Wazuh Setup - Berrym-tech/Sec-350 GitHub Wiki
Commands
- ping -c1 google.com
Firewall Commands on fw01
- set protocols rip interface eth2
- set protocols rip network 172.16.50.0/29
Firewall Commands on fw-mgmt
- set protocols rip interface eth0
- set protocols rip network '172.16.200.0/28'
- set nat source rule 30 description "NAT FROM MGMT to WAN"
- set nat source rule 30 outbound-interface eth0 set nat source rule 30 source address 172.16.200.0/28
- set nat source rule 30 translation address masquerade
- commit
- save
- show configuration commands | grep -v "syslog global|ntp|login|console|config|hw-id|loopback|conntrack"
IP Config Commands on Wazuh
- nano /etc/netplan/00-installer-config.yaml Should look similar to
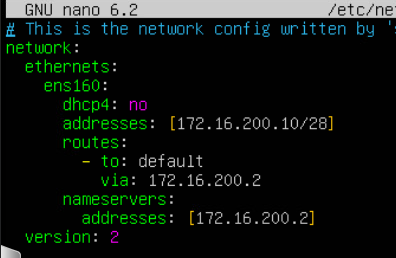
Commands to run on Wazuh
- curl -sO https://packages.wazuh.com/4.3/wazuh-install.sh && sudo bash ./wazuh-install.sh -a On MGMT you can now browse to the Wazuh site using the Wazuh IP address and login info shown below.
Login
User: admin Password: 1A7cR3Bj7bWc,esX7K8zz4u2D*Yka03b
After login
After you login you can create new groups and new agents that you can assign to those groups as shown below.
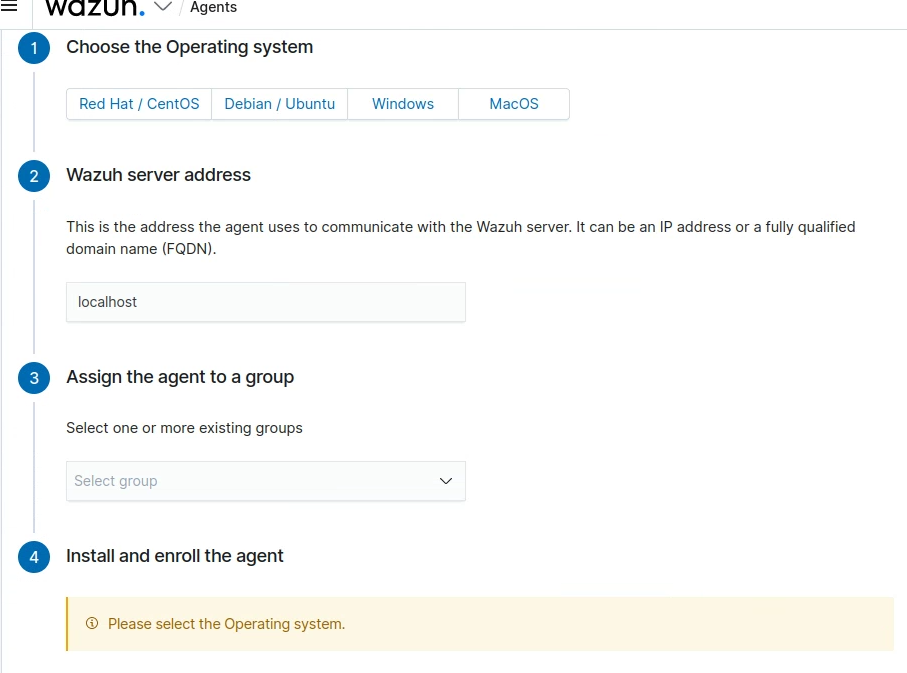
 After completing this, you can connect those agents to a server through the enable, start and status systemctl commands.
After completing this, you can connect those agents to a server through the enable, start and status systemctl commands.
Logging
Finally you can now get logs from your server and you can see security alerts and do alert monitoring.