Authentification process - DLR-SC/DataFinder GitHub Wiki
After accessing the DataFinder server, it might be needed, to access other systems (e.g other servers), that require different authentification. The authentification information should not be stored with the datafinder configuration, therefore a new approach needs to be developed and different authentication mechanisms provided.
Requirements
-
Different ways to authenticate:
-
user password
-
Authentication using Grid certificates:
-
using public key infrastructure(see above)
-
none
-
Edit authentication information (preferences page)
-
Make a default for certificate based authentication or ldap authentication (???)
-
saving authentication information - or links to a certificate
- keyCzar as key store implementation (link see below)
-
making certificate information available for signing content or for encrypting it
Open Questions:
- Generally Shibbolise !DataFinder?
- Why Shibboleth?
- meaning to have one single sign on?! or actually using shibboleth?
- using Shibboleth is task of the it Manager in an organizatinonal structure (can not imagine how to fit it into the datafinder)
Design ideas outline
General
- on datafinder server side:
- configure authentication mechanisms (what store needs what kind of authentication in order to work properly --> not providing a password but the initial information)
- try to figure out, what the server wants and needs and then provide the right interface for it
- in user client: catch the authentication request
- Possibility to point to a certificate in wizard, the certificate needs to be checked
User Interface
- three places for authentication:
- preferences page/wizard: list with all saved authentication mechanisms and passwords (?)
- connection wizard to connect to datafinder configuration
- connection wizard to connect to storage server via different authentication mechanisms (see above)
Approaches
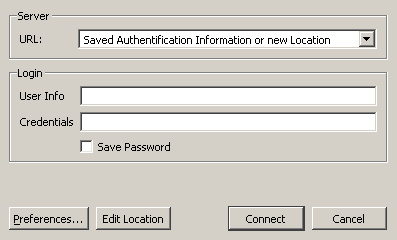
authentification-connect-dialog:
When clicking on preferences the ldap information window opens. When clicking on Edit the "authentification-edit-wizard" opens.
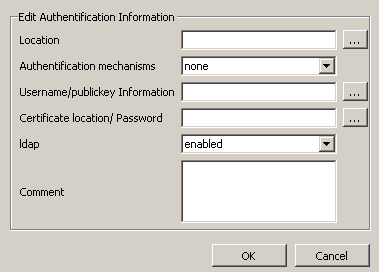
authentification-edit-dialog:
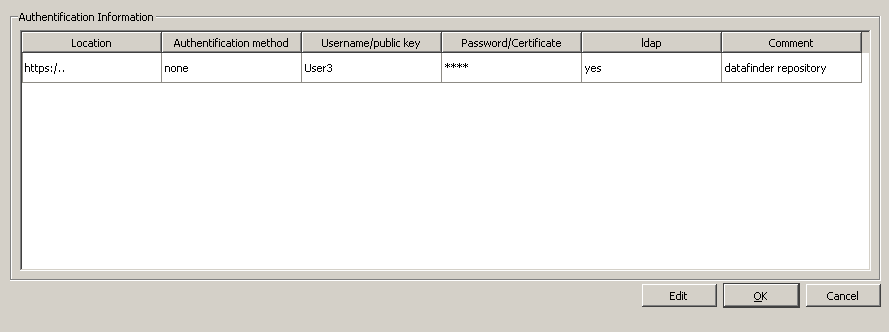
authentification-preference-wizard:
When clicking on edit, the authentification-edit-wizard opens
Internals
- using a keystore to store passwords, certificates (also grid/proxy certificates) --> e.g. keyczar
- does the work of keeping it save and helps encrypting things
Solution
affected classes
- src.datafinder.persistence.privileges.privilegestorer ( Defines interface and default implementation for privilege-/ACL-related actions.)
Some links
crypptography modules for python:
- Cryptography and Python - workshop paper
- PyCrypto Toolktit -- python library
- cryptopy -- python library
- keyCzar -- open source cryptographic toolkit, initiated by the Google Security Team
- M2Crypto -- OpenSSL wrapper for Python, crypto toolkit for Python, using SWIG to tie to native libraries
- pyGlobus -- binding of GT to Python using SWIG (can also create proxy certificates, like )
- pyGridWare -- more Python Globus goodness
Dependent Feature
Cloud Integration: Launchpad