Lab 6.1 Cracking Linux Passwords with JtR and Hashcat - FlameSpyro/Tech-Journal GitHub Wiki
Cracking Linux Passwords with JtR and Hashcat
How to grab password hashes
- To do this with the shadow users do the following
sudo -i
tail -n 3 /etc/passwd
tail -n 3 /etc/shadow
- The -n option just stands for last lines picked
Hash breakdown
-
For the algorithm being used on the server, it appears that the hashing method used is SHA 512 as this format always starts with $6$.
-
Within the entry, the "salt" is known as the value of random data that is used to combine with the password to increase its strength.
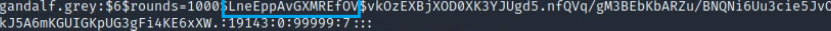
-
Everything after the 4th $ is the hashed salt+password
Unshadow
- To use unshadow in order for a file that is compatible with John the Ripper do the following
unshadow etc-passwd.txt etc_shadow.txt > unshadowed.txt
John the Ripper Cracking
- This process can take AGES if used on a VM so we used the humpty machine to do this. Ill also include how to unzip the rockyou file in this example
ls
gunzip rockyou.txt
cd
cd week6
john unshadowed.txt -wordlist:/usr/share/wordlists/rockyou.txt
john unshadowed.txt --show
Hashcat cracking
hashcat -m 1800 -a 0 -o cracked.txt unshadowed.txt /usr/share/wordlists/rockyou.txt
- -m method/hash type
- -a attack mode
- -o outfile
Reflection
- This lab wasn't really that bad, in fact it was fun! The only "struggle" I had in the lab was getting into the humpty dumpty machine which I fixed by reverting the ssh changes made in the cupcake lab. Might take me some time to get the hang of this all!