RPZ feeds from ThreatQ - Homas/ioc2rpz GitHub Wiki
Overview
ThreatQ by ThreatQuotient is a Threat Intelligence Platform (TIP) which provides you ability to aggregate, correlate, and analyze threat intelligence from multiple sources. TIP data sharing capabilities are essential for security teams in order to operationalize threat intelligence and enforce security on different security layers including NGFW, SWG, and DNS.
ioc2rpz can be easily integrated with ThreatQ via data export. You can export indicators only (hostnames, domains, IP addresses and subnets) or indicators with expiration date.
Export TI from ThreatQuotient
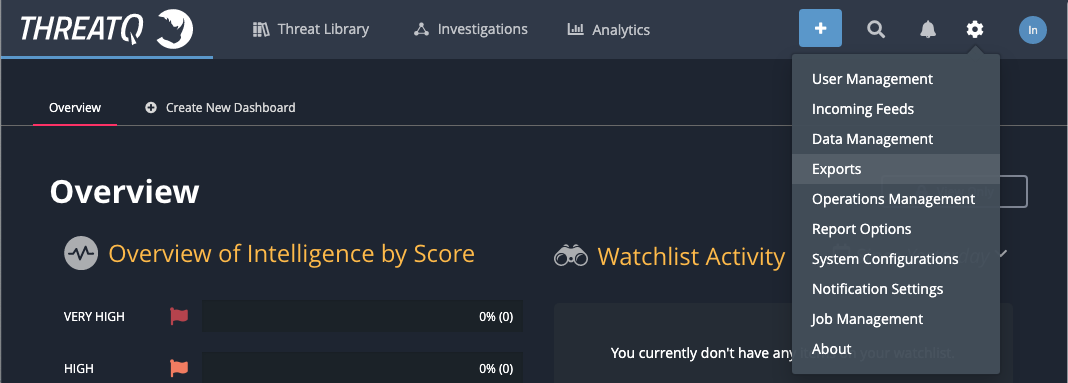
Default Export
ThreatQ provides exports of hostnames and IP-addresses out of the box. It is not recommended to use the default exports in production systems because they export all indicators without filtering and this can lead to blocking benign domains/hosts.
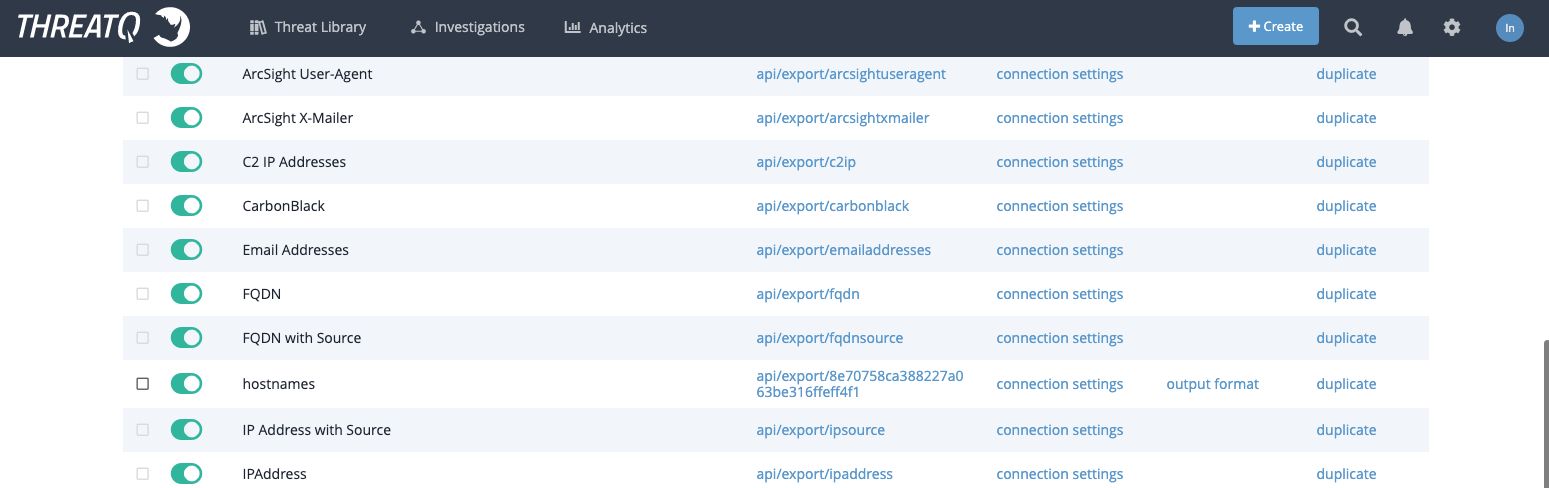
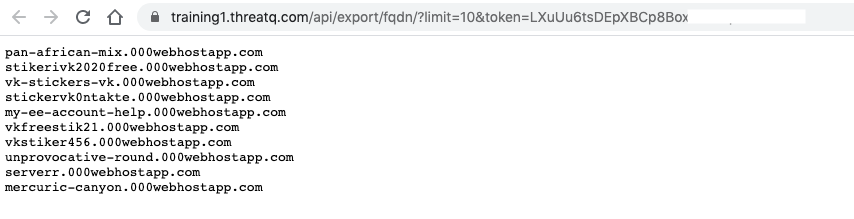
You can use the default exports to check the integration and as a base for a custom exports.
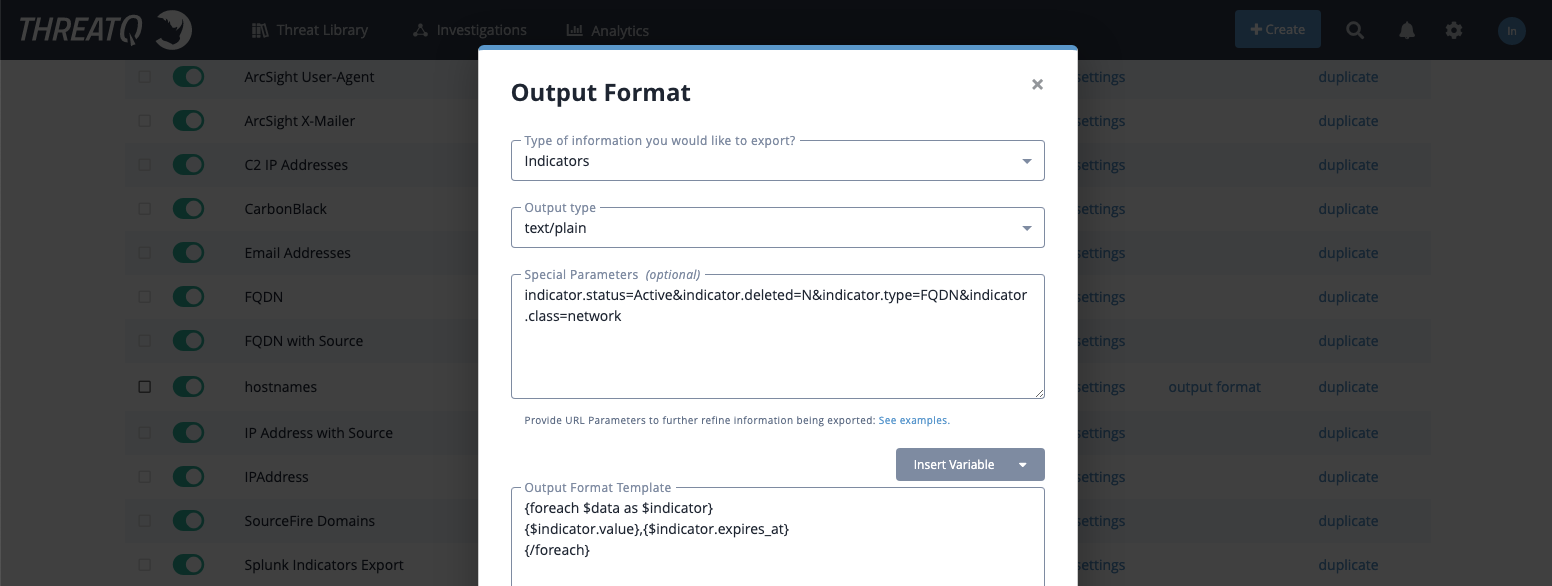
Custom Export
ioc2rpz was tested with up to 50 millions indicators and 100 millions rules (to block a domain and subdomains 2 RPZ rules are required). Larger the feed, more memory and CPU resources are required to generate and maintain an RPZ feed. Before pushing the feed to a DNS server check if it can handle the feed (dependency on memory) and the performance (max QPS).
When you decided on the maximum feed size, use filters to limit the feed content, do not use "limit".
Create Sources and RPZ feeds
To create a source you need to copy the export URL (don't forget to remove limit). ThreatQ supports incremental updates as well as ioc2rpz supports incremental zone transfer. Use incremental updates as much as possible to reduce load on servers and network.
