Firewall Lab - Hsanokklis/2022-2023-Tech-journal GitHub Wiki
Summary: In this lab, you will combine some of the knowledge and skills from previous activities and the information from Chapter 10 on Firewalls. You will have some services running and ports open, scan to make sure they are visible from the outside, then block with firewall rules, and rescan to observe the changes.
Doc Link
1. All of the following are done on your Win 10 VM (not the host machine) & Kali VM. Make sure both VMs are on the same custom VMnets with DHCP enabled.
This is optional, if you do this you can't connect to the internet, so you are able to keep it on bridged as long as you don't scan the whole network
- Edit/Virtual Network Editor to check which VMnet# is host-only with DHCP enabled


- VM/Settings to select that VMnet# for both VMs

2. Start your WIN10 VM and services, & change hostname.
-
right-click Windows Start menu and select System
-
Click Change Settings, Change, then insert your 1st initial + last name for your computer name (i.e. alincoln), and then run the “whoami” command after reboot.

- Make sure your Windows IIS web server is running, and can be reached by your Kali VM.

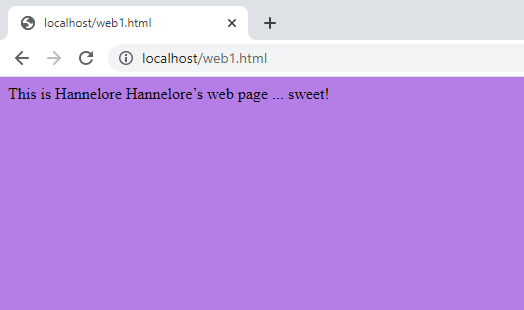

Kali Access to webpage
3. Download & install nmap on the Win10 VM, then open a ncat listener.
https://nmap.org/download.html
4. Start ncat running on port 8082 via command line
- ncat -l 8082 -k -v
The -k option is the keep it running even after a scan hits it
- You should see 2 new ncat inbound rules under Firewall/Advanced Settings

5. Block/allow some rules and then ping your windows machine from your kali machine

I blocked the rule that allows for ping

When I tried to ping my windows machine from my kali, all my packets were lost
6. Scan your Windows VM from your Kali VM using nmap to see what services are running.
- nmap -p 1-8085 –T5 –A Target_IP
The –p option allows you to specify ports, -A enables OS/version detection, and –T5 is set for a speed of “insane”


_This is ncat listening to the nmap
TROUBLESHOOTING: I initially could not get port 8082 to work. I didn't have ncat running on my windows machine, which is hosted by port 8082 which is why it was not working.
On the Win10 VM, create a new firewall rule to block web traffic to your Win10 VM.
- Currently, your Win10VM allows incoming regular web requests via HTTP.
- Now we’re going to test to see if a new Block rule overrules an existing Allow rule.
- In Windows Firewall’s Advanced Settings, create a new rule which blocks all HTTP inbound traffic across all profiles (domain, public & private) named “Blocky” with a description including your first initial and last name.

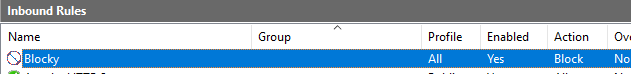
- Now on Kali, test it via its browser with the Win10 VM’s IP. It should not work, and should prove that a Block rule overrides an Allow rule.

without the rule

With the rule
7. change the default HTTP port, & create a new inbound rule for incoming HTTP request.
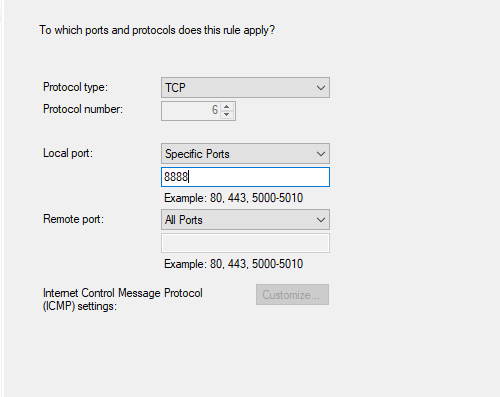
- On the Win10 VM, open the IIS Manager. In the Default Web Site Connection, Edit the Site Bindings from port 80 to 8888.




Change to port 8888


IIS working on port 8888

IIS not working on port 80
8. Snip the successful packet’s details via Wireshark with the IP & port displaying.

