Lab 4.1 Network Firewalls 1 - FlameSpyro/Tech-Journal GitHub Wiki
Lab 4.1 Network Firewalls 1
- In this lab we are going to shut down and then manage traffic between the LAN, DMZ,WAN and MGMT Networks. The initial configuration of fw01 will be illustrated in detail, but you will need to use that information to configure fw-mgmt.
- This Lab can be very tricky and strict in instructions so it may make your head spin!
Lab Review
-
Prerequisites
-
Please Ensure that:
- rw01 can ping web01 via its static route, rw01 can browse to web01
- wks01 can browse web01
- wks01 can browse wazuh
- web01 can ping wazuh
-
Configuring fw01
-
Create and link firewall zones to interfaces (eth0, eth1, eth2)
set zone-policy zone WAN interface eth0set zone-policy zone DMZ interface eth1set zone-policy zone LAN interface eth2- commit and save!
WAN and DMZ
- Observe and repeat the following commands. In the illustration below, we have created firewalls for WAN to DMZ and DMZ to WAN, we are going to lock them down with a default drop directive, and we will log violations of the firewall rules. We have also assigned firewalls to the respective direction of communication between zones.
- Firewalls for WAN and DMZ:
set firewall name WAN-to-DMZ default-action dropset firewall name DMZ-to-WAN default-action dropset firewall name WAN-to-DMZ enable-default-logset firewall name DMZ-to-WAN enable-default-log
- Assigning Firewalls to Zones
set zone-policy zone WAN from DMZ firewall name DMZ-to-WANset zone-policy zone DMZ from WAN firewall name WAN-to-DMZ- commit and save
- Attempt to connect to web01 via rw01, it should fail!
- On fw01, monitor your firewall logs with the following command:
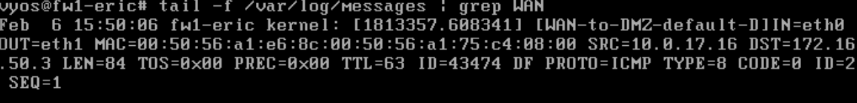
tail -f /var/log/messages | grep WAN
- Deliverable 1: Provide a screenshot showing a [WAN-TO-DMZ-default-D] log entry similar to the one above.
Allow http inbound
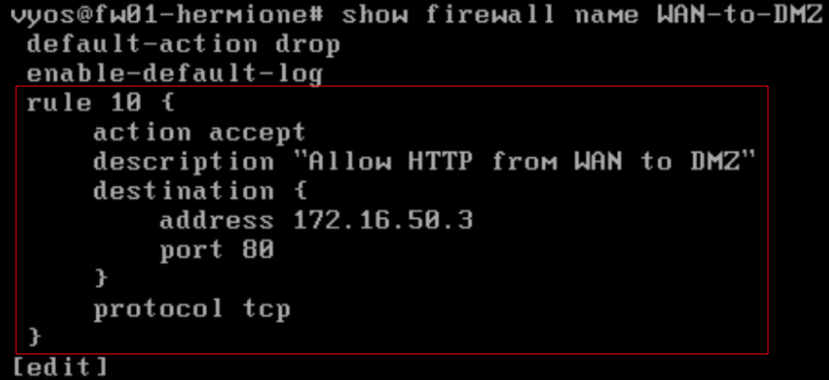
- Allow http traffic from the WAN to the DMZ based web01 using the following syntax, remember you use your IP address for web01.
- How to append rule 10 to the WAN-to-DMZ firewall
configure
set firewall name WAN-to-DMZ rule 10 action accept
set firewall name WAN-to-DMZ rule 10 destination address 172.16.50.3
set firewall name WAN-to-DMZ rule 10 destination port 80
set firewall name WAN-to-DMZ rule 10 protocol tcp
commit
save
- Try to connect via http, the connection should still fail.
- This time the failure is due to another firewall. The communication was stopped on the way back out, not on the way in. We need to explicitly tell the DMZ-TO-WAN firewall to allow established connections initiated from the WAN back out again.
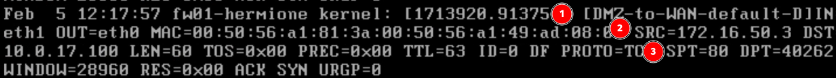
- The rule is DMZ-to-WAN or outbound traffic from the DMZ back to rw01
- The source ip is web01
- The source port is port 80/tcp (the web server response to the wget from rw01)
Allowing established connections back out again.
- The following screenshot shows an updated DMZ-to-WAN firewall rule that will allow connections that were let in the door, back out again.
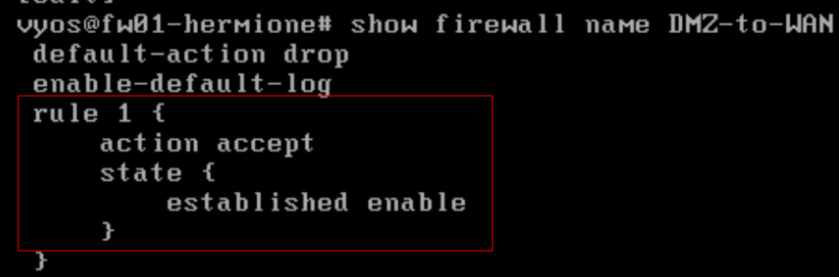
- This is done by entering
configure
set firewall name DMZ-to-WAN rule 1 action accept
set firewall name DMZ-to-WAN rule 1 state established enable
commit
save
show firewall name DMZ-to-WAN
- Deliverable 2: Take a screenshot similar to the one below that shows a failed wget or curl (1) followed by a successful connection to your web server. Make sure you've deleted the default welcome.conf file, you've restarted httpd and have added a simple index.html banner as shown in (2).
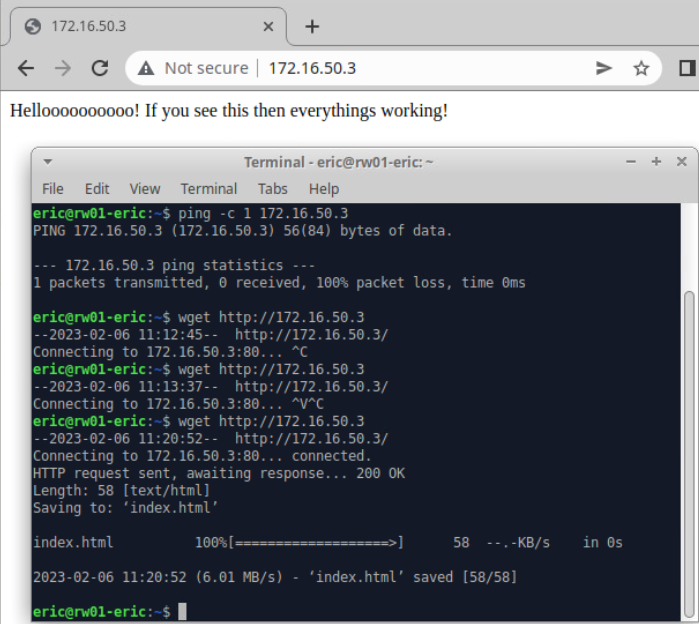
DMZ and LAN Traffic
- We are going to continue our firewalling by creating default firewalls for LAN and DMZ and link them to zone policies.
configure
set firewall name DMZ-to-LAN default-action drop
set firewall name DMZ-to-LAN enable-default-log
set firewall name LAN-to-DMZ default-action drop
set firewall name LAN-to-DMZ enable-default-log
set zone-policy zone LAN from DMZ firewall name DMZ-to-LAN
set zone-policy zone DMZ from LAN firewall name LAN-to-DMZ
commit
save
- Right now we have firewalls whose only rules are to drop everything (except port 80 to web01 from the WAN). We are now going to use debugging techniques shown earlier to find out why our wazuh traffic doesn’t work between DMZ and LAN (actually MGMT, but fw01 does not know about the MGMT network, just the LAN).
- The Wazuh server expects clients to connect to it via tcp/1514 and tcp/1515, this is a good connection to start with. We will examine or logs to see if there are any drop messages for these ports.
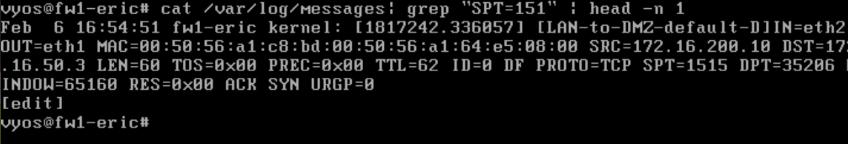
DMZ-to-LAN
- Deliverable 3: Provide a screenshot similar to the one above of /var/log/messages on fw01 that shows a drop message like the one below, make sure you select the message that indicated PROTO=TCP and DPT=1514 or 1515
- To do this:
configure
set firewall name DMZ-to-LAN rule 10 action accept
set firewall name DMZ-to-LAN rule 10 destination address 172.16.200.10
set firewall name DMZ-to-LAN rule 10 destination port 1514
set firewall name DMZ-to-LAN rule 10 protocol udp
commit
save
Allowing established wazuh traffic back
- Try finding LAN-to-DMZ traffic that has been dropped that has a SPT=1514,1515. This is a tcp connection, so we need to allow established back through the related firewall (LAN-to-DMZ)
- Deliverable 4. Provide a screenshot of your new LAN-to-DMZ rule 1 that allows established connections back through the LAN-to-DMZ firewall.
LAN-TO-WAN
- We are receiving complaints from our Burlington-based employees because they cannot surf the internet or listen to Spotify. It is also likely that CRD is no longer working. We need to allow clients to initiate any connections to the WAN. This one requirement can be the Achilles Heel of network security. Clients in this zone typically need to initiate connections in a very permissive manner to do their jobs. We may need to look at supplementary host based controls and restrictive web proxies later.
- Create a default LAN to WAN firewall and associate it with the appropriate zone policy. This firewall will have only one rule allowing LAN clients to initiate WAN connections.
WAN-TO-LAN
- Create the WAN-TO-LAN firewall, link it to the appropriate zones and allow established connections back from WAN to LAN
configure
set firewall name LAN-to-WAN default-action drop
set firewall name LAN-to-WAN enable-default-log
set firewall name LAN-to-WAN rule 1 action accept
commit
save
show firewall name LAN-to-WAN
- Deliverable 5: Submit a screenshot showing a LAN-TO-WAN browsing session between wks01 and champlain.edu
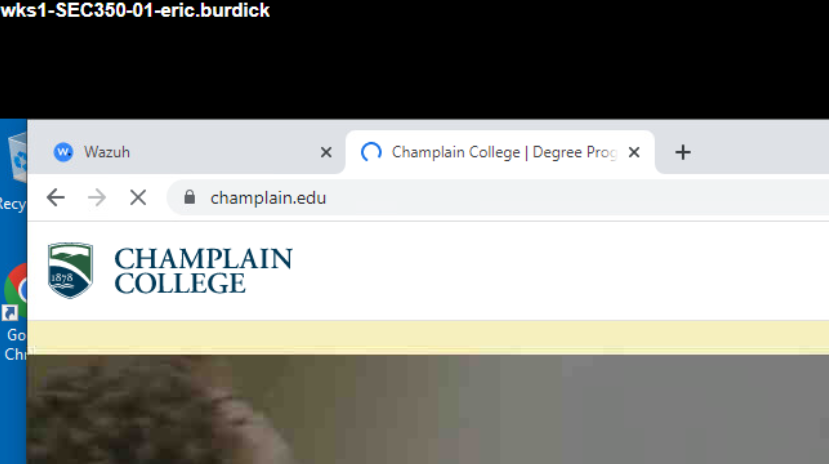
LAN to DMZ
- As communication between LAN and DMZ is currently broken, we need to create a firewall, assign to the appropriate zone policy and adjust it to only allow the traffic we want to go through. We want wks01 to be able to browse to web01 and we want mgmt01 to ssh into anything on the DMZ.
- With that in mind, create firewall rules on LAN-TO-DMZ that allows
- 80/tcp from LAN to web01.
- 22/tcp from mgmt01 to the DMZ
configure
set firewall name LAN-to-DMZ rule 10 action accept
set firewall name LAN-to-DMZ rule 10 destination address 172.16.50.3
set firewall name LAN-to-DMZ rule 10 destination port 80
set firewall name LAN-to-DMZ rule 10 protocol tcp
set firewall name LAN-to-DMZ rule 10 description "Allow LAN access to Web01 HTTP"
commit
save
set firewall name DMZ-to-LAN rule 1 action accept
set firewall name DMZ-to-LAN rule 1 state established enable
commit
save
-
Deliverable 6: Screenshot showing web session between wks01 and web01.
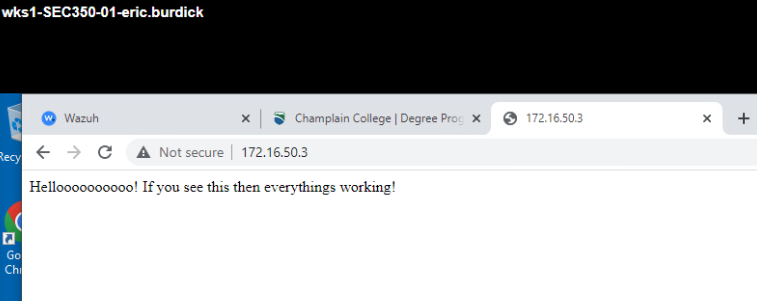
-
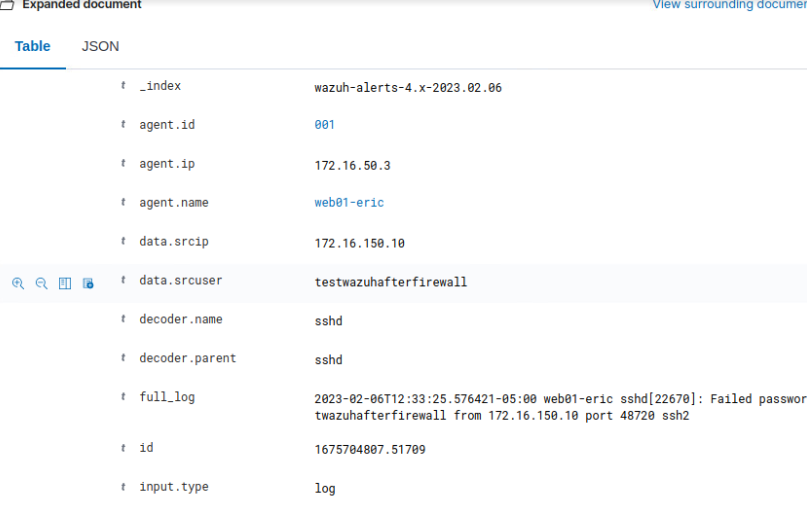
Deliverable 7. ssh into web01 from using the username testwazuhafterfirewall. Attempt this until the session is closed by web01. Provide a screenshot similar to the one below that shows a related security event in wazuh, after fw1 was configured.
Configuring fw-mgmt
- Now that you have the basics of zone and firewall configuration under your belt, you are going to use the techniques shown above in configuration of fw-mgmt.
- Create a LAN-to-MGMT firewall that:
- Allows 1514,1515/tcp from LAN to wazuh
- Allows 443/tcp from mgmt01 on LAN to wazuh
- Allows 22/tcp from mgmt01 on LAN to wazuh
- Allows established traffic back through the related firewall
set firewall name LAN-to-MGMT default-action 'drop'
set firewall name LAN-to-MGMT enable-default-log
set firewall name LAN-to-MGMT rule 1 action 'accept'
set firewall name LAN-to-MGMT rule 1 state established 'enable'
set firewall name LAN-to-MGMT rule 10 action 'accept'
set firewall name LAN-to-MGMT rule 10 description 'wazuh agent traffice to
wazuh'
set firewall name LAN-to-MGMT rule 10 destination address '172.16.200.10'
set firewall name LAN-to-MGMT rule 10 destination port '1514,1515'
set firewall name LAN-to-MGMT rule 10 protocol 'tcp'
set firewall name LAN-to-MGMT rule 20 action 'accept'
set firewall name LAN-to-MGMT rule 20 description 'MGMT01 tls to wazuh'
set firewall name LAN-to-MGMT rule 20 destination address '172.16.200.10'
set firewall name LAN-to-MGMT rule 20 destination port '443'
set firewall name LAN-to-MGMT rule 20 protocol 'tcp'
set firewall name LAN-to-MGMT rule 30 action 'accept'
set firewall name LAN-to-MGMT rule 30 description 'MGMT01 ssh to wazuh'
set firewall name LAN-to-MGMT rule 30 destination address '172.16.200.10'
set firewall name LAN-to-MGMT rule 30 destination port '22'
set firewall name LAN-to-MGMT rule 30 protocol 'tcp'
set firewall name MGMT-to-LAN default-action 'drop'
set firewall name MGMT-to-LAN description 'MGMT access to LAN'
set firewall name MGMT-to-LAN enable-default-log
set firewall name MGMT-to-LAN rule 1 action 'accept'
set firewall name MGMT-to-LAN rule 1 state established 'enable'
set firewall name MGMT-to-LAN rule 10 action 'accept'
set firewall name MGMT-to-LAN rule 10 description 'MGMT access to DMZ'
set firewall name MGMT-to-LAN rule 10 destination address '172.16.50.0/29'
set firewall name MGMT-to-LAN rule 20 action 'accept'
set firewall name MGMT-to-LAN rule 20 description 'MGMT access to LAN'
set firewall name MGMT-to-LAN rule 20 destination address '172.16.150.0/24'
-
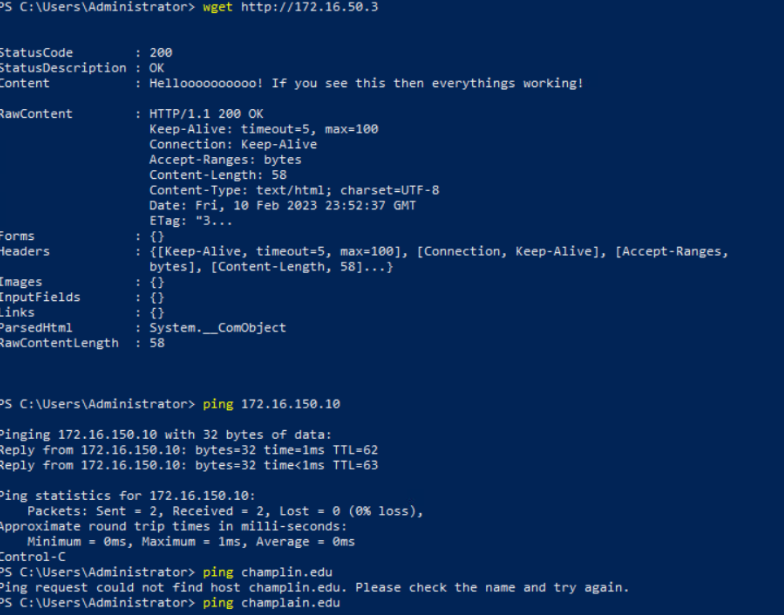
If you do this right, you should be able to connect from mgmt02 to the DMZ like so.
- wget to web01
- ping to mgmt01
- ping outside will fail because you didn't explicitly allow MGMT to go anywhere but LAN and DMZ.
-
Deliverable 8. Provide a screenshot similar to the one below
-
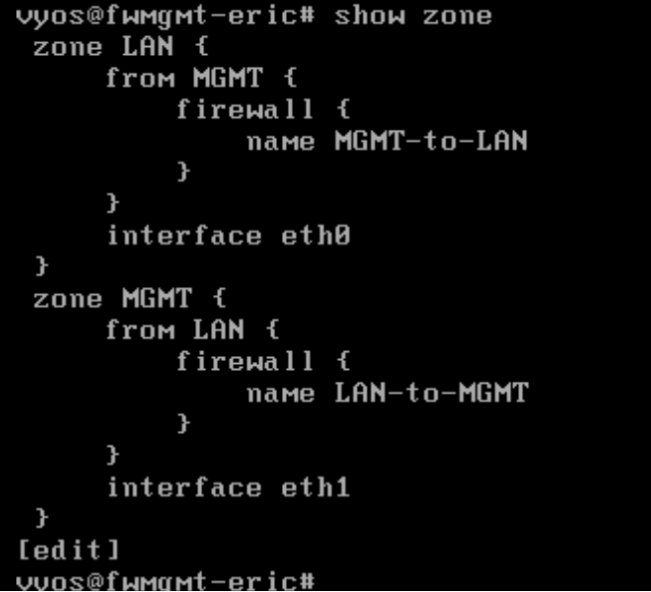
Deliverable 9. Provide the output of: show zone on fw-mgmt
-
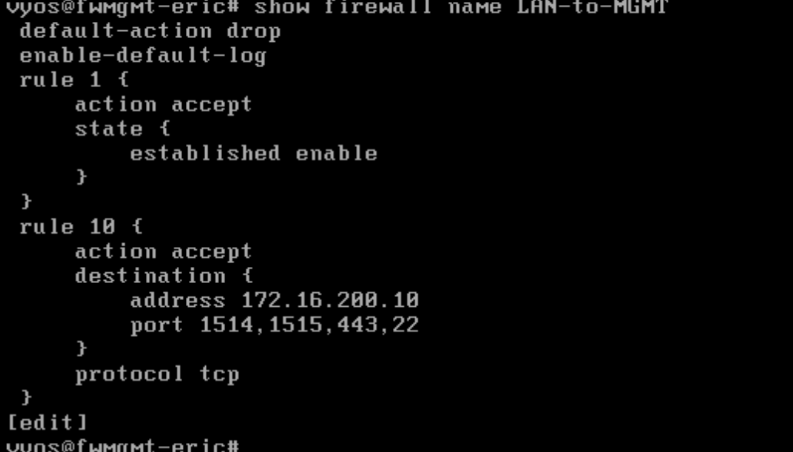
Deliverable 10. Provide the output of: show firewall name LAN-TO-MGMT
-
Deliverable 11. Provide the output of: show firewall name MGMT-TO-LAN
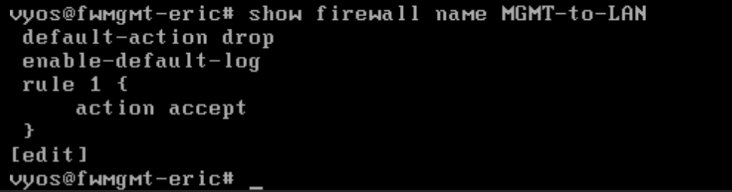
-
Deliverable 12. From mgmt01, Run an ssh test on web01 with a tag that indicates that this is a test of fw-mgmt. Take a screenshot of the resulting log within wazuh.
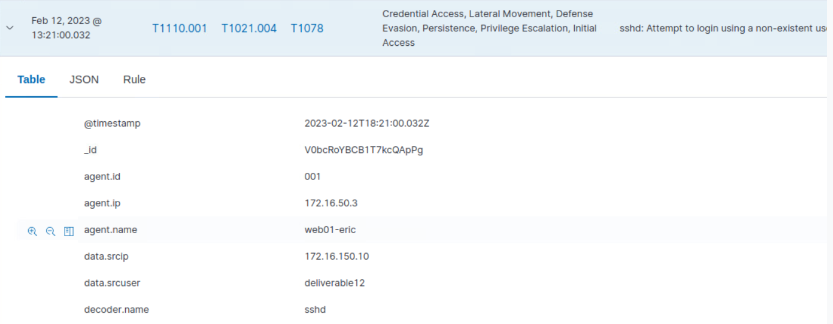
Final Thoughts
- This lab is a toughie, it can get really confusing with all of the settings and different firewalls needed to be managed at once but practice can help get things down pat! Apologies to future me if this wiki isnt helpful.