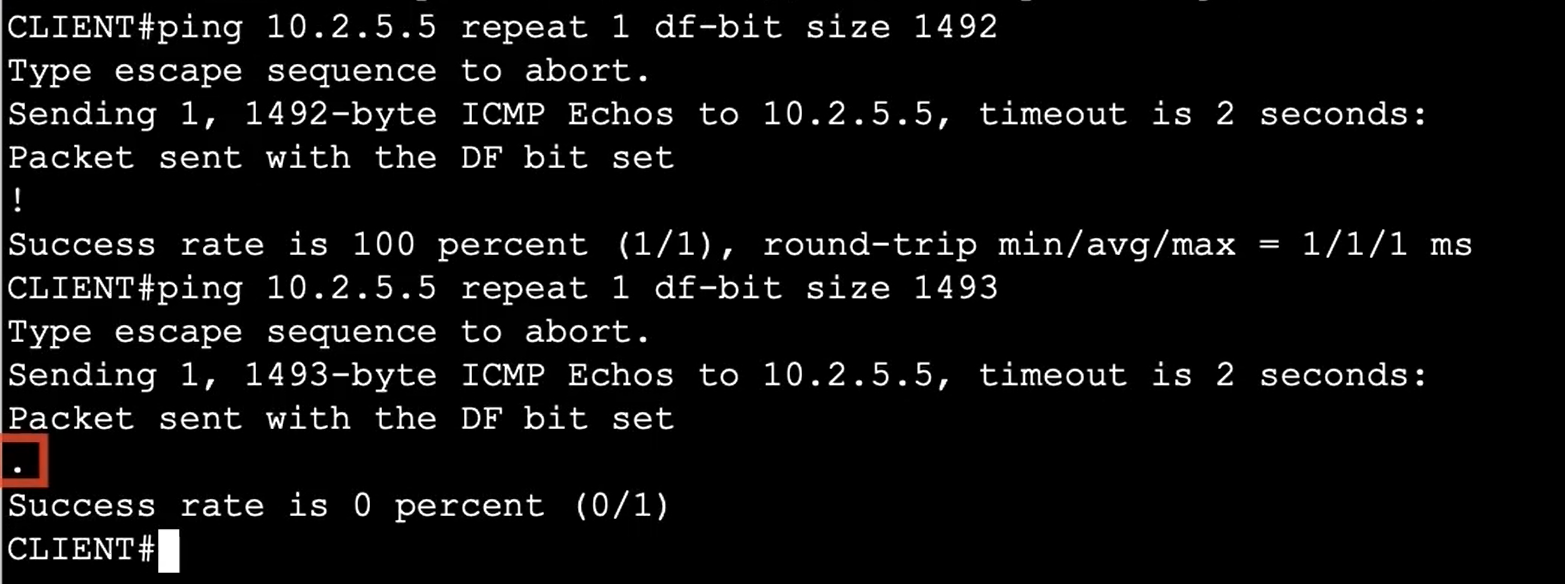
traceroute - admin prohibited
If the firewall drops our UDP probe packet then we could see this. But if the firewall silently dropped our packet (without notifiying us) then we only see the * * * which is timeout.

ICMPv6
IPv6 Neighbour Discovery - ND
NS - Neighbor Solicitation
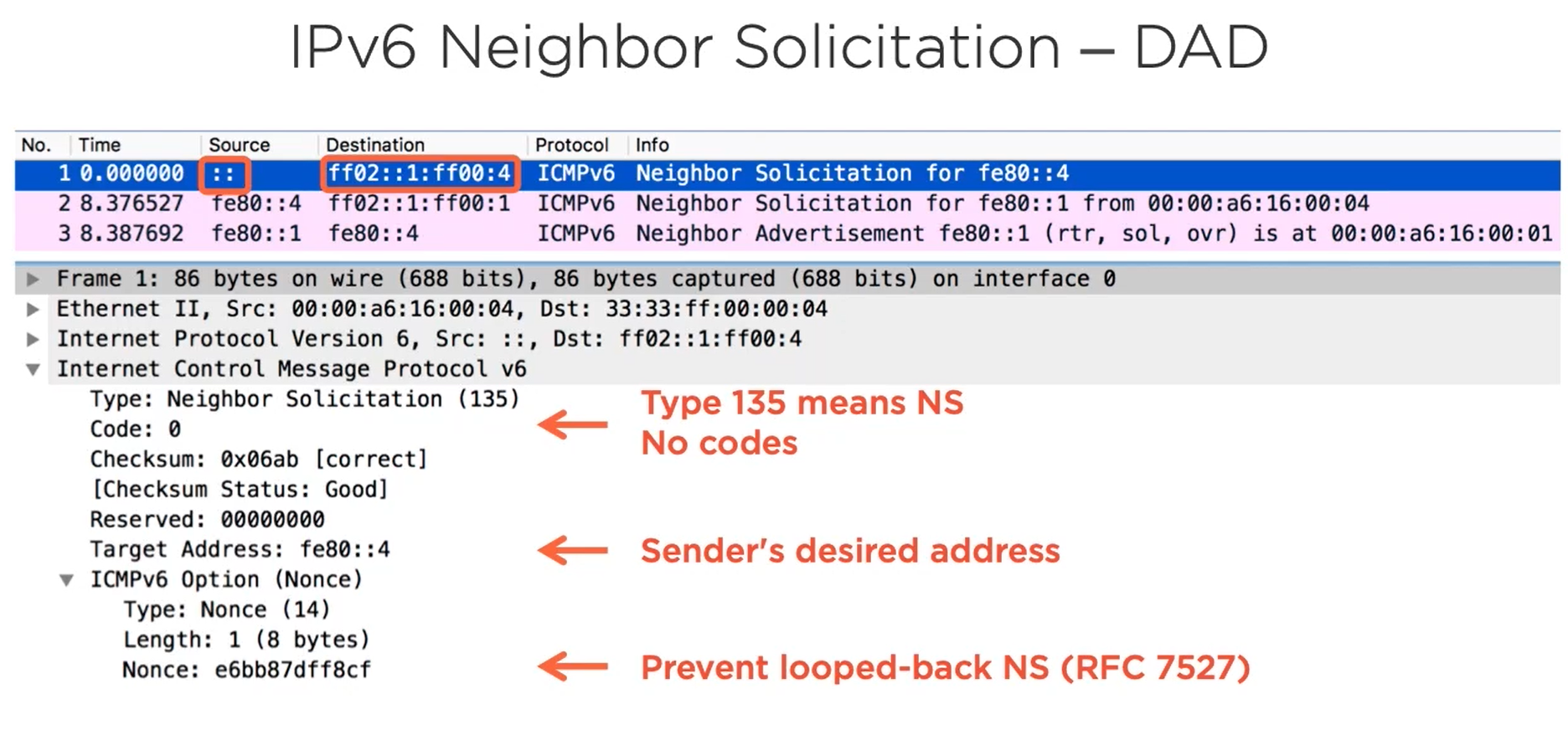
ND is just like IPv4 ARP. The Machine comesup and it assigns its own Link Local IPv6 address and checks for the duplicate in the network. It will ask the network anyone having this IPv6 Linklocal address.. if no one replies for that request then it assumes it is unique else if someone sends response then the machine will know its the duplicate it will comeup with another IP.
This process is known as Duplicate Address Detection (DAD)

Now to know the MAC address of the client whose IP is know the exact ARP happens in the name of NS.
We will get the reply as NA(Neighbor Advertisement)

Non Link Local communication
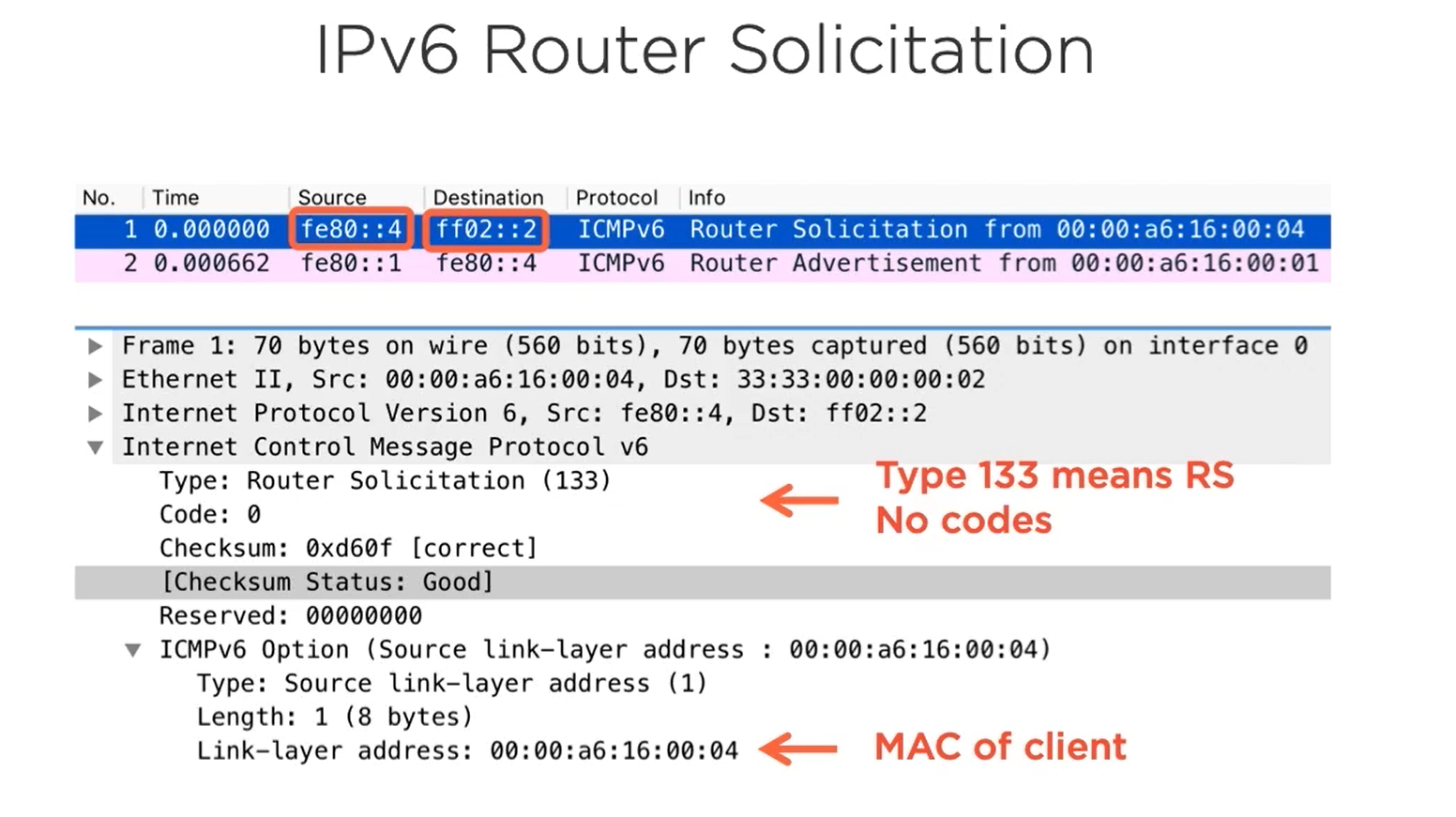
RS- Router Solicitation
RA - Router Advertisement
Now for the IPv6 clients to communicate to the Server that resides in another network, it needs to find whether its default gateway supports IPv6 commnication it will send the ICMPv6 RS that asks for the Routers that support the IPv6.
The Routers responds with the ICMPv6 RA.
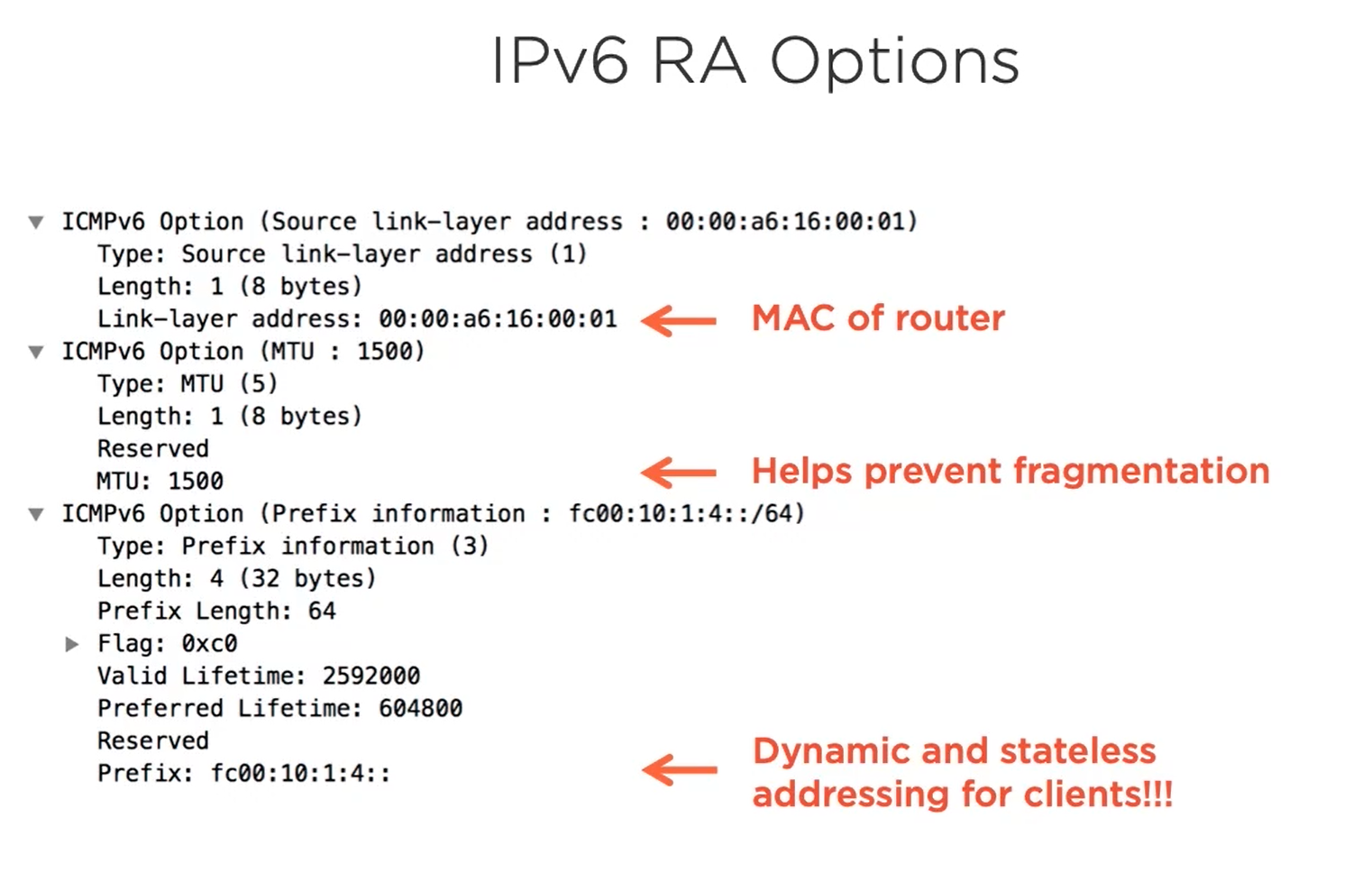
And the machine derives its IPv6 using SLAAC and then sends the data.
The RS is needed when hosts are trying to perform slack to dynamically determine their route.
More about IPv6 in future i will have separate page for that

PCAP
NS - DAD
NS - ND
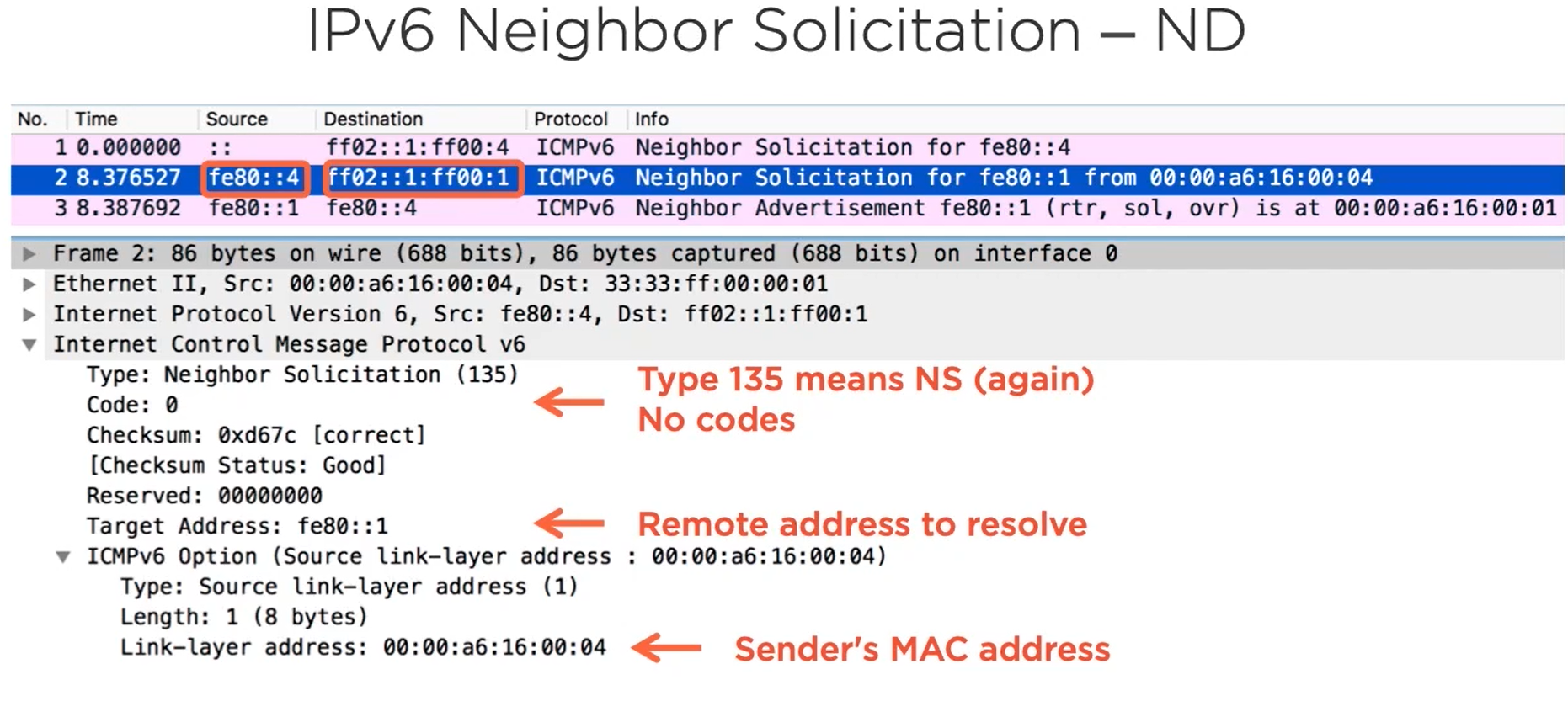
NA

RS
ff02::2 is a router multicast group ip
RA

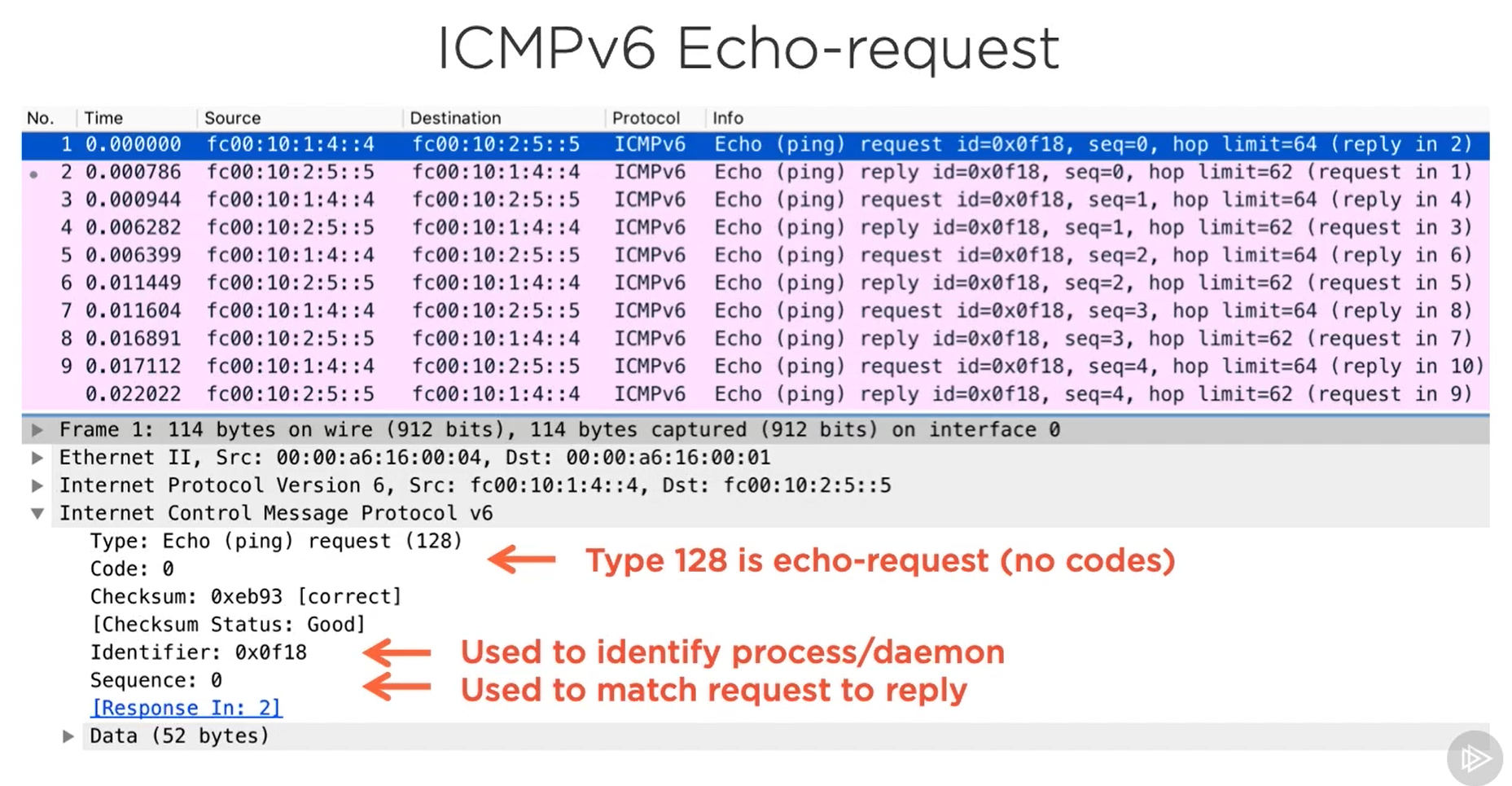
IPv6 Ping
same process as IPv4

IPv6 Traceroute
Same process as the IPv4
UDP Probe
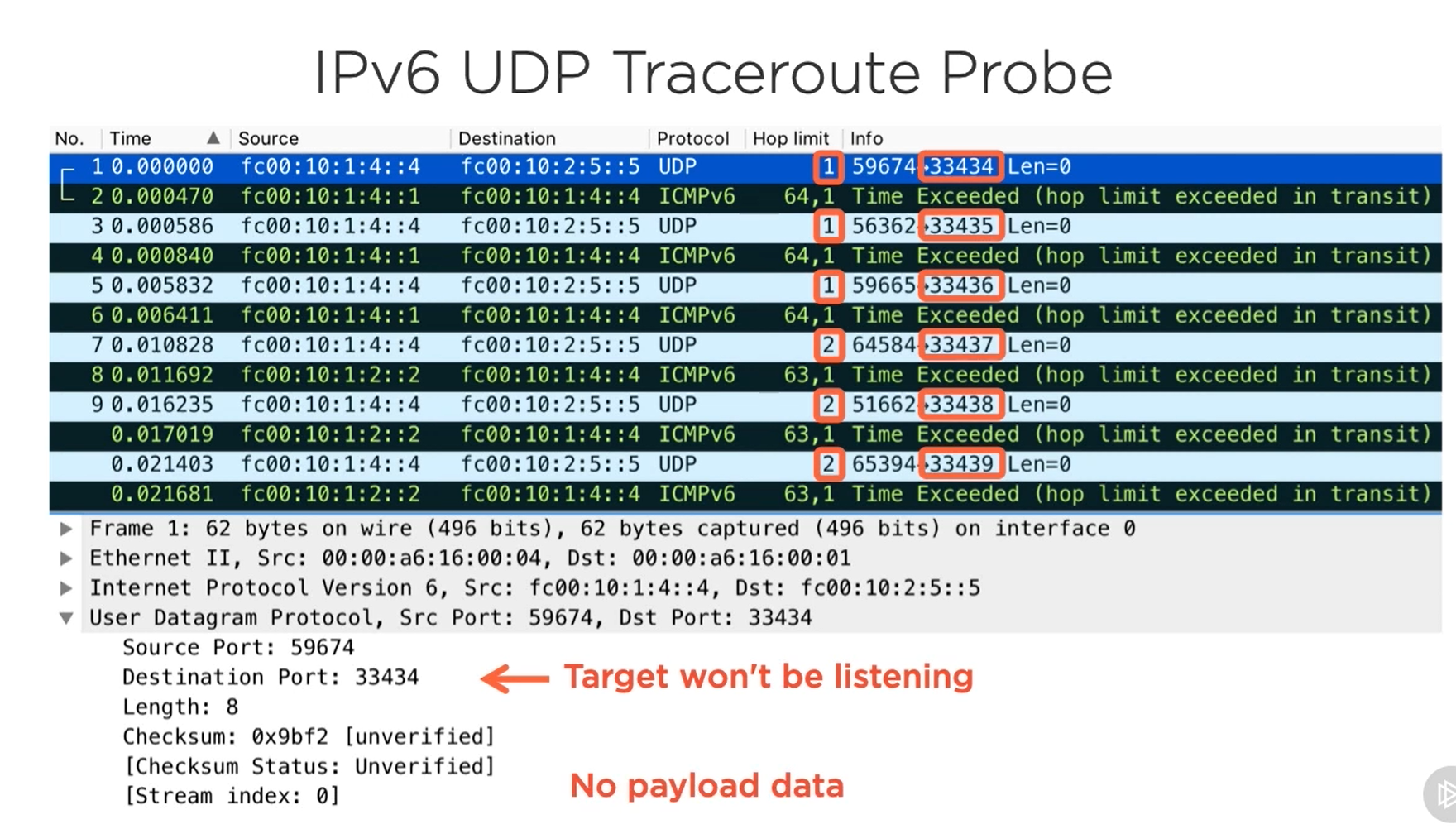
HOP Limit exceeded
Port Unreachable

IPv6 Fragmentation

a note on the wireshark column titled Payload Length. In IPv4 the length field of the packet measures the length of the whole IPv4 packet, including the I P header, which is typically 20 bytes.
In IPv6 the length field only includes the payload size, so we need to add the typical 40 bytes IPv6 header size to see the actual IPv6 packets size.
The first set of ICMPv6 ping packets haven't IPv6 packets size of 1400 which is 1360 plus 40.
The next ICMPv6 echo request has a total IPv6 packet size of 1401 which is slightly too large to fit through this demo network.
ICMPv6 Admin prohibited
