11.1 Cisco Access List Configs - DefiantCoder/Tech-Journals GitHub Wiki
Cisco Access List Documentation
Standard ACLs can filter traffic based on source IP address only. A typical best practice is to configure a standard ACL as close to the destination as possible.
Remember that every ACL has an implicit “deny all” that causes all traffic that has not matched a statement in the ACL to be blocked. For this reason, add the permit any statement to the end of the ACL.
- Copy & Paste template
enable
config t
! The Router interface leading to or from what we are permitting/blocking
interface <OutsideInterface>
! You can apply a filter for a specific flow of traffic (in or out) that the ACL will be applied to
ip access-list standard <YourListName> (in or out)
(permit or deny) <network address> <wildcard mask>
(permit or deny) host <ip address>
Examples:
enable
config t
interface Serial0/0/0
ip access-list standard aList
deny 192.168.1.0 0.0.0.255
deny host 192.168.1.11
permit any
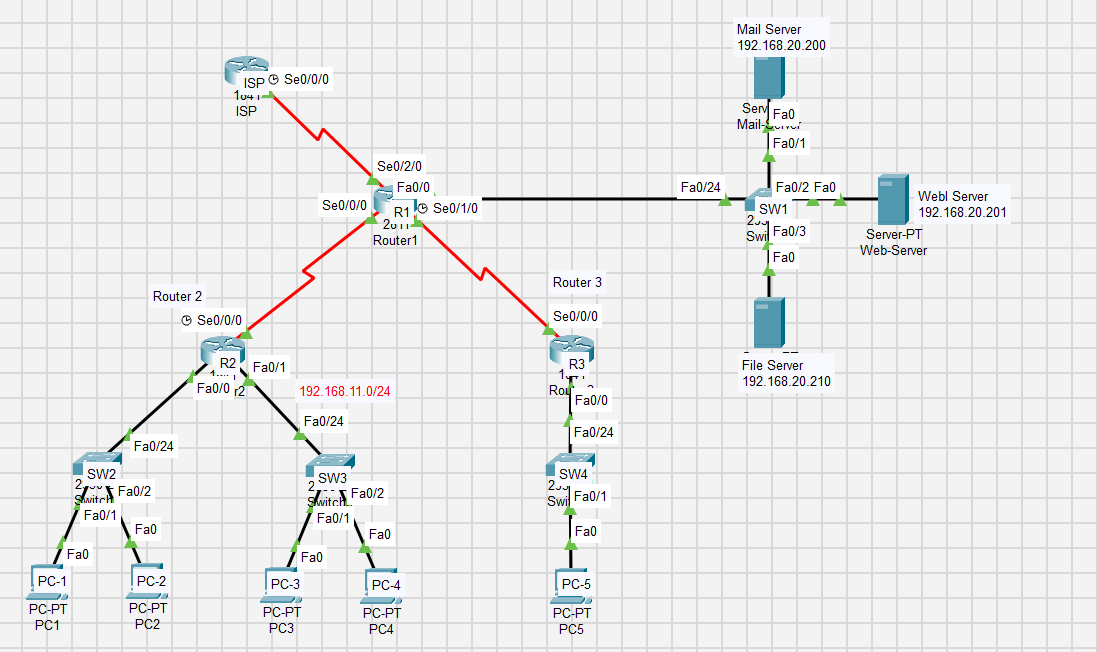
- This was run on Router3 to block Router2 Fa0/1 Traffic
enable
config t
interface Serial0/0/0
ip access-list standard STND-1
deny 192.168.11.0 0.0.0.255
Used for more specific filtering
Extended ACLs can filter on protocol, source, and destination IP addresses, and source and destination port numbers.
A typical best practice for applying extended ACLs is to place them as close to the source as possible.
Extended ACL Documentation & Available Protocol Syntax
Copy & Paste Template
enable
config t
! The Router interface leading to or from what we are permitting/blocking
interface <Router_Interface>
! You can apply a filter for a specific flow of traffic (in or out) that the ACL will be applied to
ip access-list extended <name of list> (in or out)
(permit or deny) <protocol> <Source_IP> <wildcard_mask> <Destination_IP> <wildcard_mask> [eq <port/service>]
permit ip any any
Examples:
enable
config t
interface FastEthernet0/1
ip access-list extended Extendo
deny tcp host 192.168.1.5 host 10.10.1.4 eq 80
deny tcp 10.0.0.0 0.0.0.255 10.0.1.0 0.0.0.255 eq 22
permit ip any any
This case blocks Router1 and it's desktops from the internet (200.200.200.1)
enable
config t
interface Serial0/0/0
ip access-list extended EXTEND-1
deny tcp 192.168.10.0 0.0.0.255 host 200.200.200.1 eq 80
When putting the destination IP address you do not need a wildcard subnet as shown below
enable
config t
interface Serial0/0/0
ip access-list extended FileS-1
deny tcp host 192.168.20.210 0.0.0.255 200.200.200.1 eq 80
Issues:
I ran the command but forgot to select my interface so It didn't work I realized my issue later when re-reading the instructions so I used interface Serial0/0/0. I added a wildcard subnet after the ISP address during the bonus ACL's and couldn't figure out the problem until I came back the next day and looked at it. Throughout this assignment I ran into numerous issues with packet tracer and the testing software. Many times it would close the window I am working on and crash. I do not understand this software, when I had the first deliverable working properly it said it was incorrect but when it is improperly setup and pc3 can ping pc5 it is saying that it is correct.