10.1 Linux Permission Vulnerabilities - DefiantCoder/Tech-Journals GitHub Wiki
#include <stdlib.h>
#include <pwd.h>
#include <stdio.h>
#include <unistd.h>
/*
SEC335 Illustrate SUID Programs
* based on: https://stackoverflow.com/questions/8953424/how-to-get-the-username-in-c-c-in-linux
* Make sure run the following
* sudo chown root:root nameofprogram
* sudo chmod u+s nameofprogram
* makes a **.c program**
*/
int main(int argc, char *argv[])
{
struct passwd *pw;
uid_t uid;
uid = geteuid ();
pw = getpwuid (uid);
if (pw)
{
puts (pw->pw_name);
exit (EXIT_SUCCESS);
}
else
{
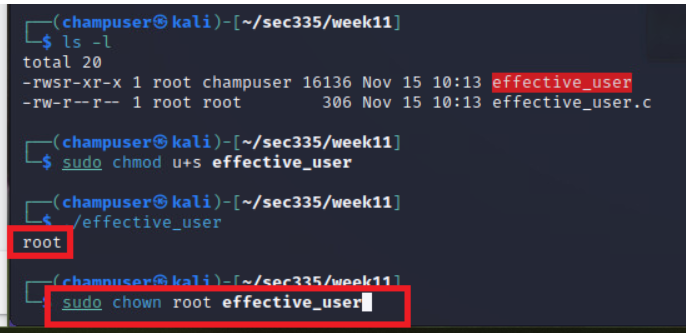
Run these commands to find the effective user when running a command, gcc compiles the program. If you sudo ./nameofprogram you will return root
gcc nameofprogram -o nameofprogram
./nameofprogram
This will change the owner to root and then make the program a suid binary program, this can be useful as a pen tester
sudo chown root:root nameofprogram
sudo chmod u+s nameofprogram
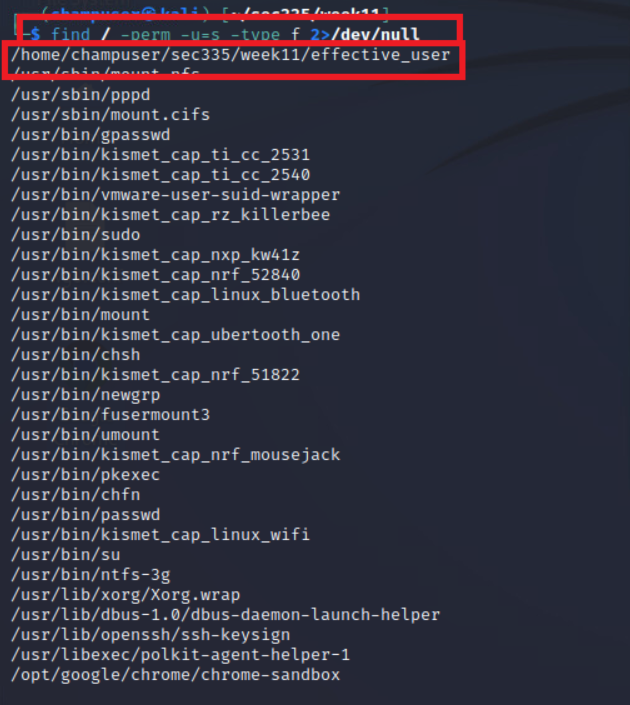
This useful command can find suid programs across the internet
find / -perm -u=s -type f 2>/dev/null
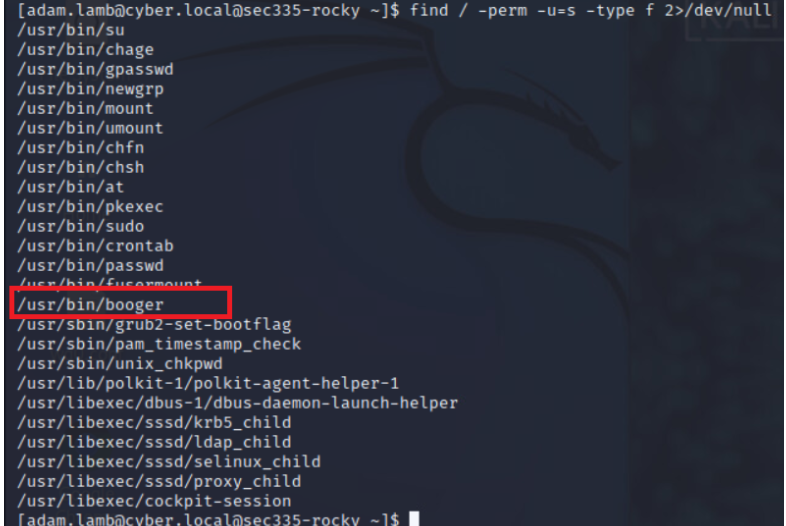
Using this command on other machines can help to find other programs as shown:
/usr/bin/booger
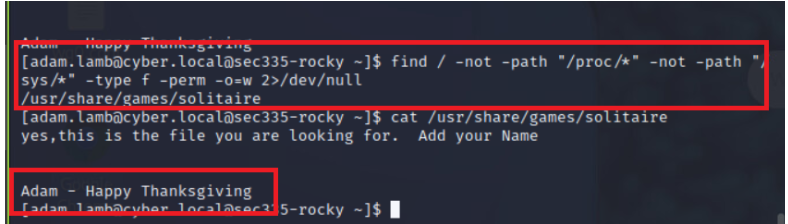
This find comman differs with -o=w which can be helpful to filter all files writable by the other groups/users.
find /etc -perm -o=w -type f 2>/dev/null
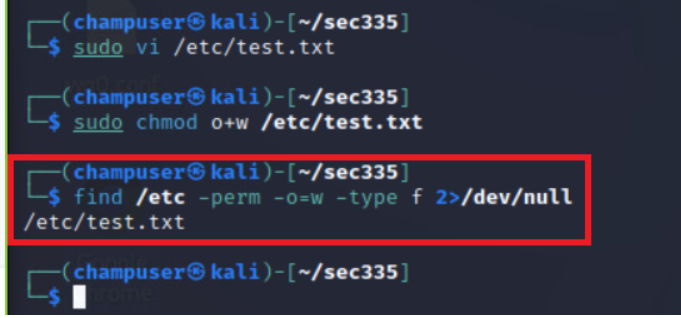
This command requires modification for uses outside this specific use case but is very useful for finding a world writable file
-
-not -path "/proc/*" -not -path "/sys/*"this is specific to this use case as these directories gave us false positives
find / -not -path "/proc/*" -not -path "/sys/*" -type f -perm -o=w 2>/dev/null