Wireless Security - LogeshVel/802.11 GitHub Wiki
4 way handshake
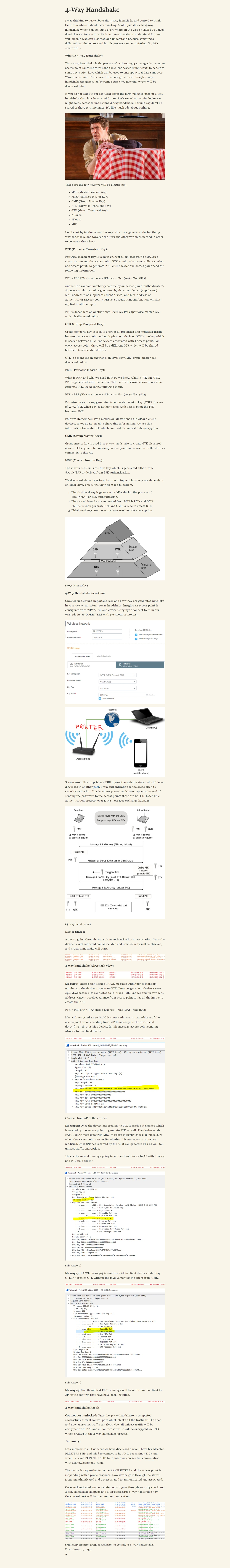

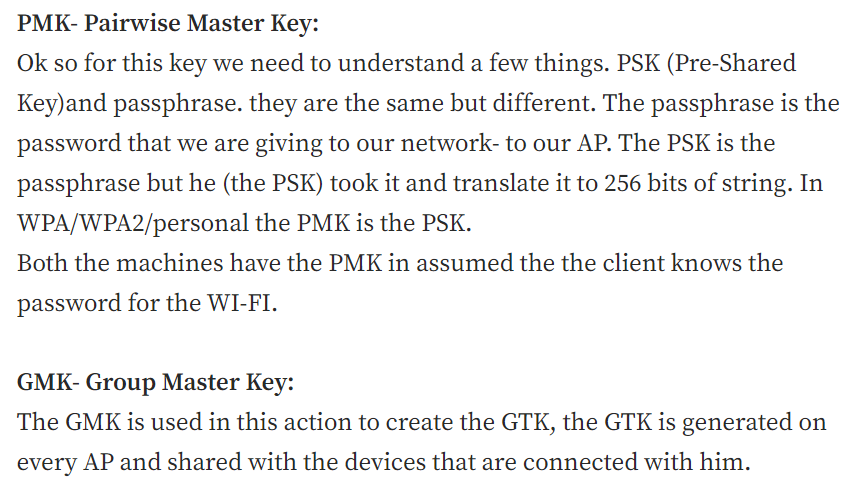

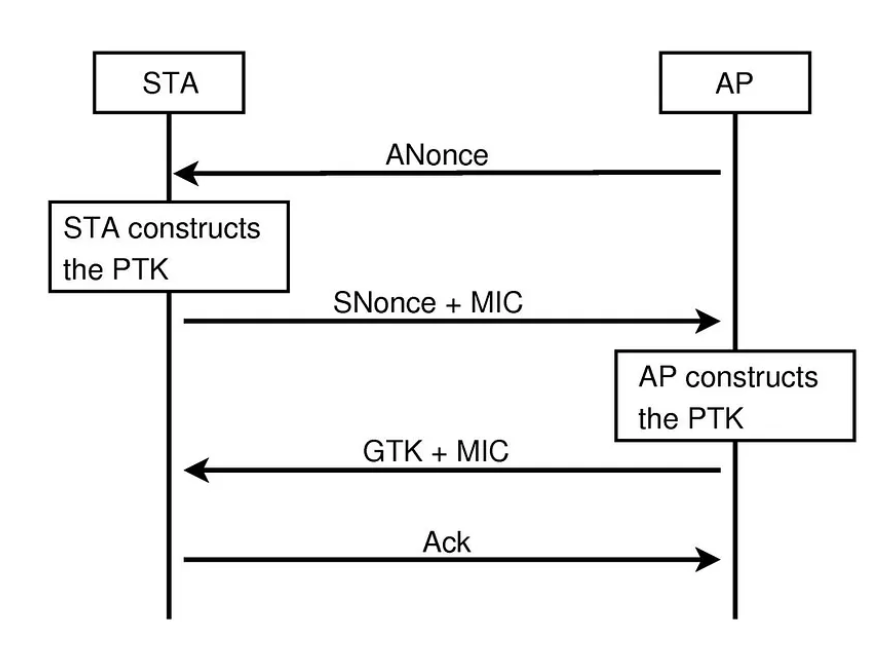
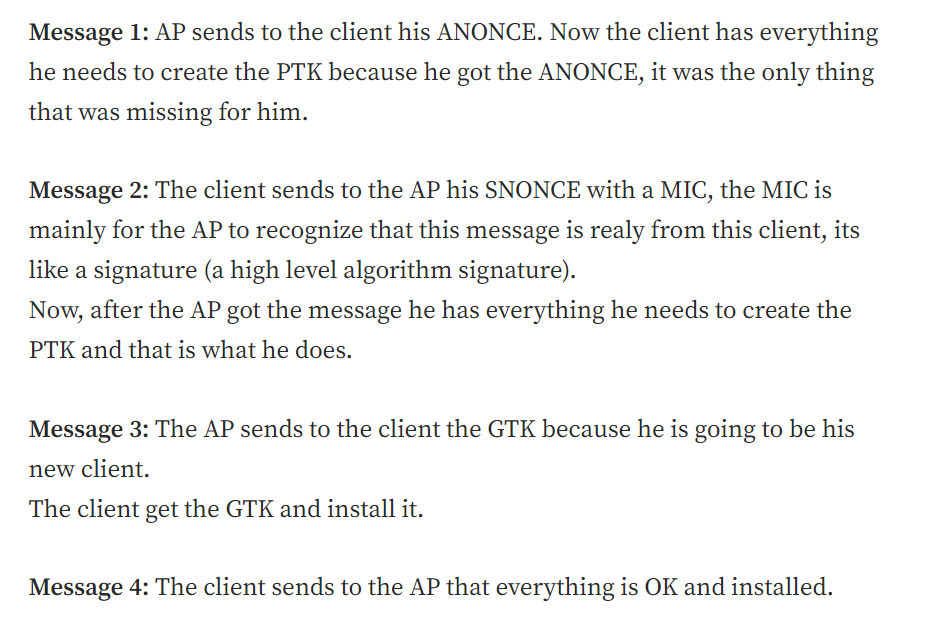

Wireless Encryption
The two most common types of wireless encryption are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA).
Wi-Fi systems use symmetrical encryption, the same key is used to encrypt and decrypt data.
Wired Equivalent Privacy - WEP
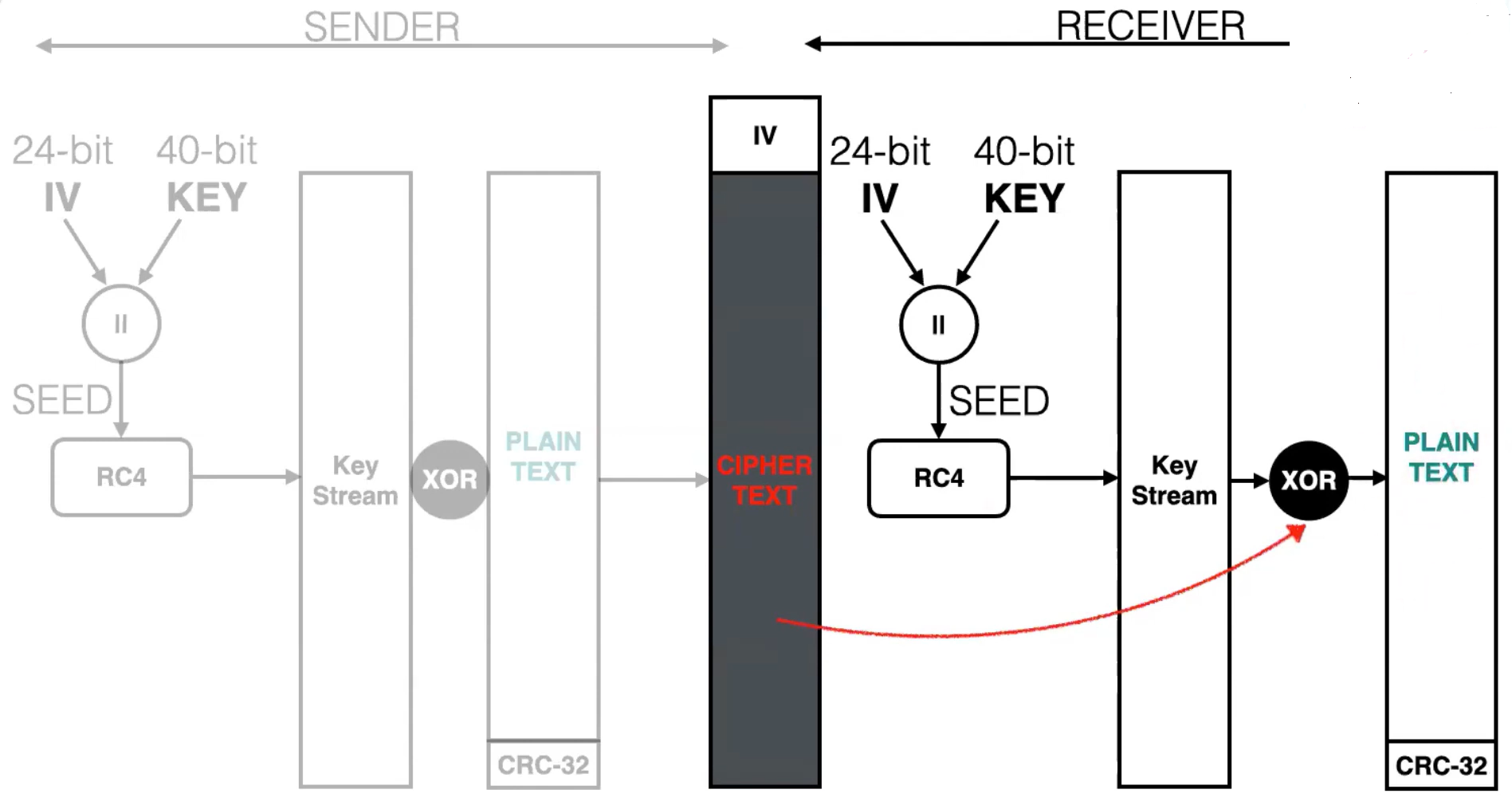
IV and RC4 encryption
WEP (Wired Equivalent Privacy) is the oldest and most common Wi-Fi security protocol.
WEP relies on a secret key that is shared between a mobile station (eg. a laptop with a wireless ethernet card) and an access point (ie. a base station). The secret key is used to encrypt packets before they are transmitted.
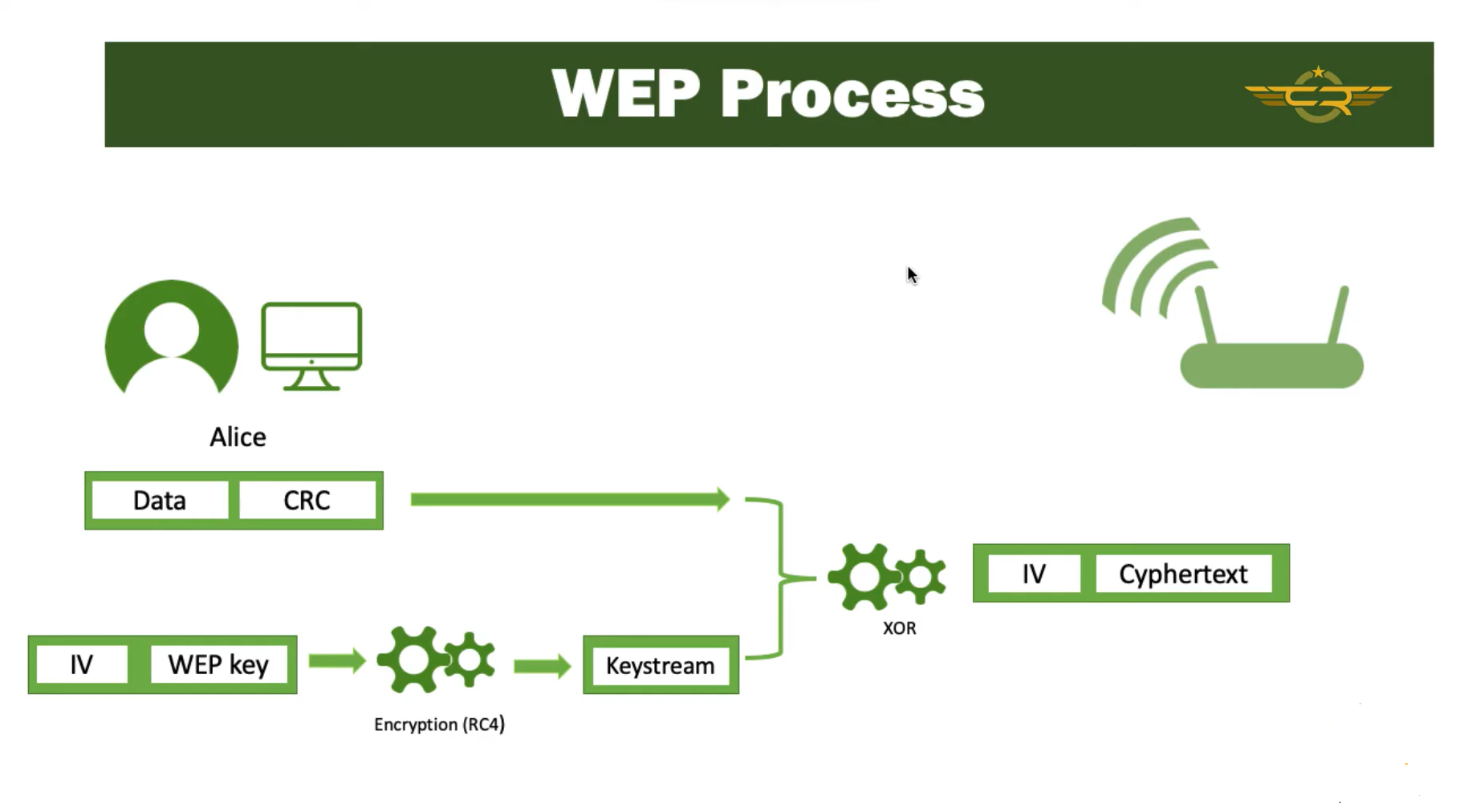
WEP uses the RC4 (also known as Rivest Cipher 4) cipher algorithm for making every frame encrypted CRC-32 checksum for confidentiality and integrity.
The RC4 cipher also encrypts data at the sender side and decrypt data at the receiving site, using a string of bits as key called WEP key.
The two widely used standards were WEP-40 and WEP-104.
-
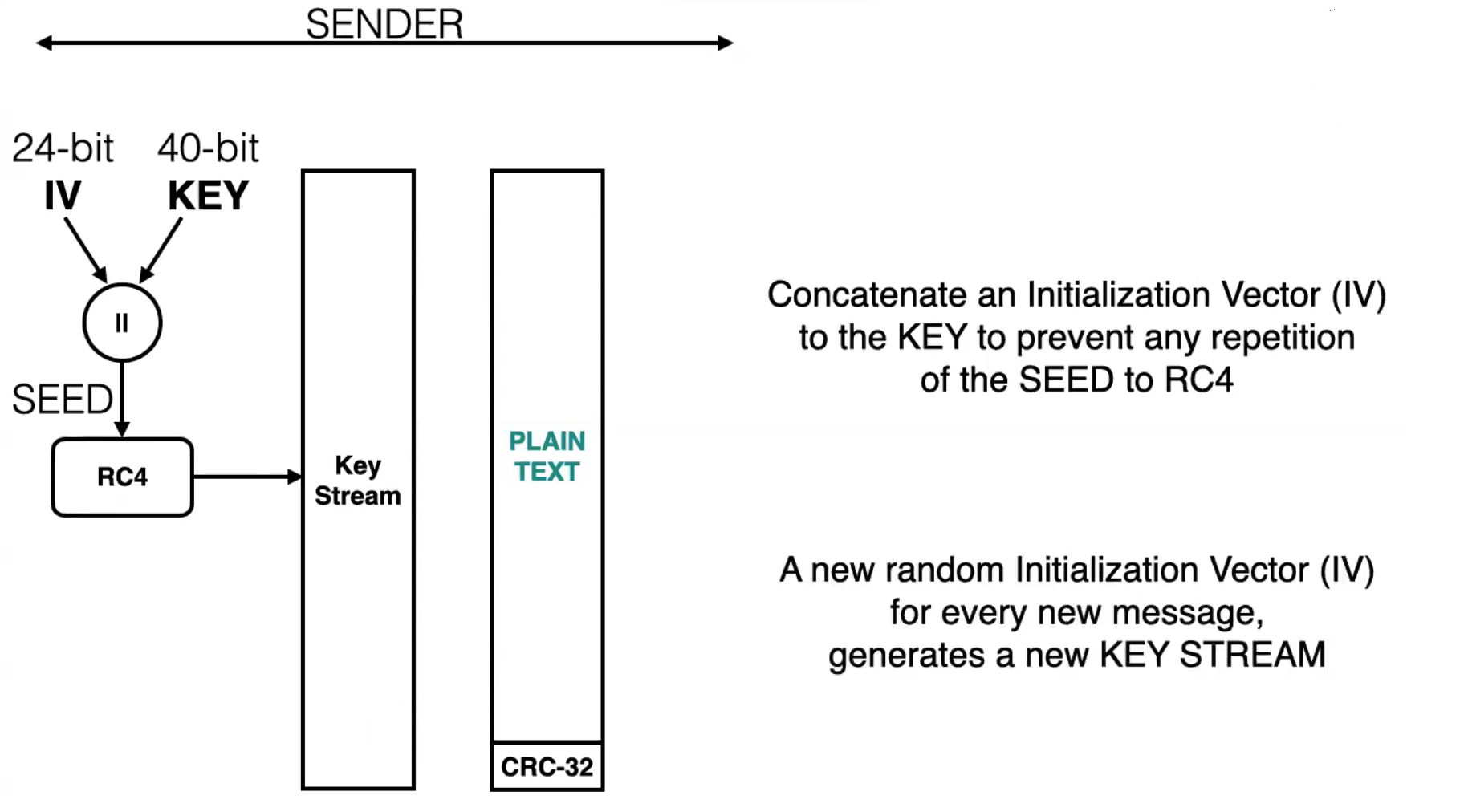
In WEP-40, a 40 bit WEP key is concatenated with a 24 bit initialization vector, to generate a 64 bit RC4 key.
-
In WEP-104, a 104 bit WEP key is concatenated with the 24 bit initialization vector, to generate a 128 bit RC4 key.
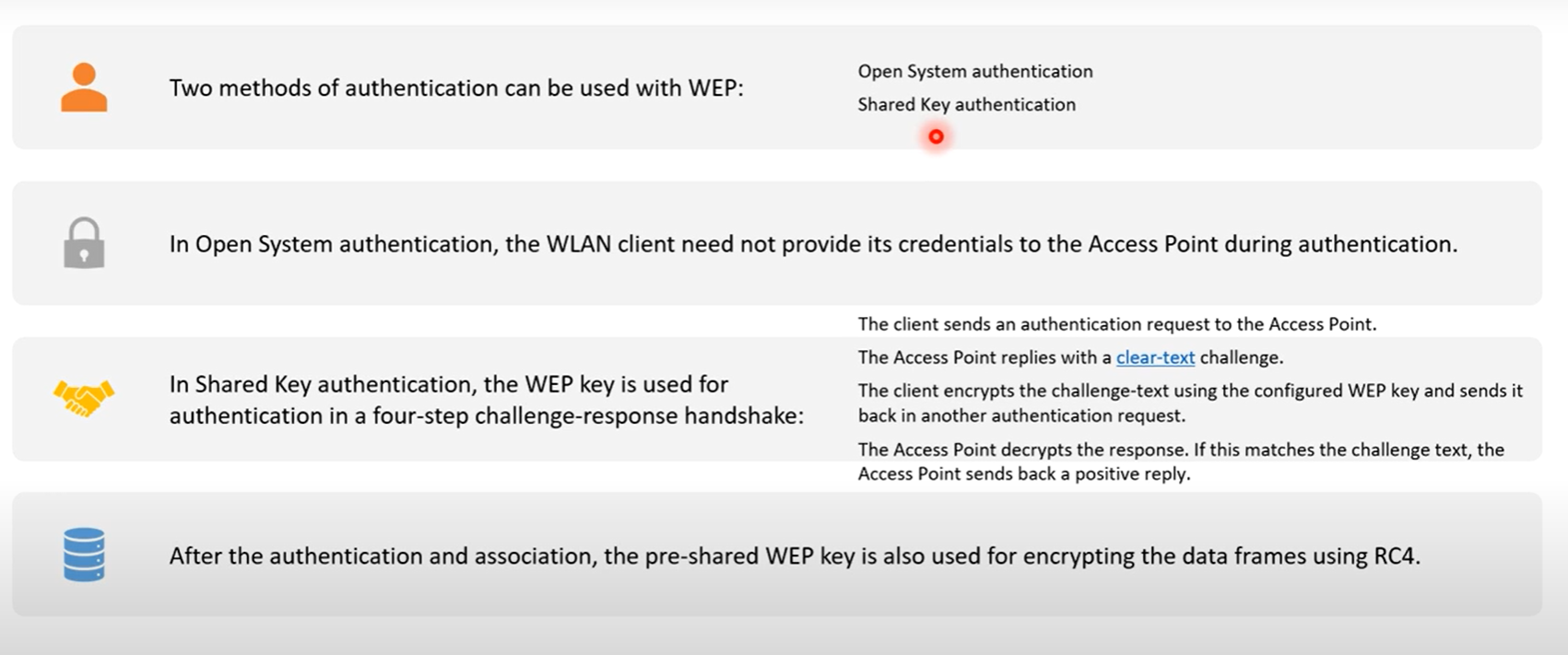
In the Open system, The key exchange mechanism is not correctly mentioned but the key must be staticly configured on the AP and Client.

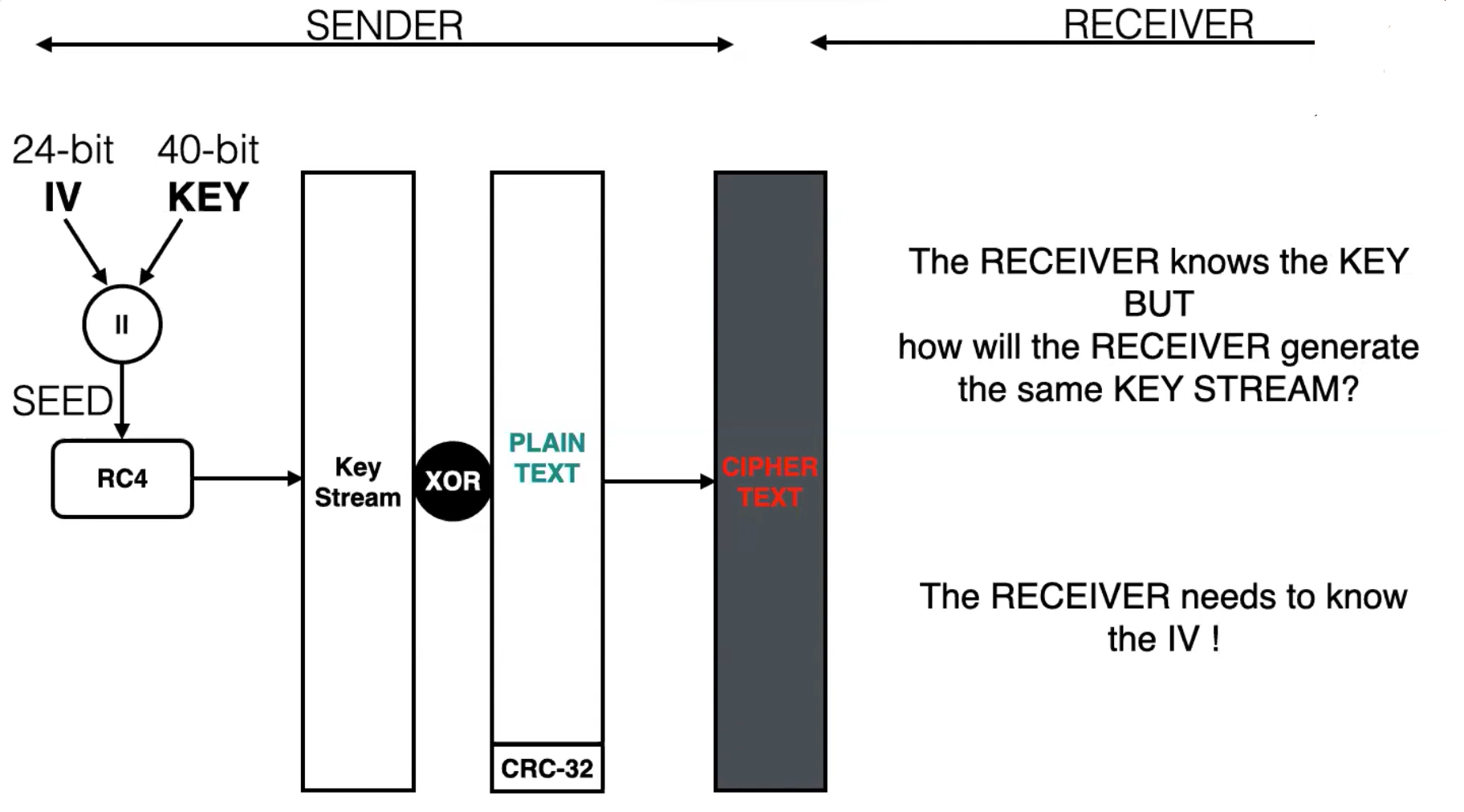
IV is unique for every new msg that has been sent. But the issue is that we have only 24bit for IV in WEP-40 So once we are able to capture the packets long enough to completely use the 24 bit then the IV starts to duplicate then we could use cryptanalysis to derive the WEP key.

Dynamic WEP
Implemented non-standard fixes for WEP
Dynamic WEP refers to the combination of 802.1x technology and the Extensible Authentication Protocol. Dynamic WEP changes WEP keys dynamically. It is a vendor-specific feature.
The dynamic change idea made it into 802.11i as part of TKIP.
802.11i - WPA
Longer IV and RC4 encryption, Each clients gets new keys with TKIP
The Temporal Key Integrity Protocol (TKIP) was adopted for WPA.
TKIP employs a per-packet key, which means that it dynamically generates a new 128-bit key for each packet and thus prevents the types of attacks that compromised WEP.

WPA has two main components
-
The Temporal Key Integrity Protocol (TKIP) addresses the privacy concerns via enhanced encryption schemes.
-
The authentication component uses 802.1x and an authentication server to provide user-level access.


WPA2
CCMP with AES encryption


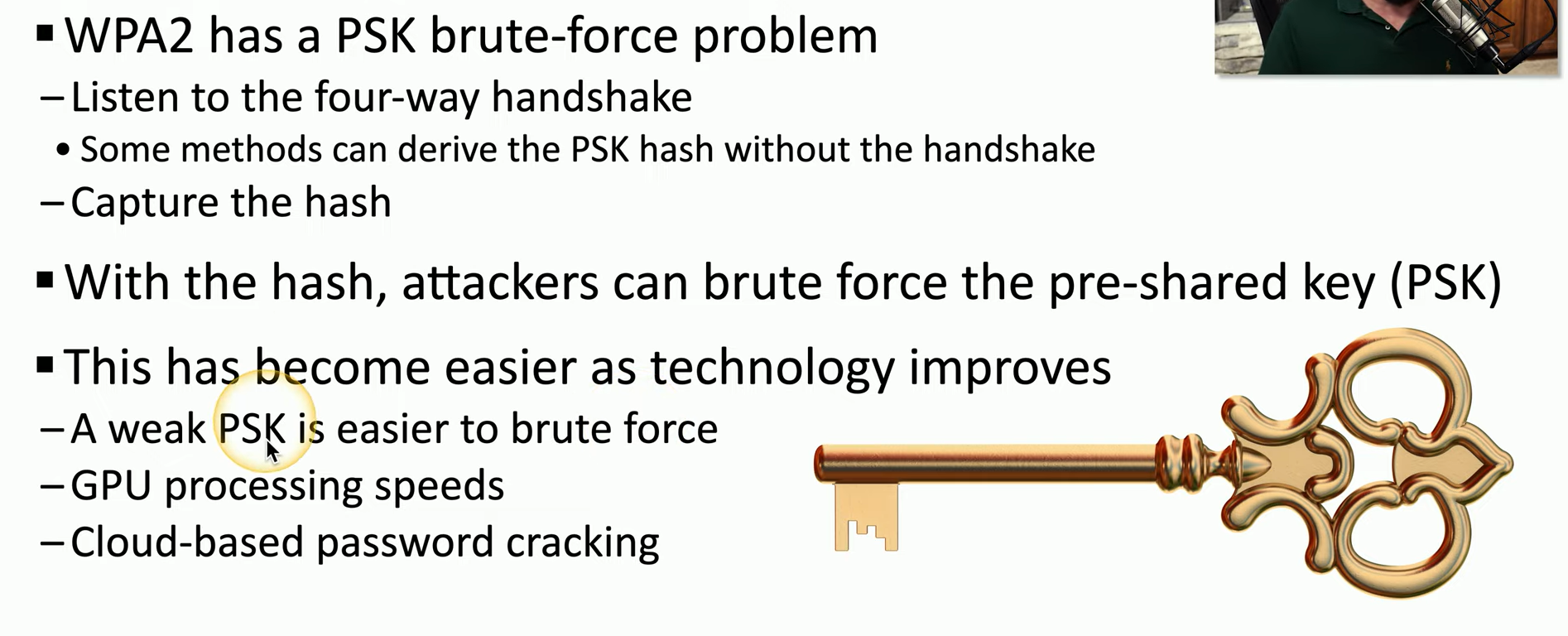
WPA/WPA2 PSK/Enterprise

WPA3

