Network Security Lab - Hsanokklis/2022-2023-Tech-journal GitHub Wiki
Summary:
Doc Link
TIL(time to live)
- How many pings it does before it stops
- if it goes on forever it will mess with the network (length of our data + the headers itself)
Outcomes:
- Refresh Wireshark skills and knowledge of protocol communication, packet data/ transfer.
- Concepts behind packet spoofing
- Concepts behind SYN-SCAN and SYN FLOOD
1. Install Wireshark and run Windows 10 VM
Exploring Packets
-
In the first packet, what is the source (browser, or web client) IP address?
-
What is the destination (web server) IP address?
-
What is the length? (value in length Column)?

- Notice the frame length matches the value you just recorded

In the top Packet List section, right-click on the first packet. Choose the option for Conversation filter (TCP). There are actually 2 TCP conversations in this stream. We want to concentrate on the first one

Can you find the TCP 3-way handshake?
SYN, SYN-ACK, ACK
- What packet numbers does it use?
Packets 1, 2 and 3

- What packet does the HTTP protocol show up in?
Packet 4

This is the start of the http conversation
- Packet 38 is the end of the http conversation (HTTP 200 OK)

- Packets 40-43 are the TCP FIN sequence to end the connection

- What Web Server application is in use here?
Apache

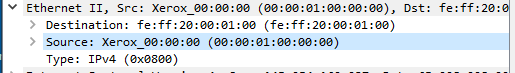
- In the first packet, click on the Ethernet II header
- What is the source MAC address?
00:00:01:00:00:00
- What is the destination Mac address?
fe:ff:20:00:01:00

1d. Statistics: Now let’s explore some statistics of the conversation.

1e. Get a baseline of normal traffic.

IP address spoof:
- Use Wireshark to capture a ping communication between your VM and your host
VM: 192.168.7.82 Host: 192.162.7.103
-
Open up Wireshark with Ethernet0
-
Ping Host with VM


- Capture ping of VM to Host in Wireshark

Spoof
1. Go to the Nmap directory

if you want to get to CMD from a folder you can click on the nav bar and type in CMD


- Run nping -h

- Wireshark capture of nping of WinClone23 (192.168.7.70)
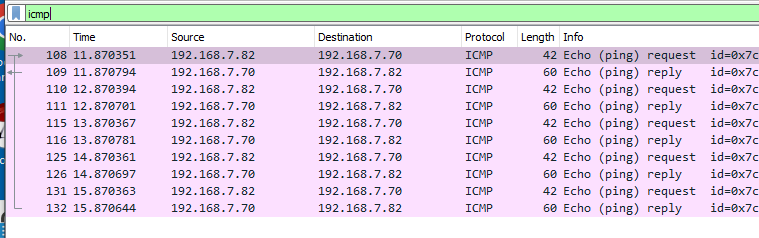
- Professor used my VM Ip address to initiate and I saw the icmp traffic of my professors IP(192.168.7.100) to my IP(192.168.7.82)
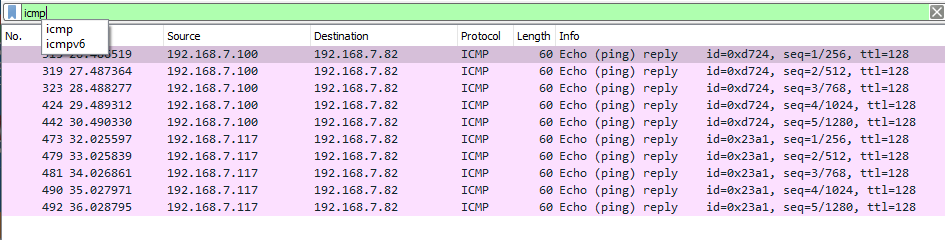
Now, you are going to use another live “spoofed” station’s IP address as the source IP in a ping to your neighbor. Your neighbor will be running Wireshark to capture the ping requests and responses.
- Impersonating James(192.168.7.131) and sending it to Mike (192.168.7.75)

(there are 5 packets lost because the attacker never receives the ping replies)
James spoofing Mikes IP, and using me as a target:
 nping
nping
SYN SCAN/Flood
- Open Zenmap
(can get you in a lot of trouble legally)

- Type in the custom Zenmap command
Me being targeted by Mike

Links used: https://www.hackingarticles.in/understanding-nmap-scan-wireshark/