Lab 5.1 Wazuh WAF - FlameSpyro/Tech-Journal GitHub Wiki
Lab 5.1 Wazuh WAF
WAN-to-DMZ
- We need to add a new permanent rule to vyos such that established connections from the DMZ-to-WAN are allowed back through the WAN-to-DMZ firewall. If that rule (typically rule 1) is not there, add it.
- Refer to last week to adding rules
- We need to add a temporary rule for software updates that we either delete, disable or discard when complete. This rule should have the following characteristics.
- Set the rule number to 999 or similar
- Set the action to accept (this is wide open)
- Set the source ip address to be the web server
Adding mod_security, the core rule set and php to web01
-
I used the following cmds
sudo yum install mod_security mod_security_crs php php-common php-opcache php-cli php-gd php-curl php-mysqlnd -y -
Deliverable 1. Restart httpd on web01. Provide two screenshots similar to the ones below that shows that the security2_module is loaded.
-
Check by using
cat error_log | grep ModSecurity -
sudo -M | grep security2
Test ModSecurity
- Deliverable 2. Provide a screenshot showing that you can get to web01 from rw01. Make sure you show your are on rw01 (hostname). Depending on the default rules, modsecurity may not allow you to browse by IP. If this happens, figure out how to allow IP's in urls.
hostname
curl HTTP://172.16.50.3
-
Used this through wget to get the code
-
Deliverable 3. Use the php webshell to execute a command like ifconfig, hostname or whoami. Provide a screenshot showing remote code execution like the one below. You may need to be explicit about the path of the program you wish to run
- Going to shell.php allows you to enter
ifconfig /sbin/ifconfig
hostname
whoami
-
Deliverable 4. provide a screenshot that shows what happens when you attempt to run the following command within your webshell.
cat /etc/passwd -
Leads to a forbidden error page
-
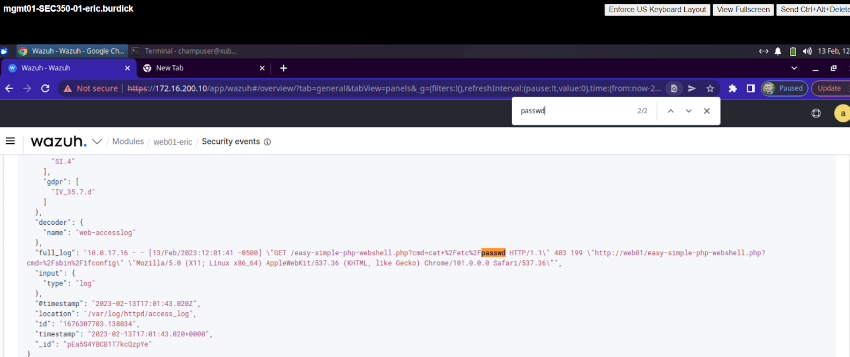
Deliverable 5. Find the error or warning associated with Deliverable 4 in the apache error_log. Provide a screenshot.
-
Refer to logging lab
-
Deliverable 6. Find the same alert in wazuh, provide a screenshot similar to the one below. You will see two types of events. 404 events directly from the apache logs but you should see some modsecurity events as well.