Project 3 Threat Hunting - Cyber-JL/SEC-350-01 GitHub Wiki
APT43, also known as Kimsuky, is a well-known and large threat actor group that is state-backed by North Korea. The group's technical capabilities are sophisticated using very aggressive social engineering tactics. APT43 has had a large focus on South Korean and U.S. government organizations, academics, and think tanks that focus on geopolitical issues within Korea as well as foreign policy and nuclear security issues.
The group specializes in espionage and cybercrime with the goal of collecting strategic intelligence. The group uses credential harvesting, social engineering, the use of spoofed domains and email addresses, and Domains masquerading as legitimate sites, as well as deploying malware. In 2018 APT43 used compromised sites as part of network infrastructure to deliver both PASSMARK and LATEOP malware, in 2021 APT43 conducted a credential harvesting campaign against religious groups, universities, and non-governmental organizations.
In 2022 the threat actor has observed harvesting credentials targeting academics, journalists, politicians, bloggers, and other private sector individuals. APT43, in the height of COVID-19, employed malware that had been used by Lazarus. The group also uses tools that are publicly available including Invoke-Mimikatz, METASPLOIT, and QUASARRAT which are the main focus of the simulated attack.
- kali and attack network

-
Initial Access
- T1566 Phishing: achieved through manipulation of nginx site
-
Resource Development
- T1584 Compromise Infrastructure: achieved through manipulation of nginx site
-
Execution
- T1059 Command and Scripting Interpreter
- T1059.001 PowerShell
- T1059.003 Windows Command Shell
- T1204.002 Malicious File
-
Command and Control
- T1105 Ingress Tool Transfer: done through kali box
- metasploit
- mimikatz
- Remote Access Trojan (RAT)
-
In the
/var/ossec/etc/decoders/local_decoder.xmlfile add the following custom decoders:# This extracts information from the YARA scan results <decoder name="yara_decoder"> <prematch>wazuh-yara:</prematch> </decoder> <decoder name="yara_decoder1"> <parent>yara_decoder</parent> <regex>wazuh-yara: (\S+) - Scan result: (\S+) (\S+)</regex> <order>log_type, yara_rule, yara_scanned_file</order> </decoder> -
In the
/var/ossec/etc/rules/local_rules.xmladd the following custom rules:# FOR LINUX <group name="syscheck,"> <rule id="100300" level="7"> <if_sid>550</if_sid> <field name="file">/root/</field> <description>File modified in /root directory.</description> </rule> <rule id="100301" level="7"> <if_sid>554</if_sid> <field name="file">/root/</field> <description>File added to /root directory.</description> </rule> </group> <group name="yara,"> <rule id="108000" level="0"> <decoded_as>yara_decoder</decoded_as> <description>Yara grouping rule</description> </rule> <rule id="108001" level="12"> <if_sid>108000</if_sid> <match>wazuh-yara: INFO - Scan result: </match> <description>File "$(yara_scanned_file)" is a positive match. Yara rule: $(yara_rule)</description> </rule> # FOR WINDOWS Replace <USER_NAME> with the username of the endpoint. <group name="syscheck,"> <rule id="100303" level="7"> <if_sid>550</if_sid> <field name="file">C:\\Users\\<USER_NAME>\\Downloads</field> <description>File modified in C:\Users\<USER_NAME>\Downloads directory.</description> </rule> <rule id="100304" level="7"> <if_sid>554</if_sid> <field name="file">C:\\Users\\<USER_NAME>\\Downloads</field> <description>File added to C:\Users\<USER_NAME>\Downloads directory.</description> </rule> </group> <group name="yara,"> <rule id="108000" level="0"> <decoded_as>yara_decoder</decoded_as> <description>Yara grouping rule</description> </rule> <rule id="108001" level="12"> <if_sid>108000</if_sid> <match>wazuh-yara: INFO - Scan result: </match> <description>File "$(yara_scanned_file)" is a positive match. Yara rule: $(yara_rule)</description> </rule> </group> -
Edit the
/var/ossec/etc/ossec.confand Configure the execution of the YARA script when files are added or modified to a monitored directory by adding the following:# FOR LINUX <ossec_config> <command> <name>yara_linux</name> <executable>yara.sh</executable> <extra_args>-yara_path /usr/local/bin -yara_rules /tmp/yara/rules/yara_rules.yar</extra_args> <timeout_allowed>no</timeout_allowed> </command> <active-response> <command>yara_linux</command> <location>local</location> <rules_id>100300,100301</rules_id> </active-response> </ossec_config> # FOR WINDOWS <ossec_config> <command> <name>yara_windows</name> <executable>yara.bat</executable> <timeout_allowed>no</timeout_allowed> </command> <active-response> <command>yara_windows</command> <location>local</location> <rules_id>100303,100304</rules_id> </active-response> </ossec_config> -
Restart the Wazuh manager to apply the configuration changes:
sudo systemctl restart wazuh-manager -
Download the malware samples to the /root/ directory of the monitored endpoint to test the rules:
sudo curl https://wazuh-demo.s3-us-west-1.amazonaws.com/mirai --output /root/mirai sudo curl https://wazuh-demo.s3-us-west-1.amazonaws.com/xbash --output /root/Xbash
-
Download, compile, and install YARA:
sudo apt update sudo apt install -y make gcc autoconf libtool libssl-dev pkg-config sudo curl -LO https://github.com/VirusTotal/yara/archive/v4.2.3.tar.gz sudo tar -xvzf v4.2.3.tar.gz -C /usr/local/bin/ && rm -f v4.2.3.tar.gz cd /usr/local/bin/yara-4.2.3/ sudo ./bootstrap.sh && sudo ./configure && sudo make && sudo make install && sudo make check -
Download YARA detection rules:
sudo mkdir -p /tmp/yara/rules sudo curl 'https://valhalla.nextron-systems.com/api/v1/get' \ -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' \ -H 'Accept-Language: en-US,en;q=0.5' \ --compressed \ -H 'Referer: https://valhalla.nextron-systems.com/' \ -H 'Content-Type: application/x-www-form-urlencoded' \ -H 'DNT: 1' -H 'Connection: keep-alive' -H 'Upgrade-Insecure-Requests: 1' \ --data 'demo=demo&apikey=1111111111111111111111111111111111111111111111 111111111111111111&format=text' \ -o /tmp/yara/rules/yara_rules.yar -
Create a /var/ossec/active-response/bin/yara.sh file and add the content below. This is the active response script that executes YARA scans when FIM detects changes in the monitored directory:
#!/bin/bash # Wazuh - Yara active response # Copyright (C) 2015-2022, Wazuh Inc. # # This program is free software; you can redistribute it # and/or modify it under the terms of the GNU General Public # License (version 2) as published by the FSF - Free Software # Foundation. #------------------------- Gather parameters -------------------------# # Extra arguments read INPUT_JSON YARA_PATH=$(echo $INPUT_JSON | jq -r .parameters.extra_args[1]) YARA_RULES=$(echo $INPUT_JSON | jq -r .parameters.extra_args[3]) FILENAME=$(echo $INPUT_JSON | jq -r .parameters.alert.syscheck.path) # Set LOG_FILE path LOG_FILE="logs/active-responses.log" size=0 actual_size=$(stat -c %s ${FILENAME}) while [ ${size} -ne ${actual_size} ]; do sleep 1 size=${actual_size} actual_size=$(stat -c %s ${FILENAME}) done #----------------------- Analyze parameters -----------------------# if [[ ! $YARA_PATH ]] || [[ ! $YARA_RULES ]] then echo "wazuh-yara: ERROR - Yara active response error. Yara path and rules parameters are mandatory." >> ${LOG_FILE} exit 1 fi #------------------------- Main workflow --------------------------# # Execute Yara scan on the specified filename yara_output="$("${YARA_PATH}"/yara -w -r "$YARA_RULES" "$FILENAME")" if [[ $yara_output != "" ]] then # Iterate every detected rule and append it to the LOG_FILE while read -r line; do echo "wazuh-yara: INFO - Scan result: $line" >> ${LOG_FILE} done <<< "$yara_output" fi exit 0; -
Change the script ownership and permissions with the following commands:
sudo chmod 750 /var/ossec/active-response/bin/yara.sh sudo chown root:wazuh /var/ossec/active-response/bin/yara.sh -
Install the jq utility to process the JSON data from the FIM alerts:
sudo apt install -y jq -
Add the following within the
<syscheck>block of the Wazuh agent/var/ossec/etc/ossec.confconfiguration file to monitor the/root/directory:/root/
-
Restart the Wazuh agent to apply the configuration changes:
sudo systemctl restart wazuh-agent
-
Download Python executable installer the official Python website.
-
Run the Python installer once downloaded and make sure to check the following boxes:
`Install launcher for all users` `Add Python 3.X to PATH.` This places the interpreter in the execution path. -
Download and install the latest Visual C++ Redistributable package.
-
Open PowerShell with administrator privileges to download and extract YARA:
Invoke-WebRequest -Uri https://github.com/VirusTotal/yara/releases/download/v4.2.3/yara-4.2.3-2029-win64.zip - OutFile v4.2.3-2029-win64.zip Expand-Archive v4.2.3-2029-win64.zip; Remove-Item v4.2.3-2029-win64.zip -
Create a directory called C:\Program Files (x86)\ossec-agent\active-response\bin\yara\ and copy the YARA executable into it:
mkdir 'C:\Program Files (x86)\ossec-agent\active-response\bin\yara\' cp .\v4.2.3-2029-win64\yara64.exe 'C:\Program Files (x86)\ossec-agent\active-response\bin\yara\' -
Install the valhallaAPI module:
pip install valhallaAPI -
Copy the following script and save it as download_yara_rules.py:
from valhallaAPI.valhalla import ValhallaAPI v = ValhallaAPI(api_key="1111111111111111111111111111111111111111111111111111111111111111") response = v.get_rules_text() with open('yara_rules.yar', 'w') as fh: fh.write(response) -
Run the following commands to download the rules and place them in the
C:\Program Files (x86)\ossec-agent\active-response\bin\yara\rules\ directory:python.exe download_yara_rules.py mkdir 'C:\Program Files (x86)\ossec-agent\active-response\bin\yara\rules\' cp yara_rules.yar 'C:\Program Files (x86)\ossec-agent\active-response\bin\yara\rules\' -
Create the yara.bat script in the
C:\Program Files (x86)\ossec-agent\active-response\bin\directory. This is necessary for the Wazuh-YARA active response scans:@echo off setlocal enableDelayedExpansion reg Query "HKLM\Hardware\Description\System\CentralProcessor\0" | find /i "x86" > NUL && SET OS=32BIT || SET OS=64BIT if %OS%==32BIT ( SET log_file_path="%programfiles%\ossec-agent\active-response\active-responses.log" ) if %OS%==64BIT ( SET log_file_path="%programfiles(x86)%\ossec-agent\active-response\active-responses.log" ) set input= for /f "delims=" %%a in ('PowerShell -command "$logInput = Read-Host; Write-Output $logInput"') do ( set input=%%a ) set json_file_path="C:\Program Files (x86)\ossec-agent\active-response\stdin.txt" set syscheck_file_path= echo %input% > %json_file_path% for /F "tokens=* USEBACKQ" %%F in (`Powershell -Nop -C "(Get-Content 'C:\Program Files (x86)\ossec-agent\active-response\stdin.txt'|ConvertFrom-Json).parameters.alert.syscheck.path"`) do (set syscheck_file_path=%%F) del /f %json_file_path% set yara_exe_path="C:\Program Files (x86)\ossec-agent\active-response\bin\yara\yara64.exe" set yara_rules_path="C:\Program Files (x86)\ossec-agent\active-response\bin\yara\rules\yara_rules.yar" echo %syscheck_file_path% >> %log_file_path% for /f "delims=" %%a in ('powershell -command "& \"%yara_exe_path%\" \"%yara_rules_path%\" \"%syscheck_file_path%\""') do (echo wazuh-yara: INFO - Scan result: %%a >> %log_file_path%) exit /b -
Add the
C:\Users\<USER_NAME>\Downloadsdirectory for monitoring within the<syscheck>block in the Wazuh agent configuration fileC:\Program Files (x86)\ossec-agent\ossec.conf. Replace<USER_NAME>with the username of the endpoint:<directories realtime="yes">C:\Users\<USER_NAME>\Downloads</directories> -
Restart the Wazuh agent to apply the configuration changes:
Restart-Service -Name wazuh
-
In
C:\Program Files (x86)\ossec-agent\ossec.confadd the following:<localfile> <location>Security</location> <log_format>eventlog</log_format> </localfile> <localfile> <location>Microsoft-Windows-PrintService/Operational</location> <log_format>eventchannel</log_format> </localfile> <localfile> <location>Powershell</location> <log_format>eventchannel</log_format> </localfile> <localfile> <location>Terminal Services</location> <log_format>eventchannel</log_format> </localfile> <localfile> <location>Remote Access</location> <log_format>eventchannel</log_format> </localfile>
-
in
/var/ossec/etc/rules/local_rules.xmladd the following# Configuring the alert severity for the monitored files <rule id="100345" level="12"> <if_group>syscheck</if_group> <match>/var/www/html/index.nginx-debian.html</match> <description>Changes to /var/www/html/index.nginx-debian.html - Critical file!</description> </rule>
-
in
/var/ossec/etc/ossec.confadd the following:# Configuring syscheck <syscheck> <directories check_all="yes">/etc,/usr/bin,/usr/sbin</directories> <directories check_all="yes">/root/users.txt,/bsd,/root/db.html</directories> </syscheck> <syscheck> <directories check_all="yes">/home/*/Downloads</directories> </syscheck> # Configuring reporting new files <syscheck> <alert_new_files>yes</alert_new_files> </syscheck>
-
In
C:\Program Files (x86)\ossec-agent\ossec.confadd the following:# Configuring Windows registry <syscheck> <windows_registry arch="both" check_all="yes">HKEY_LOCAL_MACHINE\SOFTWARE</windows_registry> <windows_registry arch="32bit" check_all="no" check_mtime="yes">HKEY_LOCAL_MACHINE\SYSTEM\Setup</windows_registry> </syscheck> # Configuring reporting file and registry value changes <syscheck> <directories check_all="yes" realtime="yes" report_changes="yes">/test</directories> <windows_registry arch="64bit" report_changes="yes">HKEY_LOCAL_MACHINE\SYSTEM\Setup</windows_registry> </syscheck>
-
in
/var/ossec/etc/rules/local_rules.xmladd the following# File integrity monitoring and threat detection rules <group name="linux, webshell, windows,"> <!-- This rule detects file creation. --> <rule id="100500" level="12"> <if_sid>554</if_sid> <field name="file" type="pcre2"> ( i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field> <description>[File creation]: Possible web shell scripting file ($(file)) created</description> <mitre> <id>T1105</id> <id>T1505</id> </mitre> </rule> <!-- This rule detects file modification. --> <rule id="100501" level="12"> <if_sid>550</if_sid> <field name="file" type="pcre2">(?i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field> <description>[File modification]: Possible web shell content added in $(file)</description> <mitre> <id>T1105</id> <id>T1505</id> </mitre> </rule> <!-- This rule detects files modified with PHP web shell signatures. --> <rule id="100502" level="15"> <if_sid>100501</if_sid> <field name="changed_content" type="pcre2">(?i)passthru|exec|eval|shell_exec|assert|str_rot13|system|phpinfo|base64_decode|chmod|mkdir|fopen|fclose|readfile|show_source|proc_open|pcntl_exec|execute|WScript.Shell|WScript.Network|FileSystemObject|Adodb.stream</field> <description>[File Modification]: File $(file) contains a web shell</description> <mitre> <id>T1105</id> <id>T1505.003</id> </mitre> </rule> </group>
-
in
/var/ossec/etc/ossec.confadd the following:# Rootkits behavior detection <rootcheck> <rootkit_files>etc/shared/rootkit_files.txt</rootkit_files> <rootkit_trojans>etc/shared/rootkit_trojans.txt</rootkit_trojans> </rootcheck>
-
Install auditd
apt-get install auditd -
in
/var/ossec/etc/ossec.confadd the following:<localfile> <log_format>audit</log_format> <location>/var/log/audit/audit.log</location> </localfile> -
Restart the agent
systemctl restart wazuh-agent
-
in
/var/ossec/etc/rules/local_rules.xmladd the following# Monitor running Windows processes <rule id="100010" level="6"> <if_sid>530</if_sid> <match>^ossec: output: 'tasklist'</match> <description>Important process not running.</description> <group>process_monitor,</group> </rule> <rule id="100011" level="0"> <if_sid>100010</if_sid> <match>notepad.exe</match> <description>Processes running as expected</description> <group>process_monitor,</group> </rule> # Disk space utilization <rule id="531" level="7" ignore="7200"> <if_sid>530</if_sid> <match>ossec: output: 'df -P': /dev/</match> <regex>100%</regex> <description>Partition usage reached 100% (disk space monitor).</description> <group>low_diskspace,pci_dss_10.6.1,</group> </rule> # Check if the output changed <rule id="533" level="7"> <if_sid>530</if_sid> <match>ossec: output: 'netstat listening ports</match> <check_diff /> <description>Listened ports status (netstat) changed (new port opened or closed).</description> <group>pci_dss_10.2.7,pci_dss_10.6.1,gpg13_10.1,gdpr_IV_35.7.d,</group> </rule> # Load average <rule id="100101" level="7" ignore="7200"> <if_sid>530</if_sid> <match>ossec: output: 'uptime': </match> <regex>load average: 2.</regex> <description>Load average reached 2..</description> </rule>
-
in
/var/ossec/etc/ossec.confadd the following:# Disk space utilization <localfile> <log_format>command</log_format> <command>df -P</command> </localfile> # Check if the output changed <localfile> <log_format>full_command</log_format> <command>netstat -tulpn | sed 's/\([[:alnum:]]\+\)\ \+[[:digit:]]\+\ \+[[:digit:]]\+\ \+\(.*\):\([[:digit:]]*\)\ \+\([0-9\.\:\*]\+\).\+\ \([[:digit:]]*\/[[:alnum:]\-]*\).*/\1 \2 == \3 == \4 \5/' | sort -k 4 -g | sed 's/ == \(.*\) ==/:\1/' | sed 1,2d</command> <alias>netstat listening ports</alias> <frequency>360</frequency> </localfile> # Load average <localfile> <log_format>command</log_format> <command>uptime</command> </localfile>
-
In
C:\Program Files (x86)\ossec-agent\ossec.confadd the following:# monitor windows commands <localfile> <log_format>full_command</log_format> <command>tasklist</command> <frequency>120</frequency> </localfile>






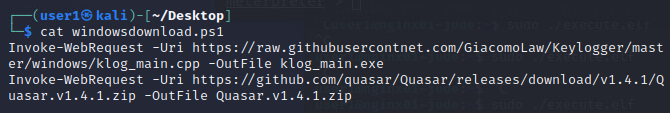
-
To download run the following:
git clone https://github.com/t3l3machus/Villain cd ./Villain pip3 install -r requirements.txt




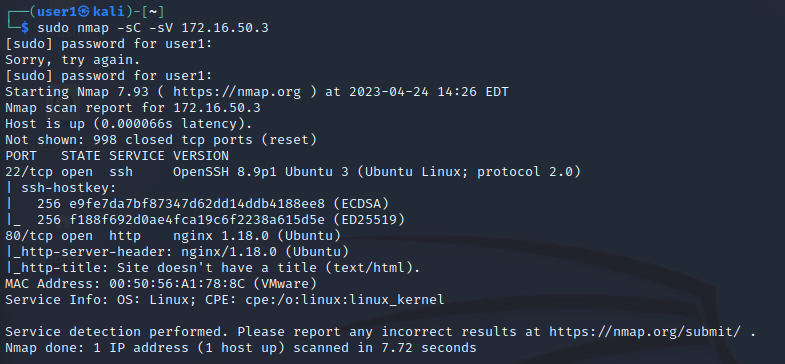



- Note there is use of both Villain and Metasploit as a backdoor throught the attack this will be indicated.























- Edg01 through metasploit backdoor via nginx01



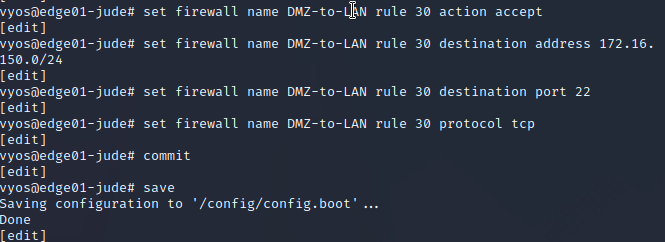


























































- https://mandiant.widen.net/s/zvmfw5fnjs/apt43-report
- https://attack.mitre.org/groups/G0094/
- https://blog.alyac.co.kr/2234
- https://www.cybereason.com/blog/research/back-to-the-future-inside-the-kimsuky-kgh-spyware-suite
- https://www.malwarebytes.com/blog/threat-intelligence/2021/06/kimsuky-apt-continues-to-target-south-korean-government-using-appleseed-backdoor
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa20-301a
- https://www.netscout.com/blog/asert/stolen-pencil-campaign-targets-academia
- https://global.ahnlab.com/global/upload/download/techreport/[Analysis_Report]Operation%20Kabar%20Cobra.pdf
- https://blog.talosintelligence.com/kimsuky-abuses-blogs-delivers-malware/
- https://www.virusbulletin.com/virusbulletin/2020/03/vb2019-paper-kimsuky-group-tracking-king-spearphishing/
- https://securelist.com/the-kimsuky-operation-a-north-korean-apt/57915/
- https://www.kali.org/tools/mimikatz/
- https://www.liquidweb.com/kb/how-to-install-and-use-mimikatz/
- https://documentation.wazuh.com/current/user-manual/index.html
- https://wazuh.com/blog/how-to-integrate-yara-with-wazuh/
- https://documentation.wazuh.com/current/user-manual/capabilities/malware-detection/fim-yara.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/detect-malware-yara-integration.html
- https://documentation.wazuh.com/current/user-manual/capabilities/log-data-collection/how-to-collect-wlogs.html
- https://documentation.wazuh.com/current/user-manual/capabilities/file-integrity/fim-configuration.html
- https://documentation.wazuh.com/current/user-manual/capabilities/file-integrity/fim-configuration.html#configuring-reporting-new-files
- https://documentation.wazuh.com/current/user-manual/capabilities/malware-detection/index.html
- https://documentation.wazuh.com/current/user-manual/capabilities/system-calls-monitoring/audit-configuration.html
- https://documentation.wazuh.com/current/user-manual/capabilities/command-monitoring/command-configuration.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/audit-commands-run-by-user.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/poc-detect-trojan.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/poc-detect-trojan.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/integrate-network-ids-suricata.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/detect-unauthorized-processes-netcat.html
- https://documentation.wazuh.com/current/proof-of-concept-guide/poc-file-integrity-monitoring.html
- https://documentation.wazuh.com/current/user-manual/ruleset/index.html
- https://github.com/gentilkiwi/mimikatz/releases
- https://book.hacktricks.xyz/windows-hardening/stealing-credentials
- https://cheats.philkeeble.com/active-directory/mimikatz
- https://github.com/t3l3machus/Villain
- https://github.com/quasar/Quasar
- https://phoenixnap.com/kb/how-to-install-a-gui-on-ubuntu
- https://itsfoss.com/install-xfce-desktop-xubuntu/
- https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/networking_guide/sec-configuring_a_multihomed_dhcp_server
- https://ubuntu.com/server/docs/network-dhcp
- https://help.ubuntu.com/community/isc-dhcp-server?_ga=2.44141857.406777474.1682005490-1166046634.1677778999
- https://ubuntu.com/server/docs/network-dhcp
- https://askubuntu.com/questions/601882/how-to-setup-multi-dhcp-server
- https://askubuntu.com/questions/601882/how-to-setup-multi-dhcp-server
- https://unix.stackexchange.com/questions/33376/debian-dhcpd-no-subnet-declaration-for-eth0
- https://www.offsec.com/metasploit-unleashed/meterpreter-basics/
- https://docs.rapid7.com/metasploit/meterpreter-getsystem/
- https://www.offsec.com/metasploit-unleashed/mimikatz/
- https://pentesthacker.wordpress.com/2020/12/27/meterpreter-hash-dump-with-windows-10/
- https://docs.metasploit.com/docs/using-metasploit/basics/how-to-use-a-reverse-shell-in-metasploit.html
- https://infinitelogins.com/2020/01/25/msfvenom-reverse-shell-payload-cheatsheet/
- https://docs.metasploit.com/docs/using-metasploit/basics/how-to-use-a-reverse-shell-in-metasploit.html
- https://www.offsec.com/metasploit-unleashed/generating-payloads/
- https://www.geeksforgeeks.org/working-with-payload-metasploit-in-kali-linux/
- https://www.offsec.com/metasploit-unleashed/modules-and-locations/