SEC 350 Lab 4.1 Network Firewalls - DefiantCoder/Tech-Journals GitHub Wiki
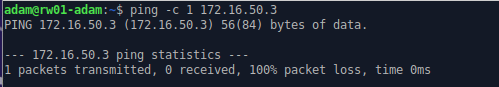
Before the lab Check if these are successful
- rw01 can ping web01 via its static route, rw01 can browse to web01
- wks01 can browse web01
- wks01 can browse wazuh
- web01 can ping wazuh
fw01 config
set zone-policy zone WAN interface eth0
set zone-policy zone DMZ interface eth1
set zone-policy zone LAN interface eth2
commit save
WAN and DMZ
set firewall name WAN-to-DMZ default-action drop
set firewall name DMZ-to-WAN default-action drop
set firewall name WAN-to-DMZ enable-default-log
set firewall name DMZ-to-WAN enable-default-log
Assigning Firewalls to Zones
set zone-policy zone WAN from DMZ firewall name DMZ-to-WAN
set zone-policy zone DMZ from WAN firewall name WAN-to-DMZ
commit
save
- on fw01 run the following
tail -f /var/log/messages | grep WAN
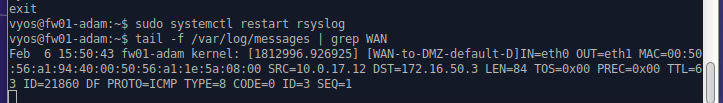
WAN-to-DMZ rules
configure
set firewall name WAN-to-DMZ rule 10 action accept
set firewall name WAN-to-DMZ rule 10 destination address 172.16.50.3
set firewall name WAN-to-DMZ rule 10 destination port 80
set firewall name WAN-to-DMZ rule 10 protocol tcp
set firewall name WAN-to-DMZ rule 10 description "Allow HTTP from WAN to DMZ"
commit
save
DMZ-to-WAN firewall rule
configure
set firewall name DMZ-to-WAN rule 1 action accept
set firewall name DMZ-to-WAN rule 1 state established enable
commit
save
- Zones
set zone-policy zone LAN from DMZ firewall name DMZ-to-LAN
set zone-policy zone DMZ from LAN firewall name LAN-to-DMZ
LAN to DMZ
set firewall name LAN-to-DMZ default-action drop
set firewall name DMZ-to-LAN default-action drop
set firewall name LAN-to-DMZ enable-default-log
set firewall name DMZ-to-LAN enable-default-log
set zone-policy zone LAN from DMZ firewall name DMZ-to-LAN
set zone-policy zone DMZ from LAN firewall name LAN-to-DMZ
commit
save
Firewall Rules
set firewall name LAN-to-DMZ rule 20 action accept
set firewall name LAN-to-DMZ rule 20 description "LAN to web01"
set firewall name LAN-to-DMZ rule 20 destination address 172.16.50.3
set firewall name LAN-to-DMZ rule 20 destination port 80
set firewall name LAN-to-DMZ rule 20 protocol tcp
commit
save
set firewall name LAN-to-DMZ rule 30 action accept
set firewall name LAN-to-DMZ rule 30 description "mgmt01 to DMZ"
set firewall name LAN-to-DMZ rule 30 destination address 172.16.50.3
set firewall name LAN-to-DMZ rule 30 destination port 22
set firewall name LAN-to-DMZ rule 30 protocol tcp
commit
save
set firewall name DMZ-to-LAN rule 1 action accept
set firewall name DMZ-to-LAN rule 1 state established enable
commit
save
set firewall name DMZ-to-LAN rule 10 action accept
set firewall name DMZ-to-LAN rule 10 description "wazuh agent communications with wazuh server"
set firewall name DMZ-to-LAN rule 10 destination address 172.16.200.10
set firewall name DMZ-to-LAN rule 10 destination port 1514,1515
set firewall name DMZ-to-LAN rule 10 protocol tcp
commit
save
LAN to WAN
set firewall name LAN-to-WAN default-action drop
set firewall name WAN-to-LAN default-action drop
set firewall name LAN-to-WAN enable-default-log
set firewall name WAN-to-LAN enable-default-log
set zone-policy zone LAN from WAN firewall name WAN-to-LAN
set zone-policy zone WAN from LAN firewall name LAN-to-WAN
commit
save
Firewall rules
set firewall name LAN-to-WAN rule 1 action accept
commit
save
set firewall name WAN-to-LAN rule 1 action accept
set firewall name WAN-to-LAN rule 1 state established enable
commit
save
fw-mgmt Config
set zone-policy zone LAN interface eth0
set zone-policy zone MGMT interface eth1
commit
save
LAN & MGMT
set firewall name LAN-to-MGMT default-action drop
set firewall name MGMT-to-LAN default-action drop
set firewall name LAN-to-MGMT enable-default-log
set firewall name MGMT-to-LAN enable-default-log
commit
save
set zone-policy zone LAN from MGMT firewall name MGMT-to-LAN
set zone-policy zone MGMT from LAN firewall name LAN-to-MGMT
commit
save
MGMT to LAN
set firewall name LAN-to-MGMT rule 10 action accept
set firewall name LAN-to-MGMT rule 10 destination address 172.16.200.10
set firewall name LAN-to-MGMT rule 10 destination port 1514,1515
set firewall name LAN-to-MGMT rule 10 protocol tcp
commit
save
set firewall name LAN-to-MGMT rule 20 action accept
set firewall name LAN-to-MGMT rule 20 description "allow established connections through"
set firewall name LAN-to-MGMT rule 20 destination address 172.16.200.10
set firewall name LAN-to-MGMT rule 20 destination port 443
set firewall name LAN-to-MGMT rule 20 protocol tcp
set firewall name LAN-to-MGMT rule 1 action accept
set firewall name LAN-to-MGMT rule 1 state established enable
commit
save
LAN to MGMT
set firewall name MGMT-to-LAN rule 10 action accept
set firewall name MGMT-to-LAN rule 10 description MGMT to all of LAN
set firewall name MGMT-to-LAN rule 10 destination address 172.16.150.0/24
commit
save
set firewall name MGMT-to-LAN rule 20 action 'accept'
set firewall name MGMT-to-LAN rule 20 description 'MGMT to all of DMZ'
set firewall name MGMT-to-LAN rule 20 destination address '172.16.50.0/29'
set firewall name MGMT-to-LAN rule 1 action 'accept'
set firewall name MGMT-to-LAN rule 1 state established 'enable'
commit
save
commit
save
Exporting VyOS Config
show configuration commands | grep -v "syslog global\|ntp\|login\|console\|config\|hw-id\|loopback\|conntrack"
Firewall Configs
Reflection
Overall this was not a very difficult lab, but it was a very long lab with a Massive amount of documentation required. I learn a lot while running through this lab when it comes to firewalls and building a network. This lab challenged me with working with a large amount of config and changes and debugging when a typo occured.