enable
conf t
hostname YourHostname-router
! Interface setup for middle (isp in example) connection to DestinationHostname-Router
! Outside connection Ethernet connection
interface FastEthernet 0/0
ip address <Public IP address> <subnet>
no shutdown
! Interface setup for Private Champlain
interface FastEthernet 0/1
ip address 192.168.25.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 <middle Router IP address (your default Gateway)>
! Identify traffic to send through tunnel with access-list
access-list <YourChoiceNum> permit ip <Source_Private Net IP> <wildcard subnet> <Destination_Private Net IP> <wildcard subnet>
! Configure IKE Phase 1 ISAKMP Policy on Middlebury Router
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
exit
crypto isakmp key <YourAuthenticationKey> address <Destination_Public IP>
! Configure the IKE Phase 2 IPsec policy
!- Create the transform-set "VPN-SET"
crypto ipsec transform-set VPN-SET esp-aes esp-sha-hmac
!- Create the crypto map "VPN-MAP"
crypto map VPN-MAP 10 ipsec-isakmp
description VPN connection to Champlain
set peer <Destination_Public IP>
set transform-set VPN-SET
match address 101
exit
! Configure the "crypto map" on the outgoing interface.
interface FastEthernet 0/0
crypto map VPN-MAP
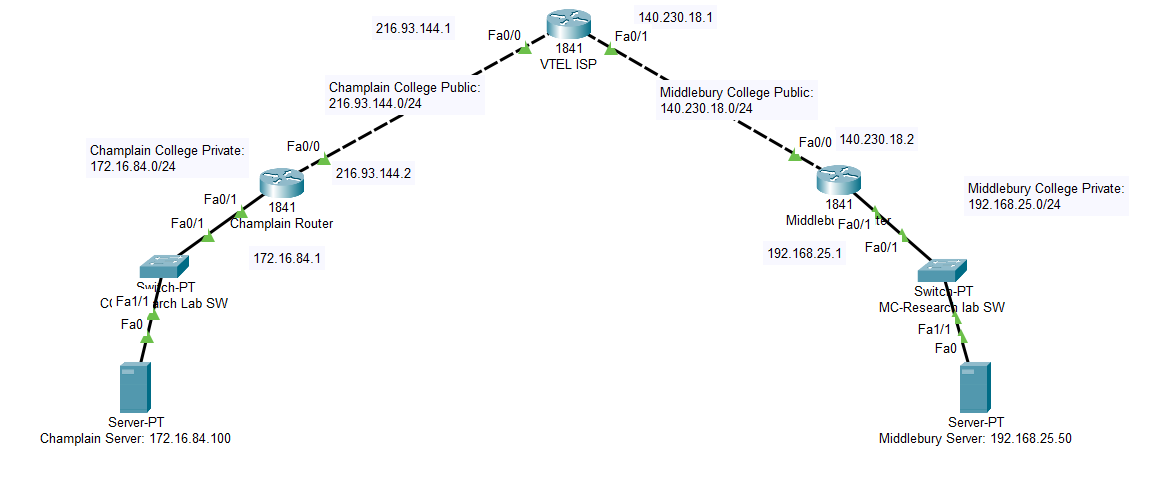
Example lab config (Champlain side)
enable
conf t
hostname champlain-router
! Interface setup for VTEL to Champlain
interface FastEthernet 0/0
ip address 216.93.144.2 255.255.255.0
no shutdown
! Interface setup for internal Champlain
interface FastEthernet 0/1
ip address 172.16.84.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 216.93.144.1
! Identify traffic to send through tunnel with access-list
access-list 101 permit ip 172.16.84.0 0.0.0.255 192.168.25.0 0.0.0.255
! Configure IKE Phase 1 ISAKMP Policy on Champlain Router
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
exit
crypto isakmp key NET330 address 140.230.18.2
! Configure the IKE Phase 2 IPsec policy
!- Create the transform-set "VPN-SET"
crypto ipsec transform-set VPN-SET esp-aes esp-sha-hmac
!- Create the crypto map "VPN-MAP"
crypto map VPN-MAP 10 ipsec-isakmp
description VPN connection to Middlebury
set peer 140.230.18.2
set transform-set VPN-SET
match address 101
exit
! Configure the "crypto map" on the outgoing interface.
interface FastEthernet 0/0
crypto map VPN-MAP
- You then do the same but inverse IP's for Middlebury
enable
conf t
hostname middlebury-router
! Interface setup for VTEL to Middlebury
interface FastEthernet 0/0
ip address 140.230.18.2 255.255.255.0
no shutdown
! Interface setup for internal Champlain
interface FastEthernet 0/1
ip address 192.168.25.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 140.230.18.1
! Identify traffic to send through tunnel with access-list
access-list 101 permit ip 192.168.25.0 0.0.0.255 172.16.84.0 0.0.0.255
! Configure IKE Phase 1 ISAKMP Policy on Middlebury Router
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
exit
crypto isakmp key NET330 address 216.93.144.2
! Configure the IKE Phase 2 IPsec policy
!- Create the transform-set "VPN-SET"
crypto ipsec transform-set VPN-SET esp-aes esp-sha-hmac
!- Create the crypto map "VPN-MAP"
crypto map VPN-MAP 10 ipsec-isakmp
description VPN connection to Champlain
set peer 216.93.144.2
set transform-set VPN-SET
match address 101
exit
! Configure the "crypto map" on the outgoing interface.
interface FastEthernet 0/0
crypto map VPN-MAP
