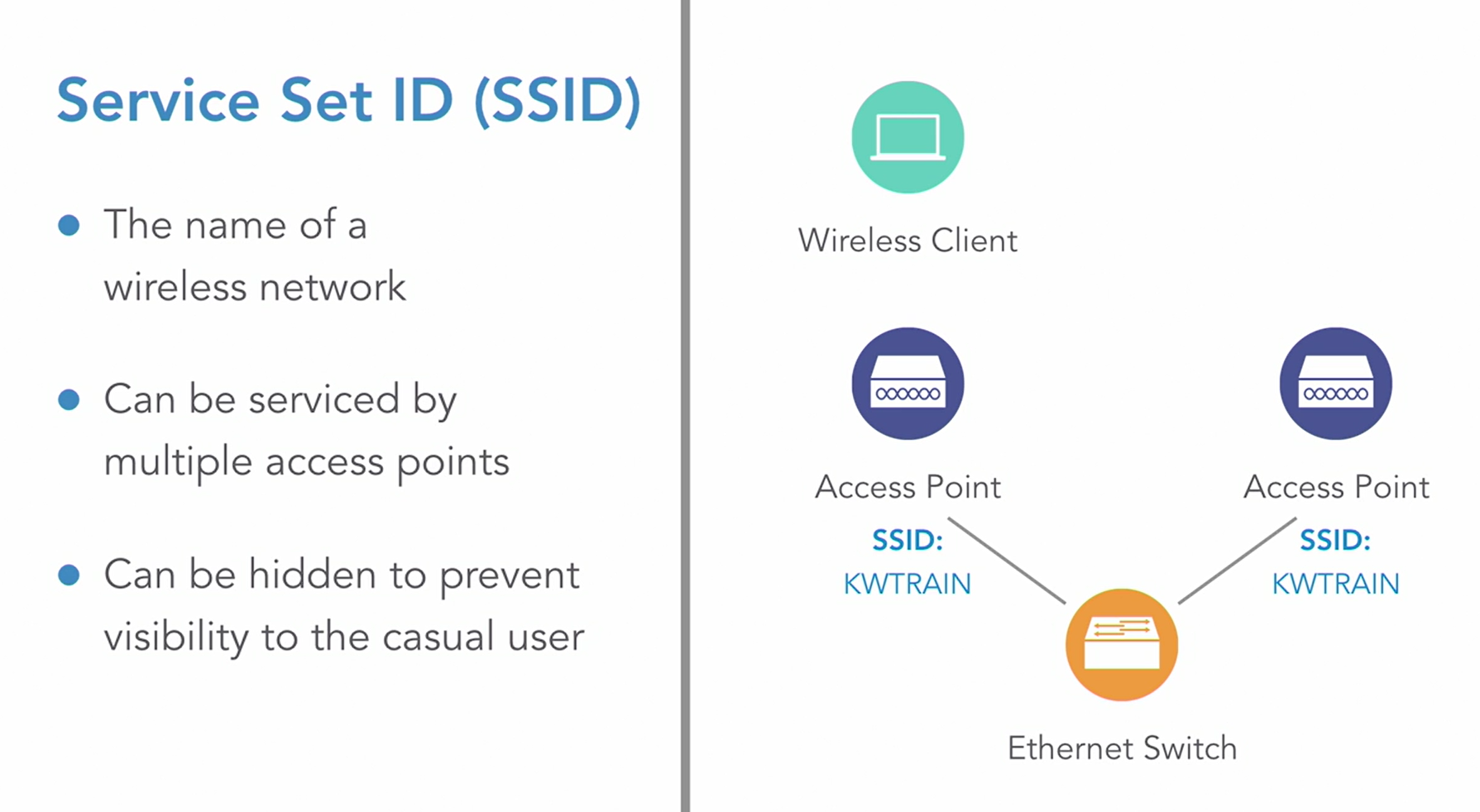
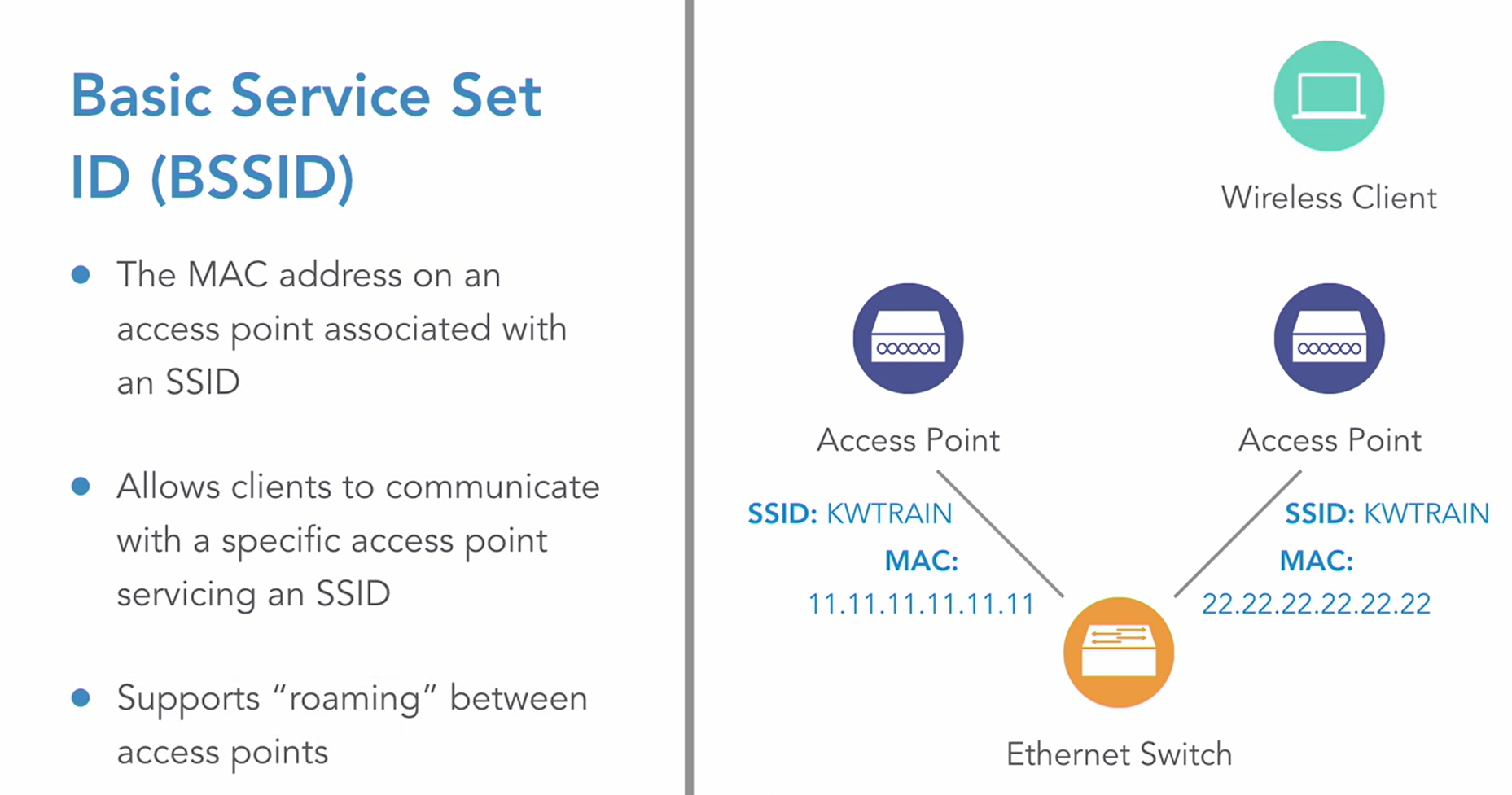
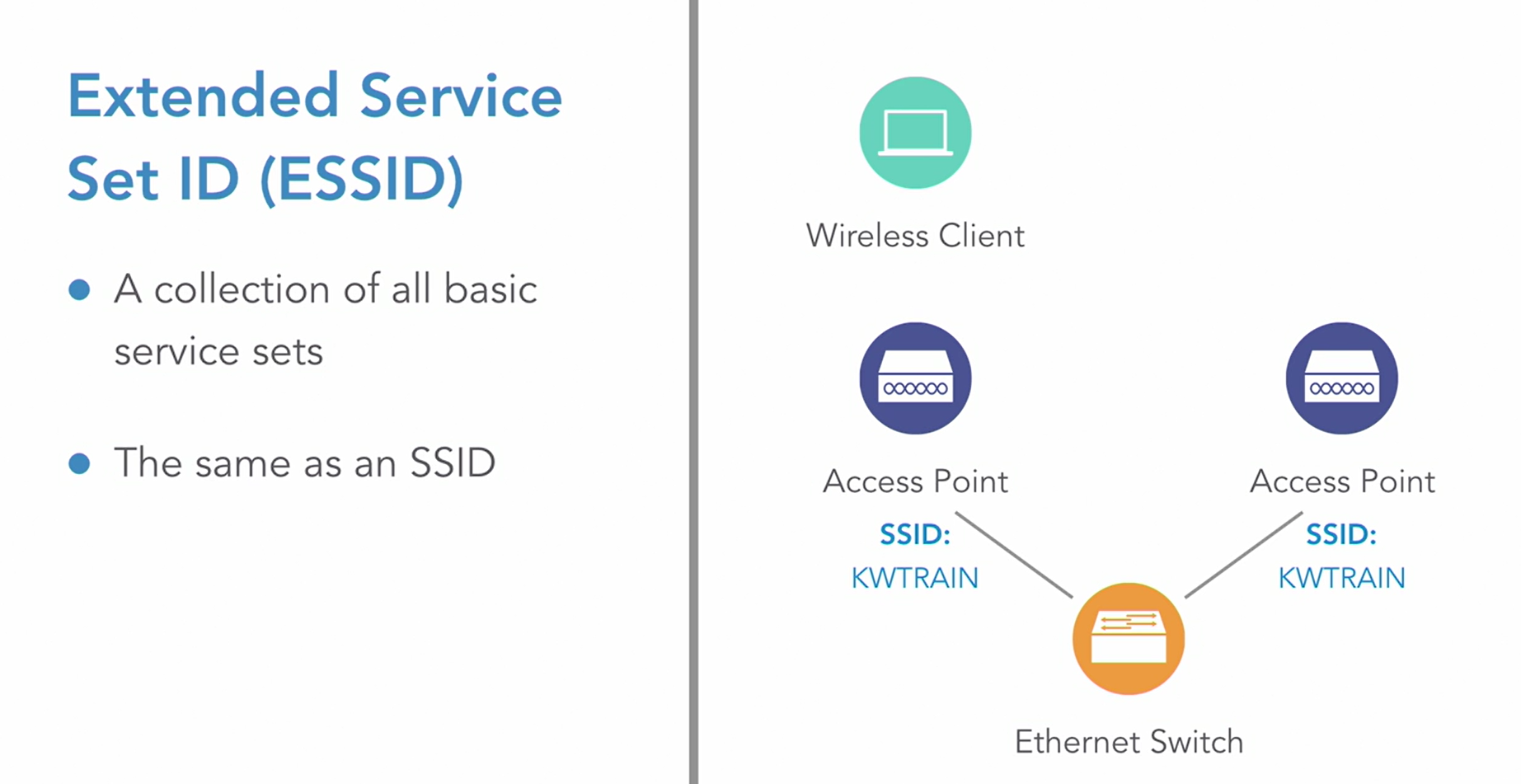
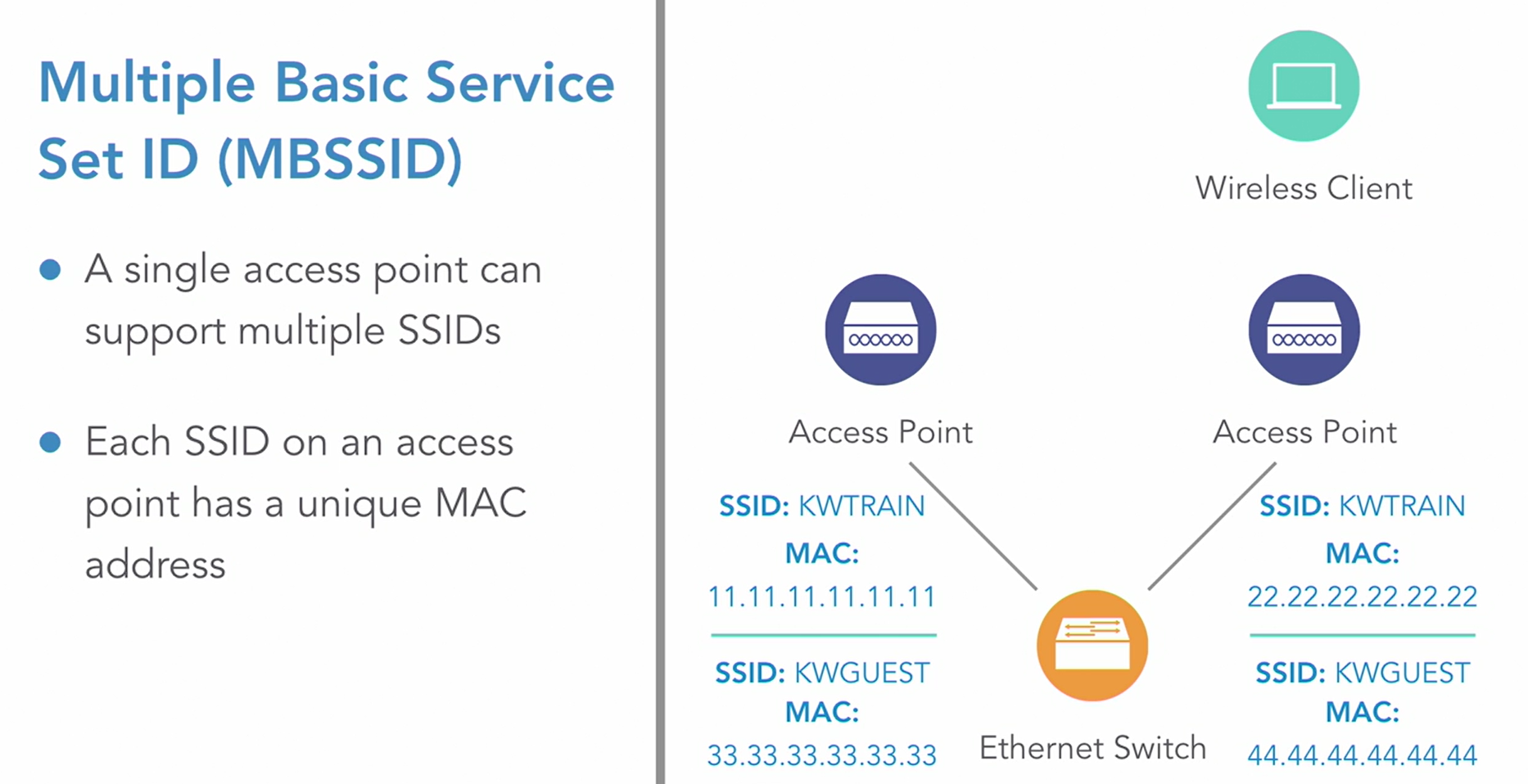
1_Wireless Networking Essential - LogeshVel/802.11 GitHub Wiki

DSSS
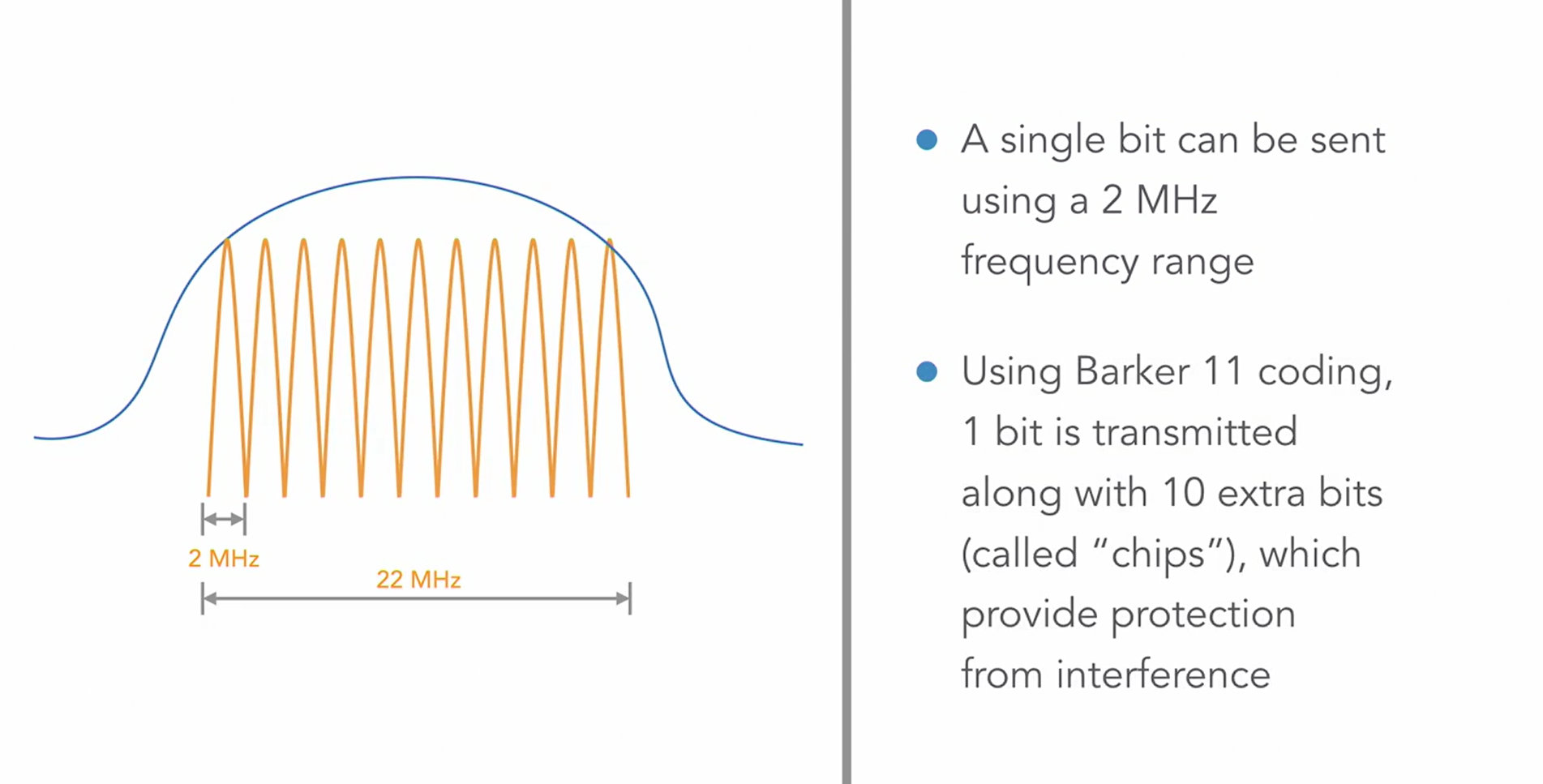
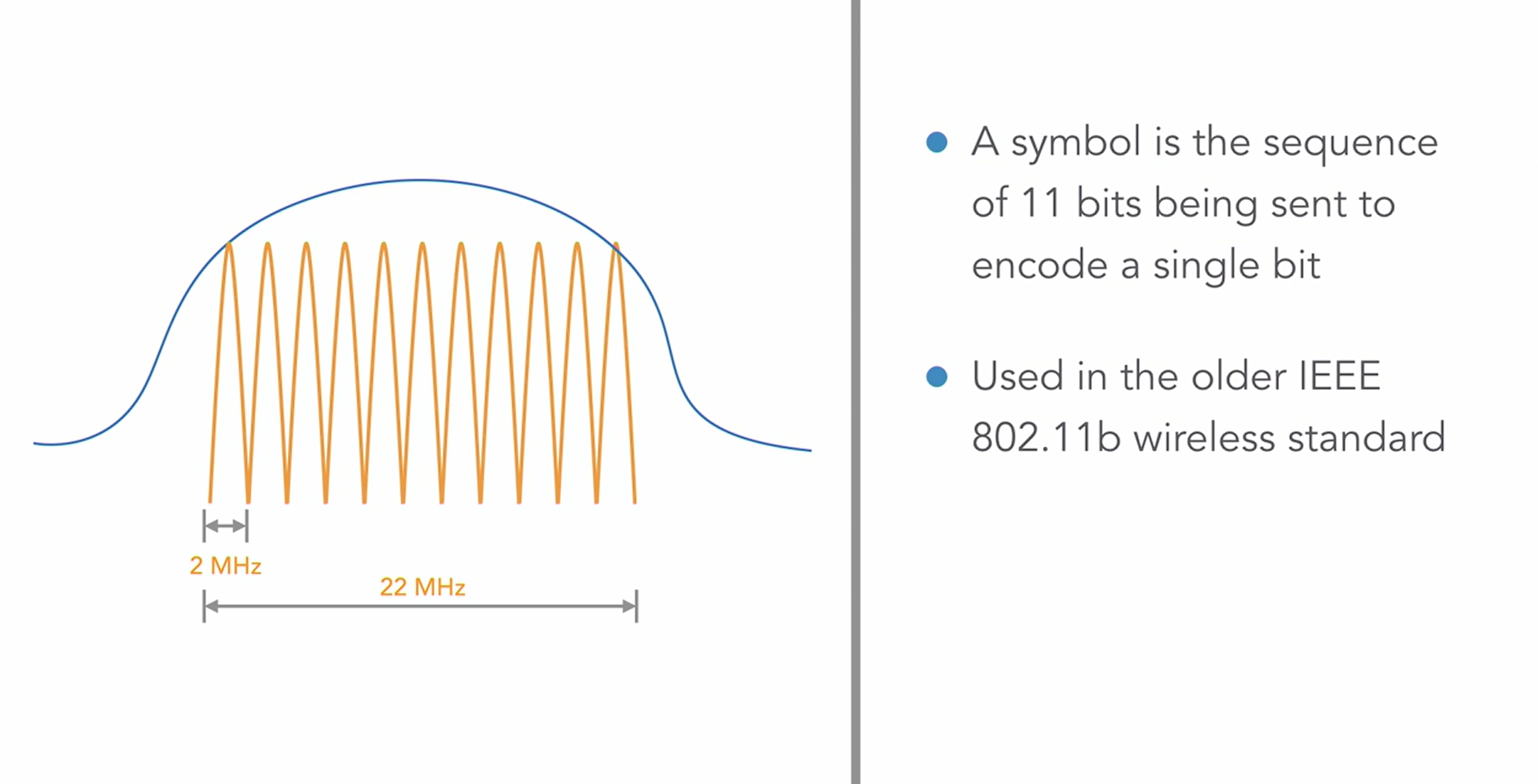
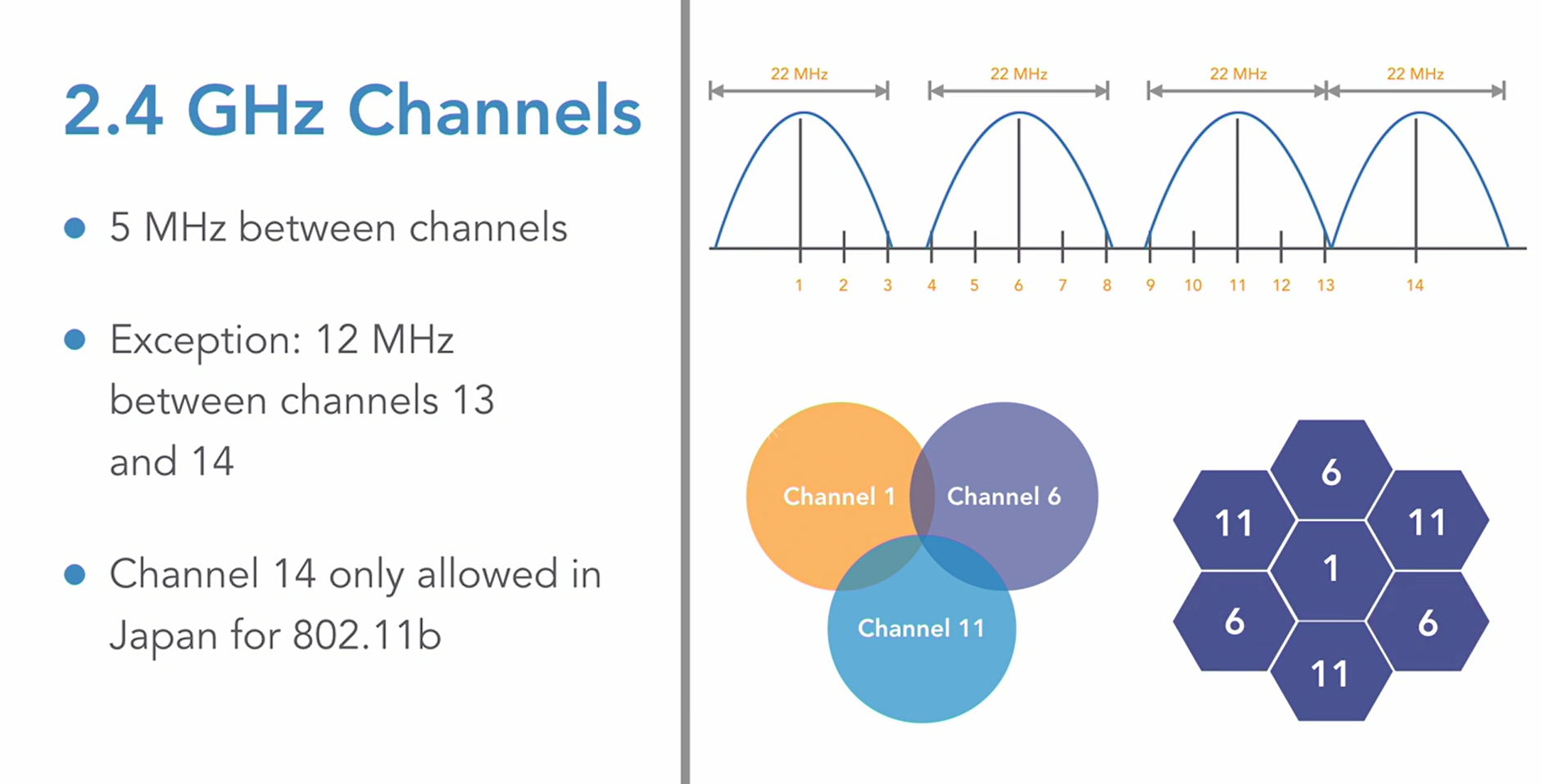
This is where the 22 MHz range for the single channel in the 2.4GHz is required.
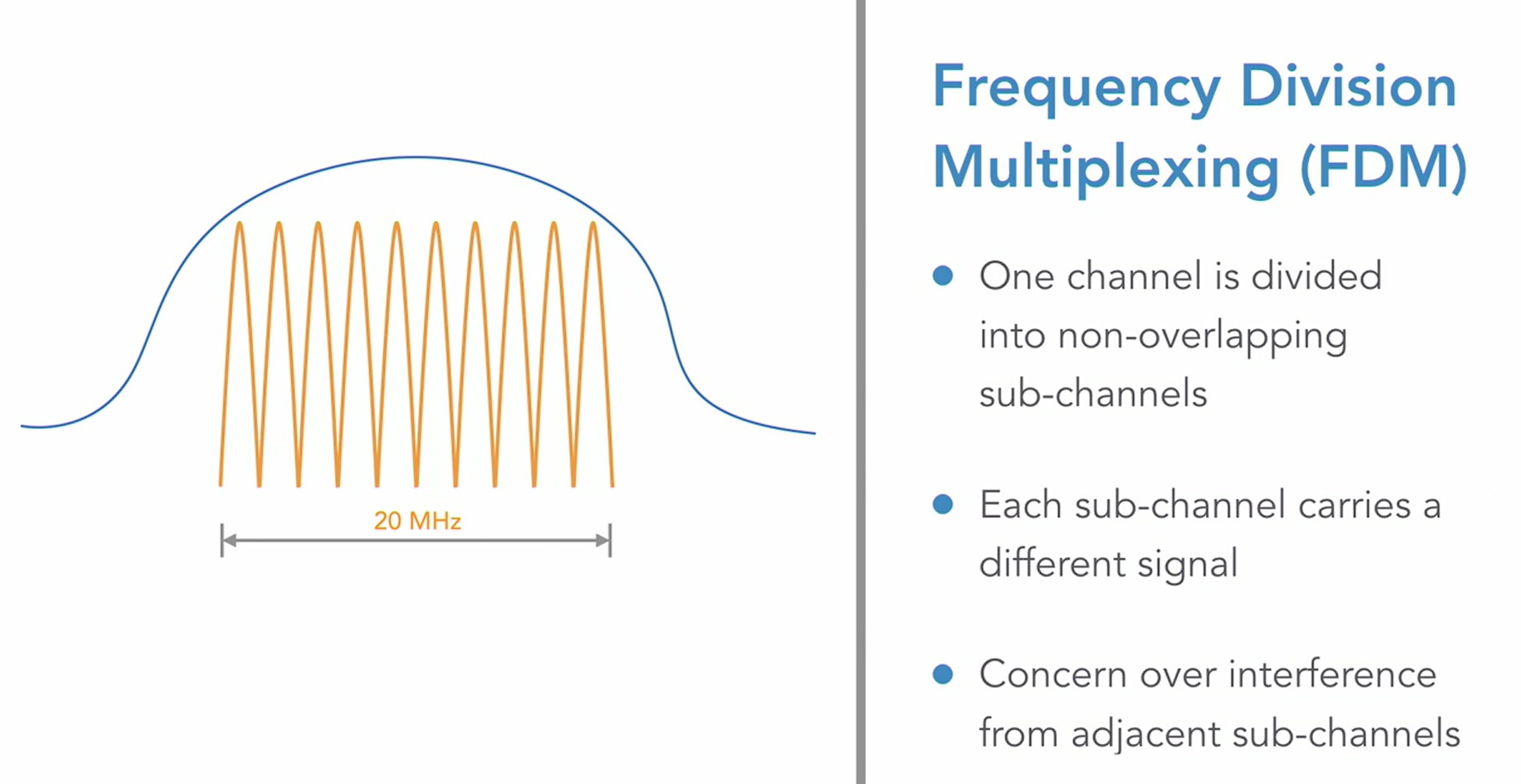
FDM
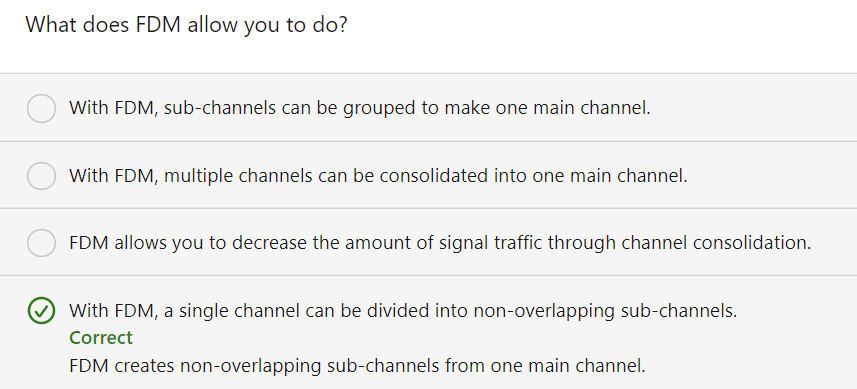
OFDM
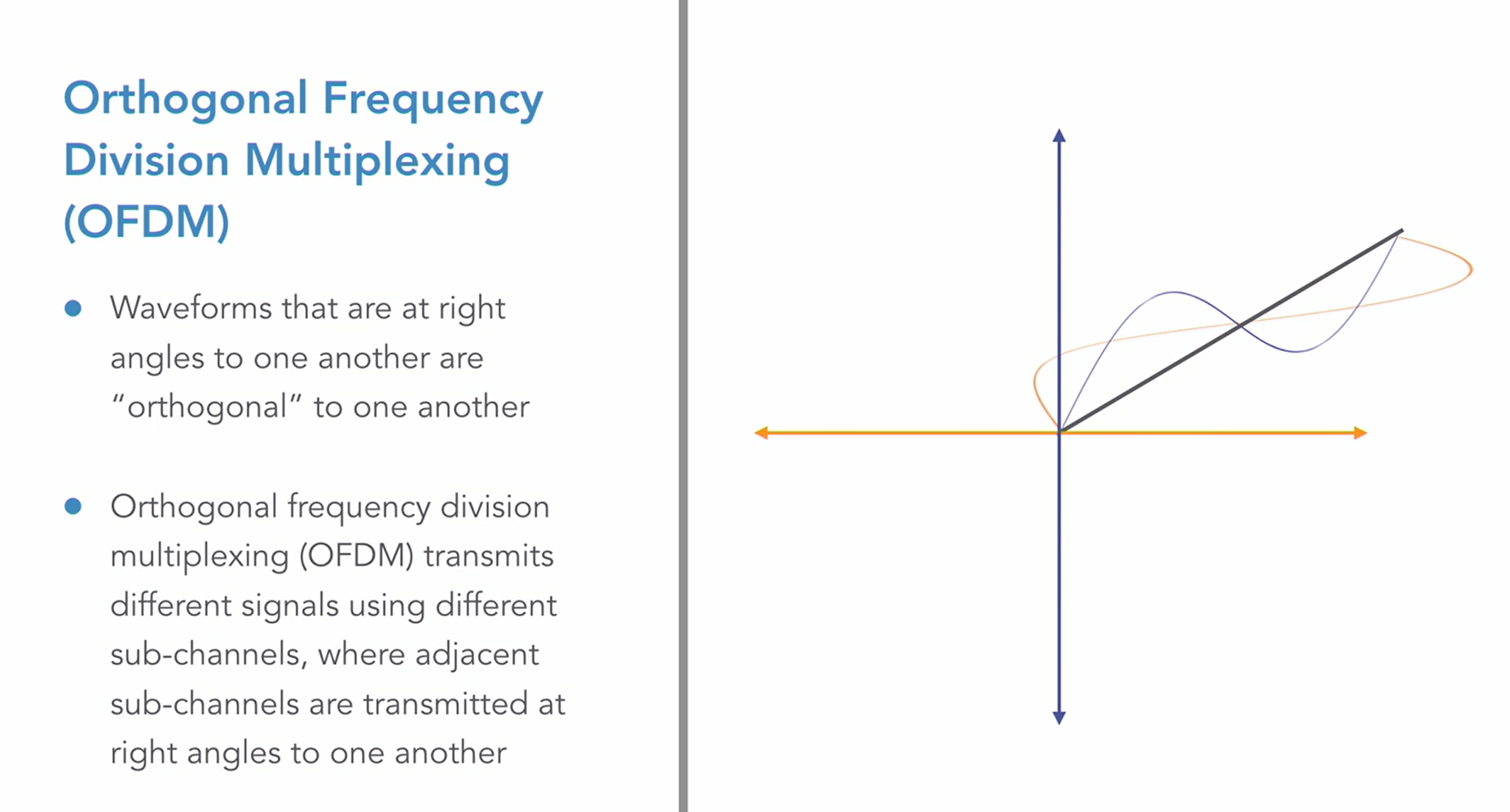

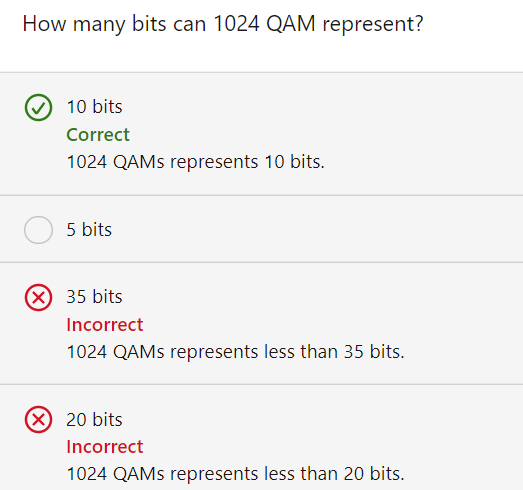
QAM
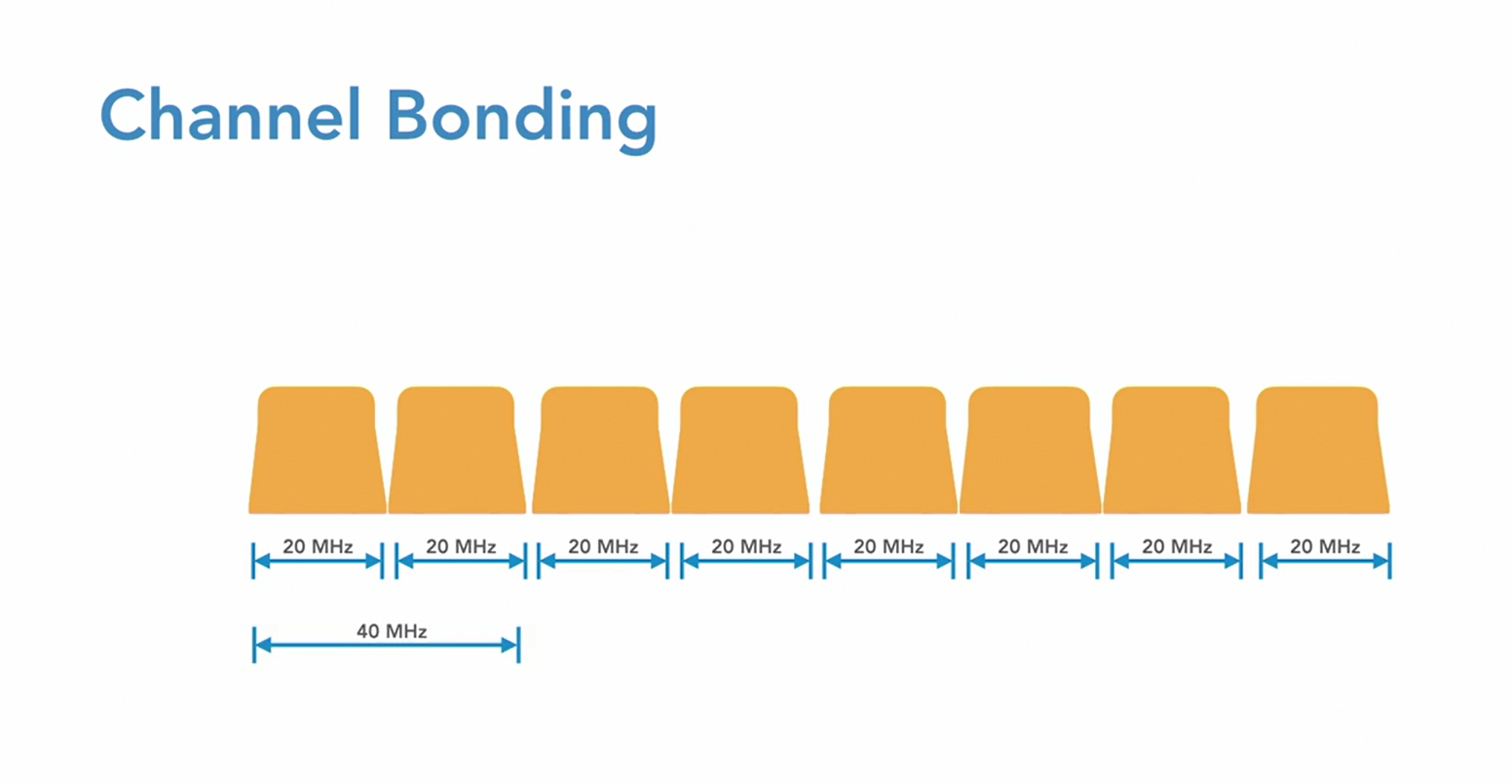
Channel Bonding
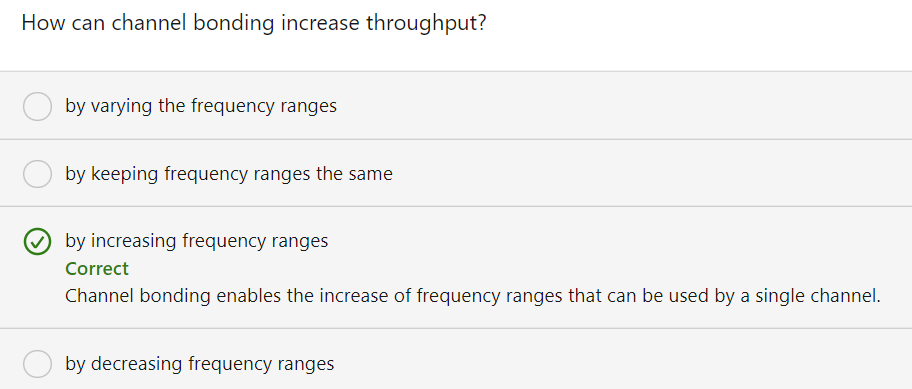
Beamforming
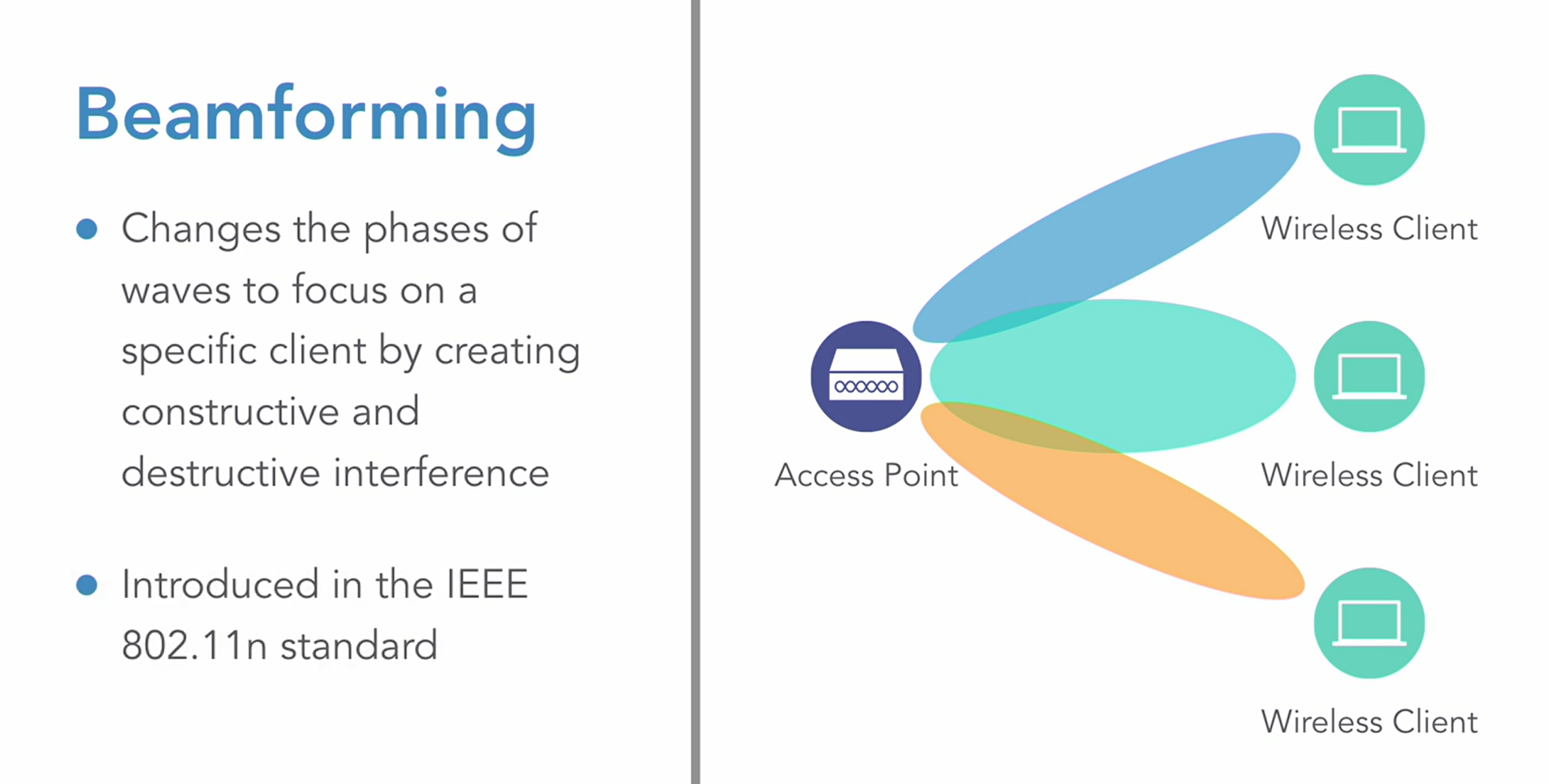

MU-MIMO
MU-MIMO stands for multi-user, multiple input, multiple output. Basically, we're talking about having multiple antennas inside of our access points. Way back in 802.11n, we had a single spatial stream, meaning that we could transmit one stream of communication at any one time. For example, if I needed to talk to both wireless clients from this access point on screen, I would have to send the signal twice. Once to one client, and then I'll have to send it to the other client. I would have to take turns. However, with the current versions of 802.11ac and now 802.11ax, we can have multiple antennas that simultaneously transmit out to multiple clients. As an example, let's say that here we have two spatial streams, where I can simultaneously communicate from my access point to both wireless clients. That's going to give us increased throughput in larger networks.
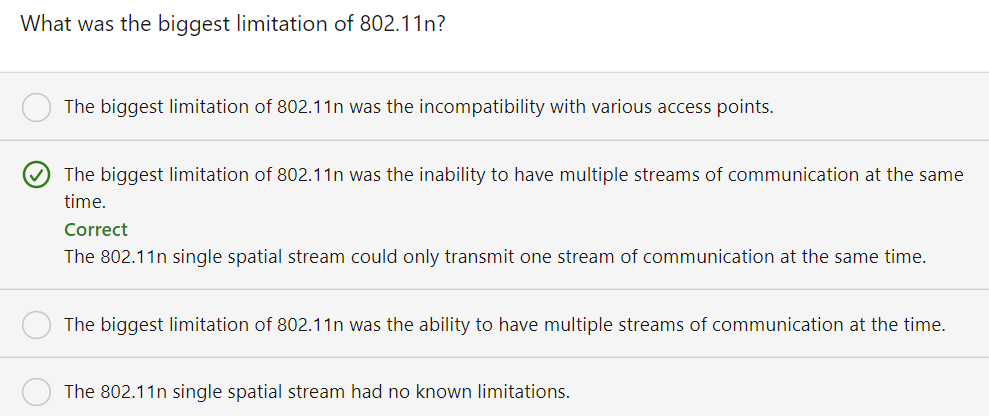
OFDMA
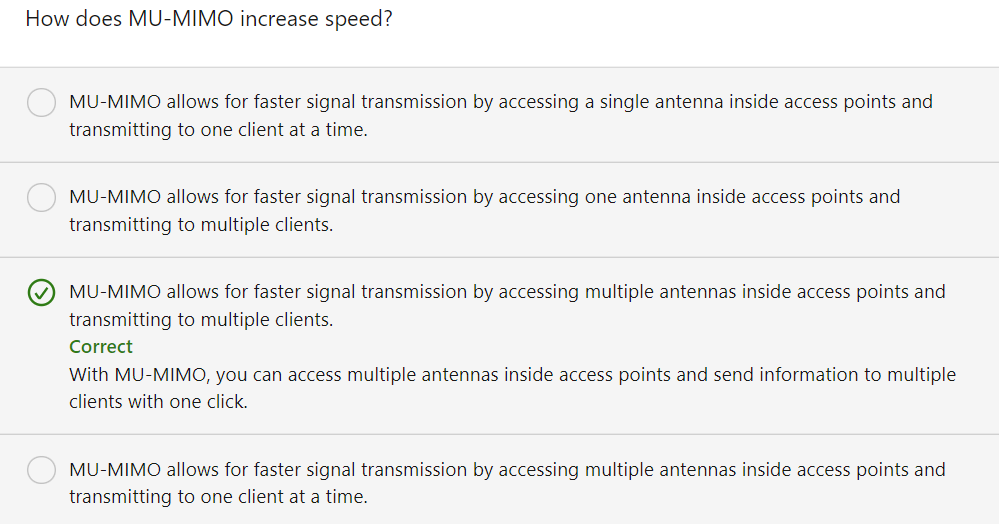
In orthogonal frequency-division multiplexing, or OFDM we took a single frequency range and we divided it up into multiple sub-channels. And that way, each user could have a different sub-channel. However as we have more and more wireless clients, we might have too many wireless clients trying to transmit at the same time. To address that issue, we can use something called orthogonal frequency-division multiple access, or OFDMA. With OFDMA, each of those sub-channels get subdivided into sub-carriers, and each user can then be assigned to a sub-carrier.
It's going to look something like this. In this example, the blue arrows represent user one's sub-carrier. And the yellow arrows represent user two's sub-carrier. This allows multiple users to simultaneously transmit using the same sub-channel. And as we're going to see later, this is one of the technologies that gives 802.11ax such a high throughput.
802.11n - WiFi4

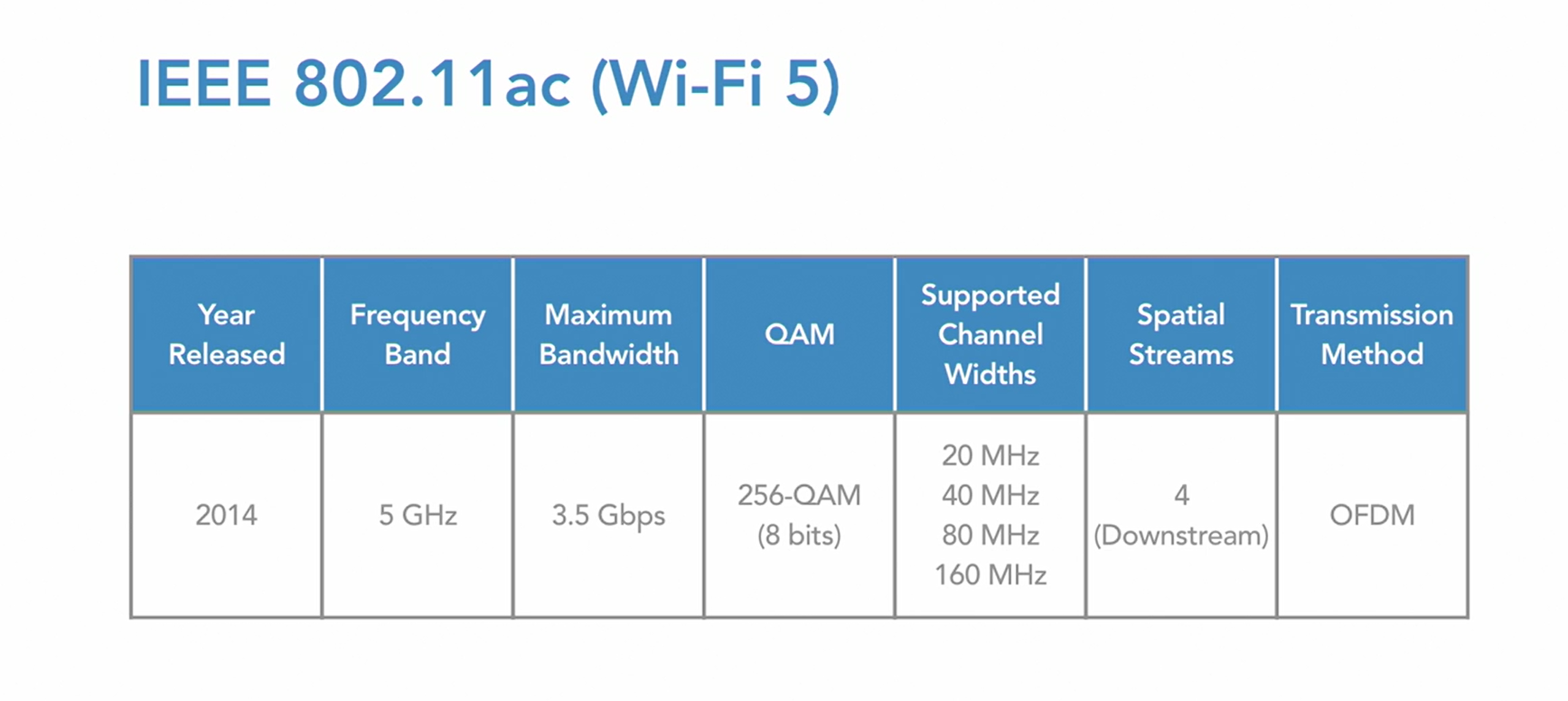
802.11ac - WiFi5
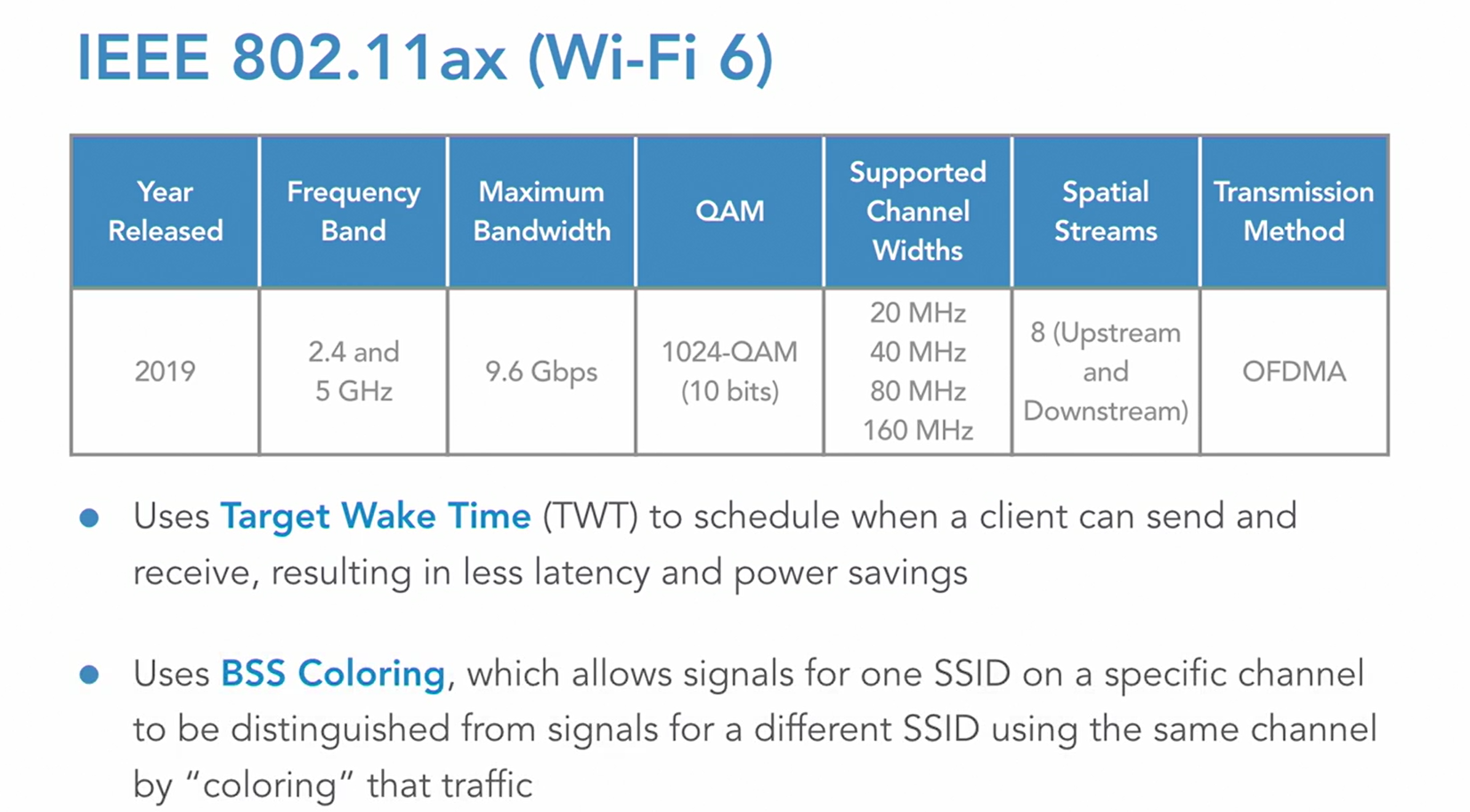
802.11ax - WiFi6
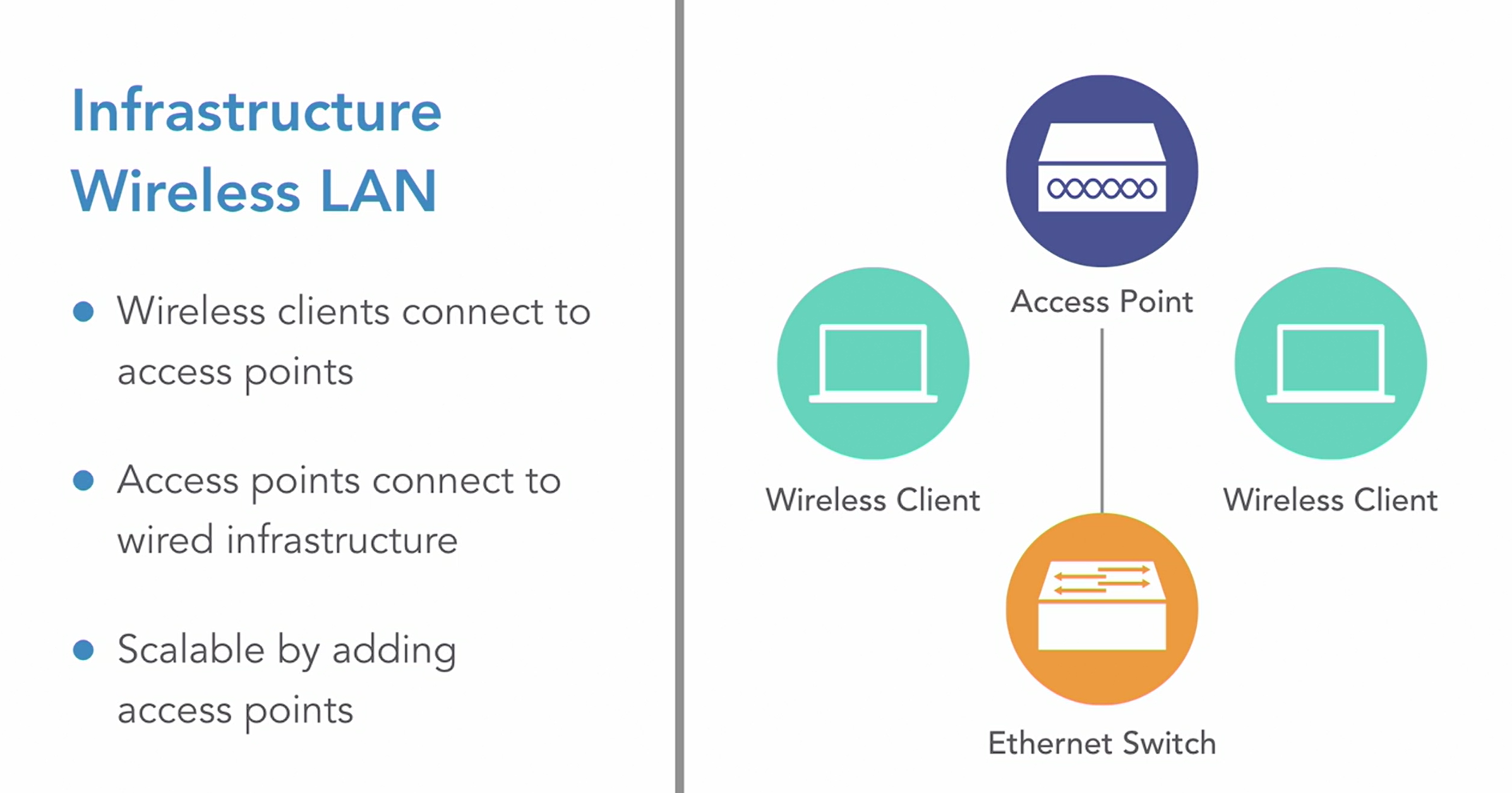
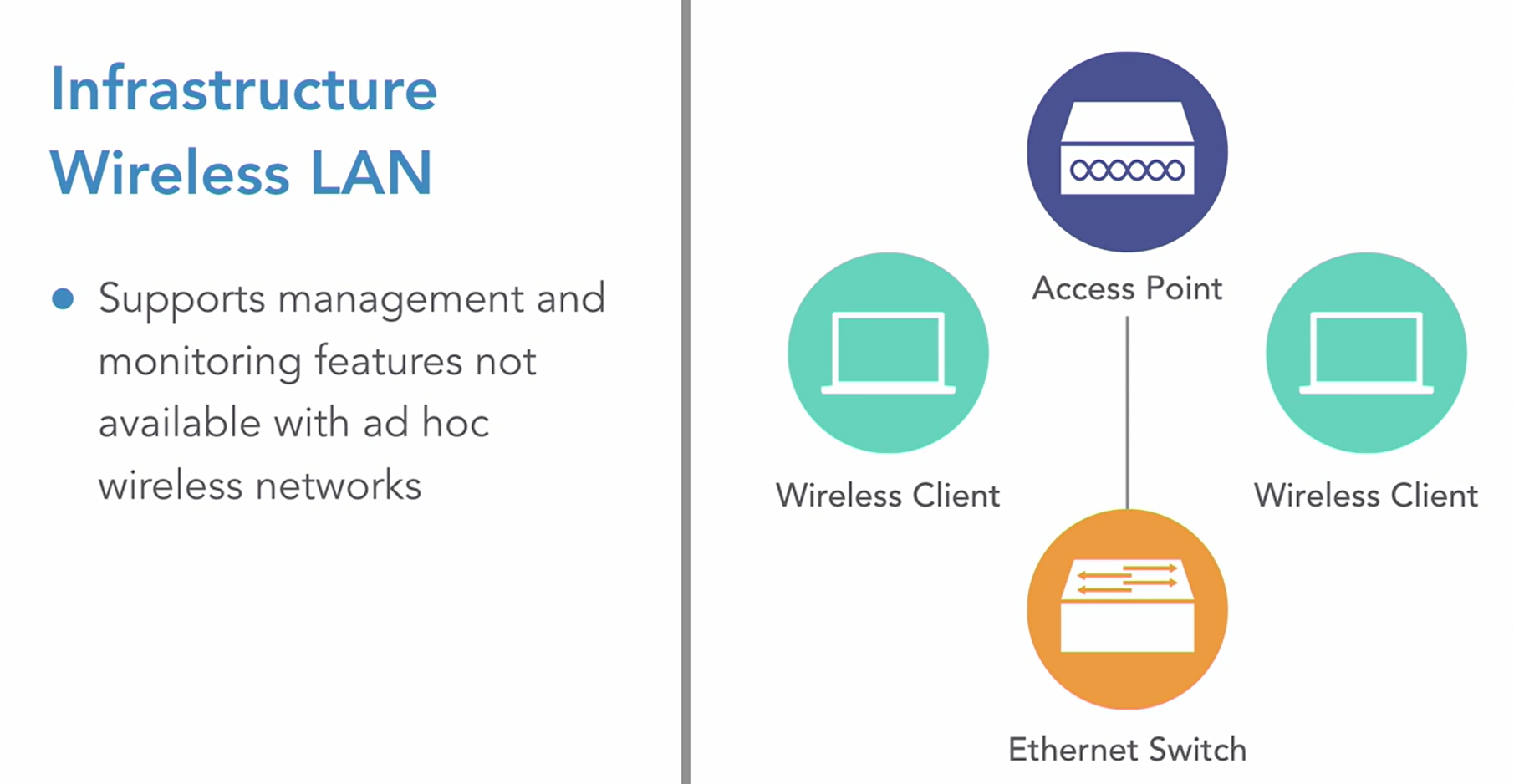
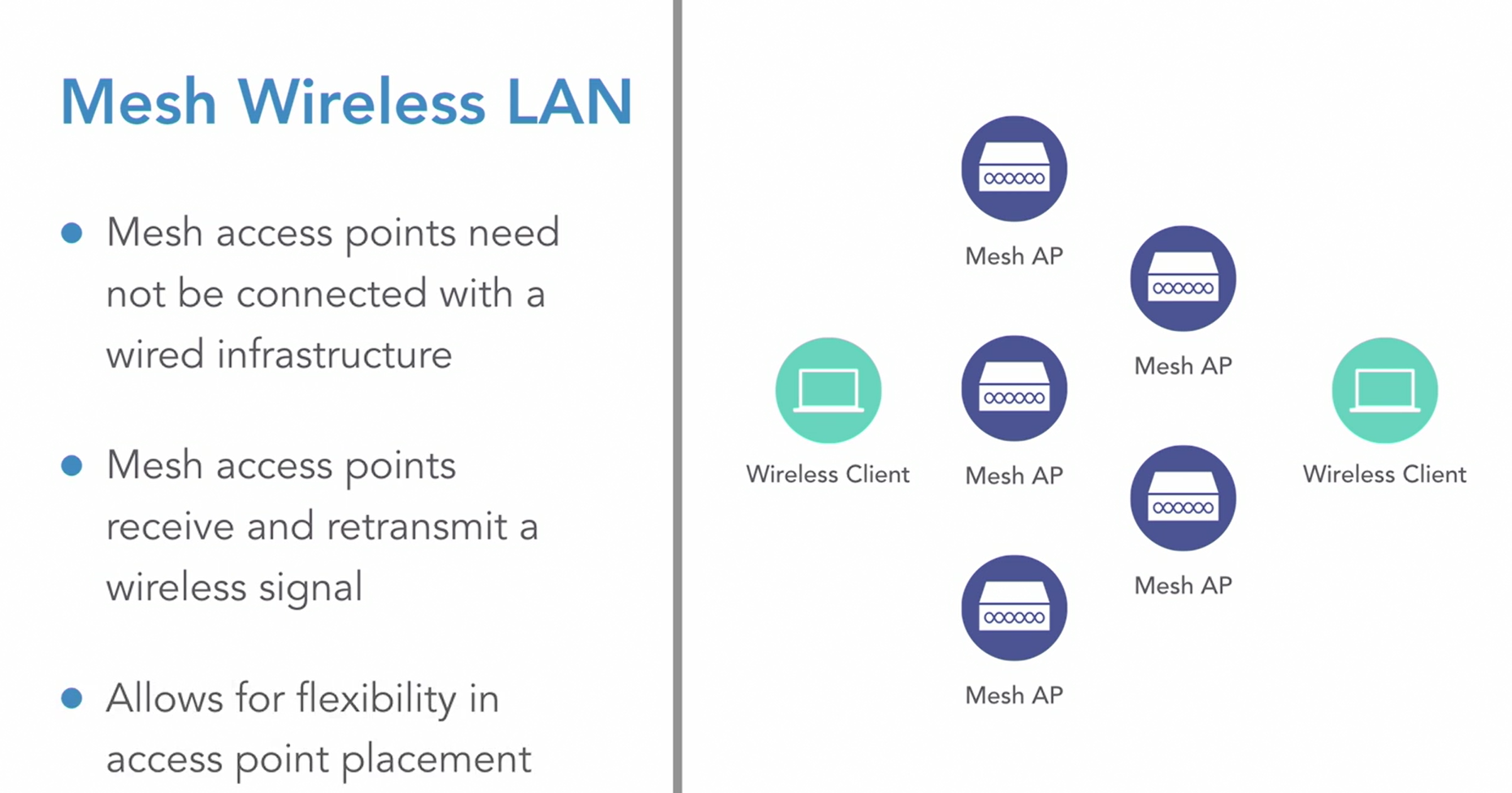
Wireless Security

WEP

With the RC4 encryption algorithm, we use something called an initialization vector, or IV for short. And this IV is combined with the shared secret key that we configure on our access point, and our wireless clients. And that's applied to the string of data we want to encrypt, and the resulting encrypted string of data is called ciphertext. And with WEP, the IV was only 24 bits in length. And the key could be either 40 bits or 104 bits in length. But since the IV was only 24 bits long, it became mathematically possible to capture enough encrypted packets and determine what the shared secret key was. In fact, if you were able to capture about 30000 packets containing initialization vectors, you had about a 50/50 shot of getting that shared secret key. And once you captured around 800000 initialization vectors, it was almost a guarantee that you would be able to calculate that shared secret key. In fact, on average, it takes about three minutes to crack a web password. So we do not want to use it. Also, the idea of having the same key configured on our access point and all of our wireless clients, that doesn't scale very well.
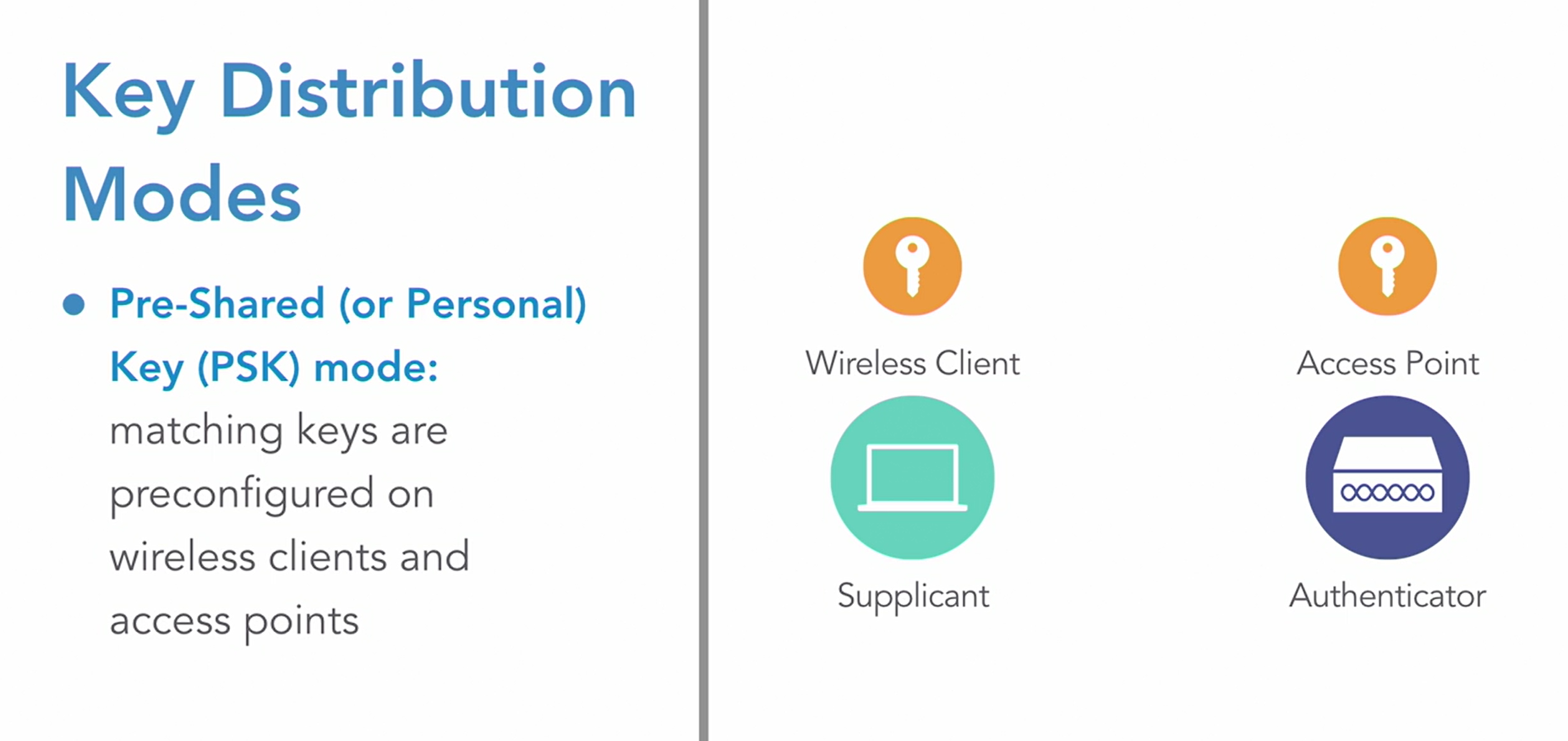
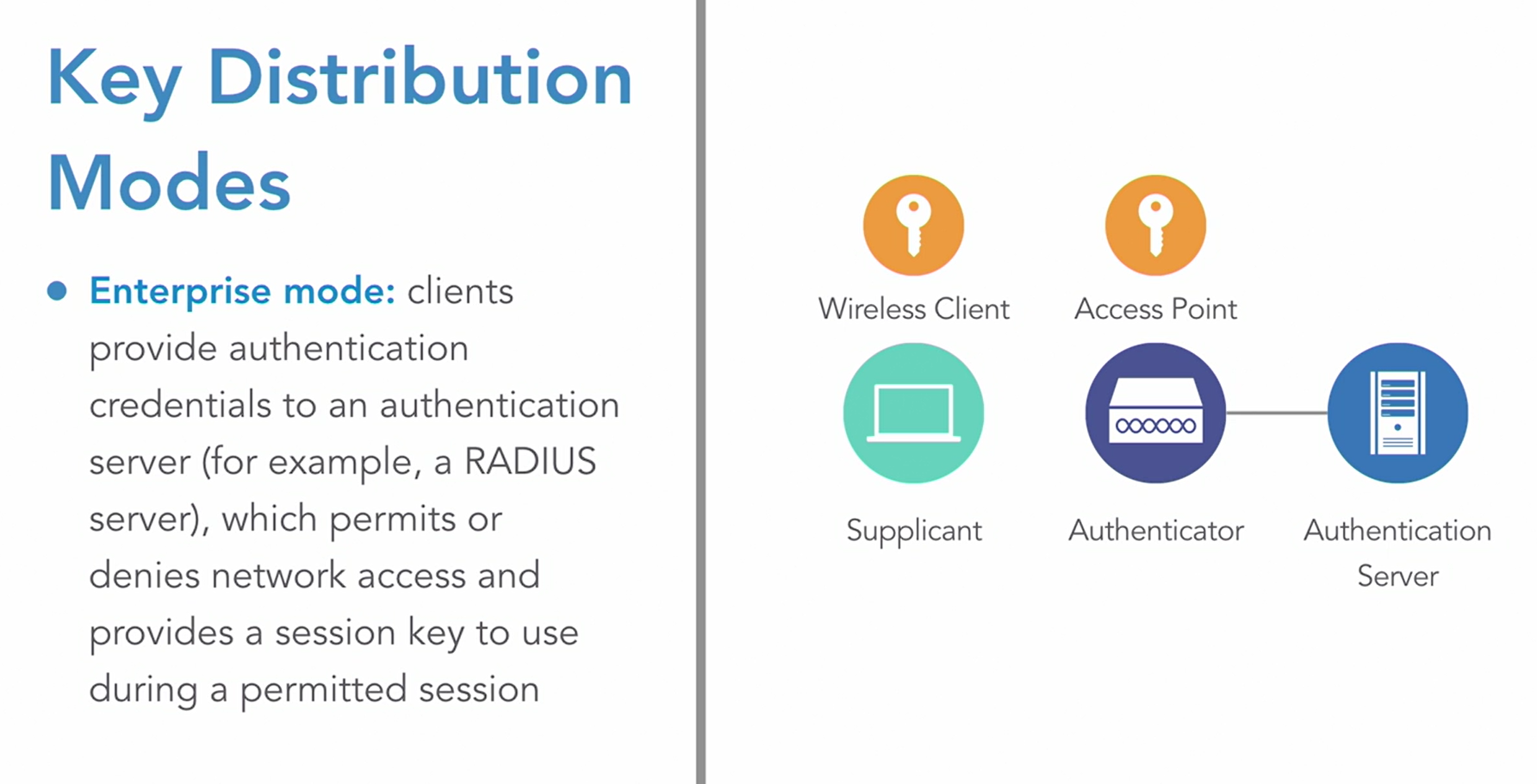
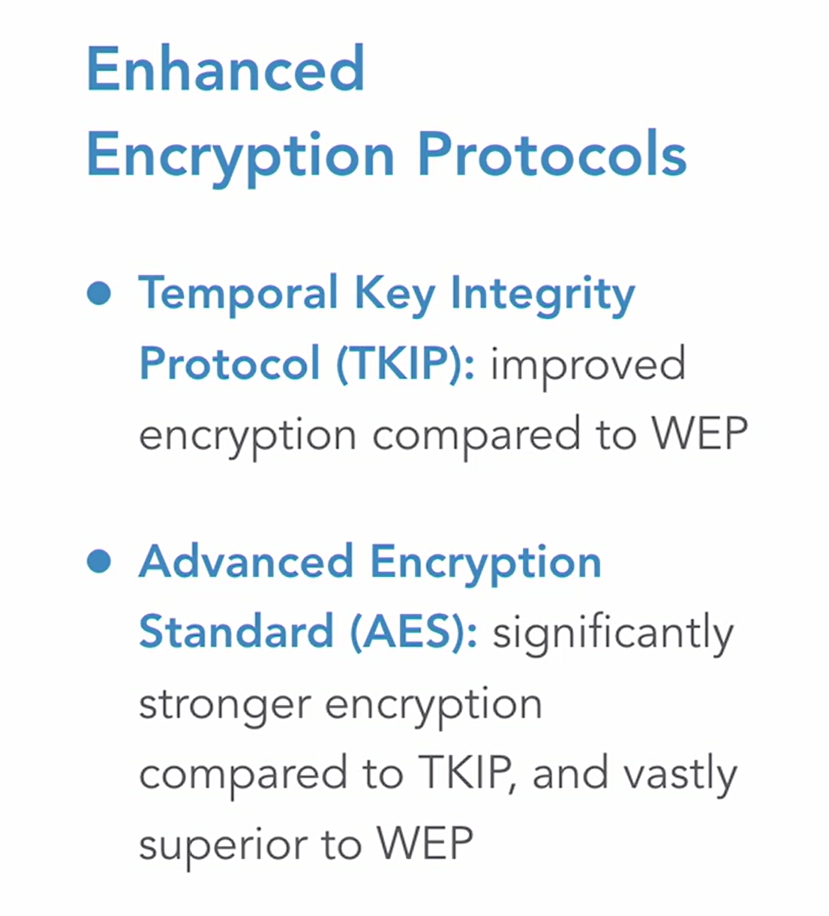

WPA/2/3