GitHub Actions - Azure/AzOps GitHub Wiki
Before you start, make sure you have followed the steps in the prerequisites article to configure the required permissions for AzOps.
If you are planning to use self-hosted runners, also verify that all required software is installed on your runners.
For those using GitHub Enterprise Server (GHES), AzOps is supported with GitHub Enterprise Server version 3.4.0 or newer.
Links to documentation for further reading:
- Create the Service Principal
- Assign the permissions at the required scope (/)
- Assign the Directory role permissions
| Repository | Description |
|---|---|
| AzOps-Accelerator | This template repository is for getting started with the AzOps integrated CI/CD solution. |
- Via GitHub portal
- Via command-line GitHub CLI
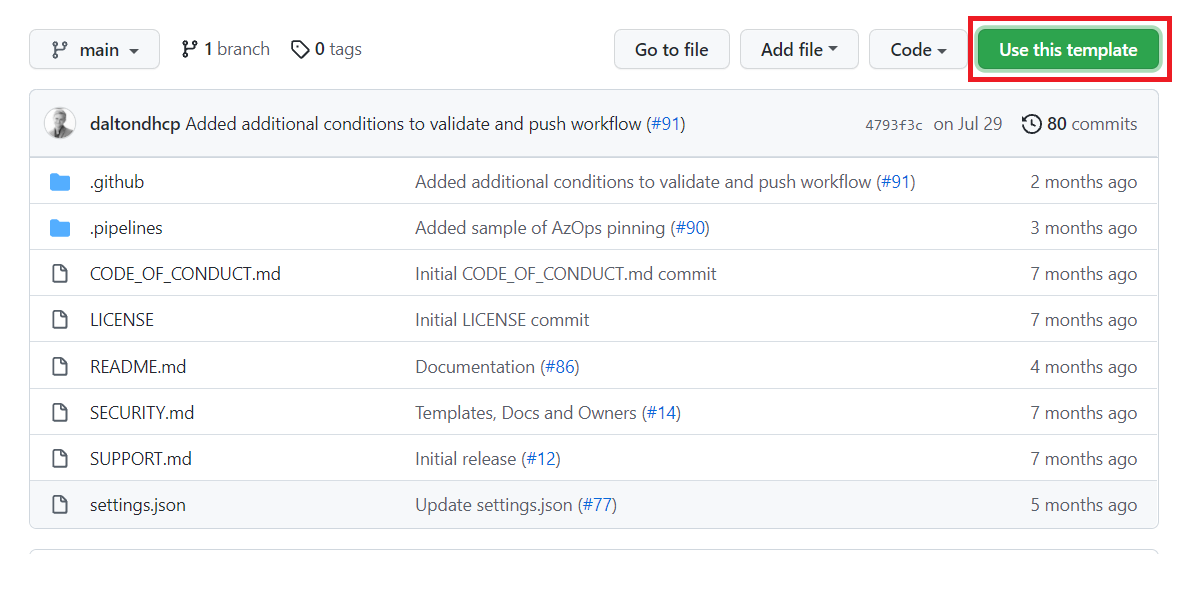
- Navigate to the AzOps-Accelerator repository and click on
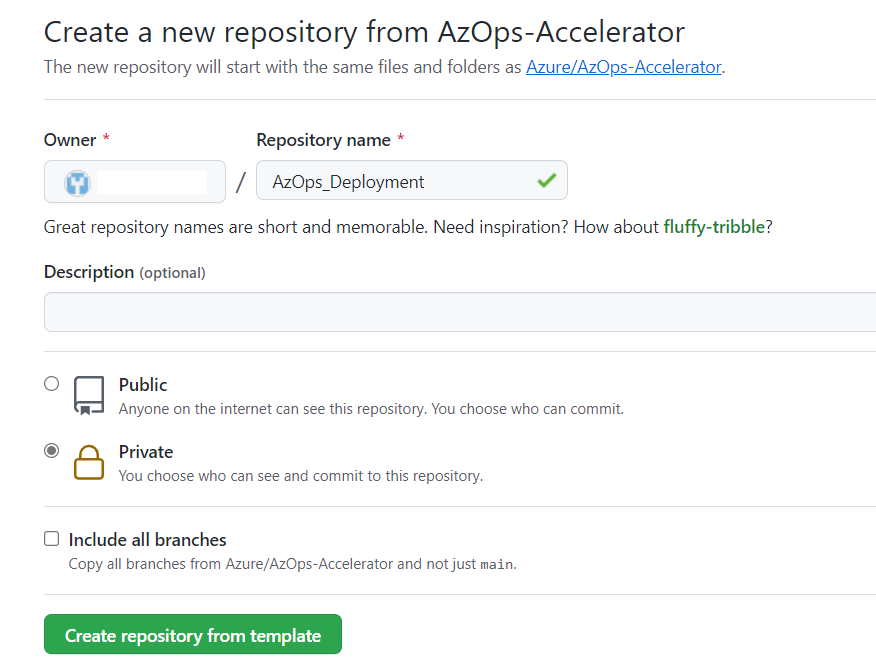
Use this templatebutton to create new repository. If you are using GitHub Enterprise Server, you need to import the repository using the command-line. - Specify whether the new repository should be public or private.
- Review the information you entered, then click Begin import.
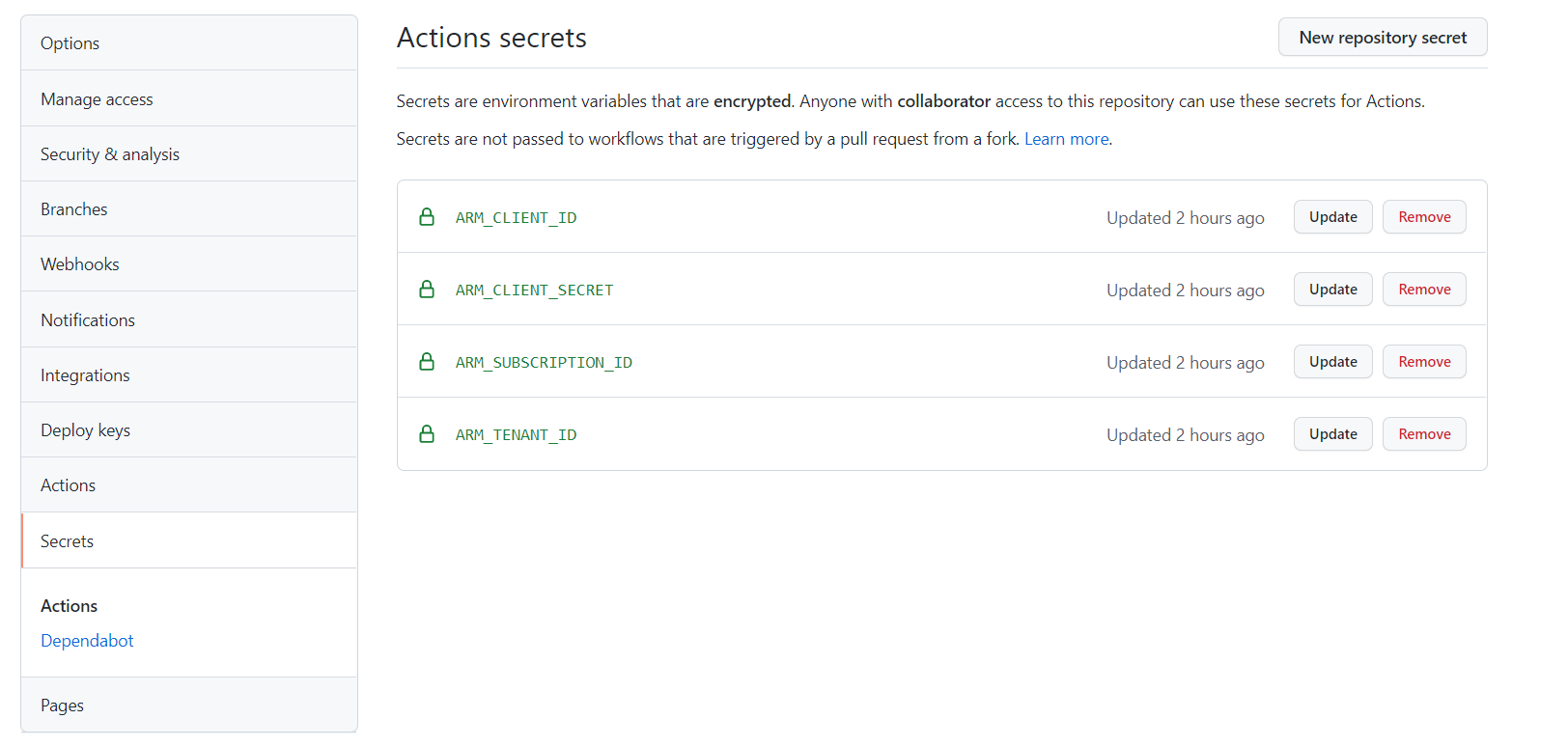
- Navigate to Settings -> Secrets -> Actions and create the required secrets as depicted below. Note that
ARM_CLIENT_SECRETis not required when using federated credentials. - Untick
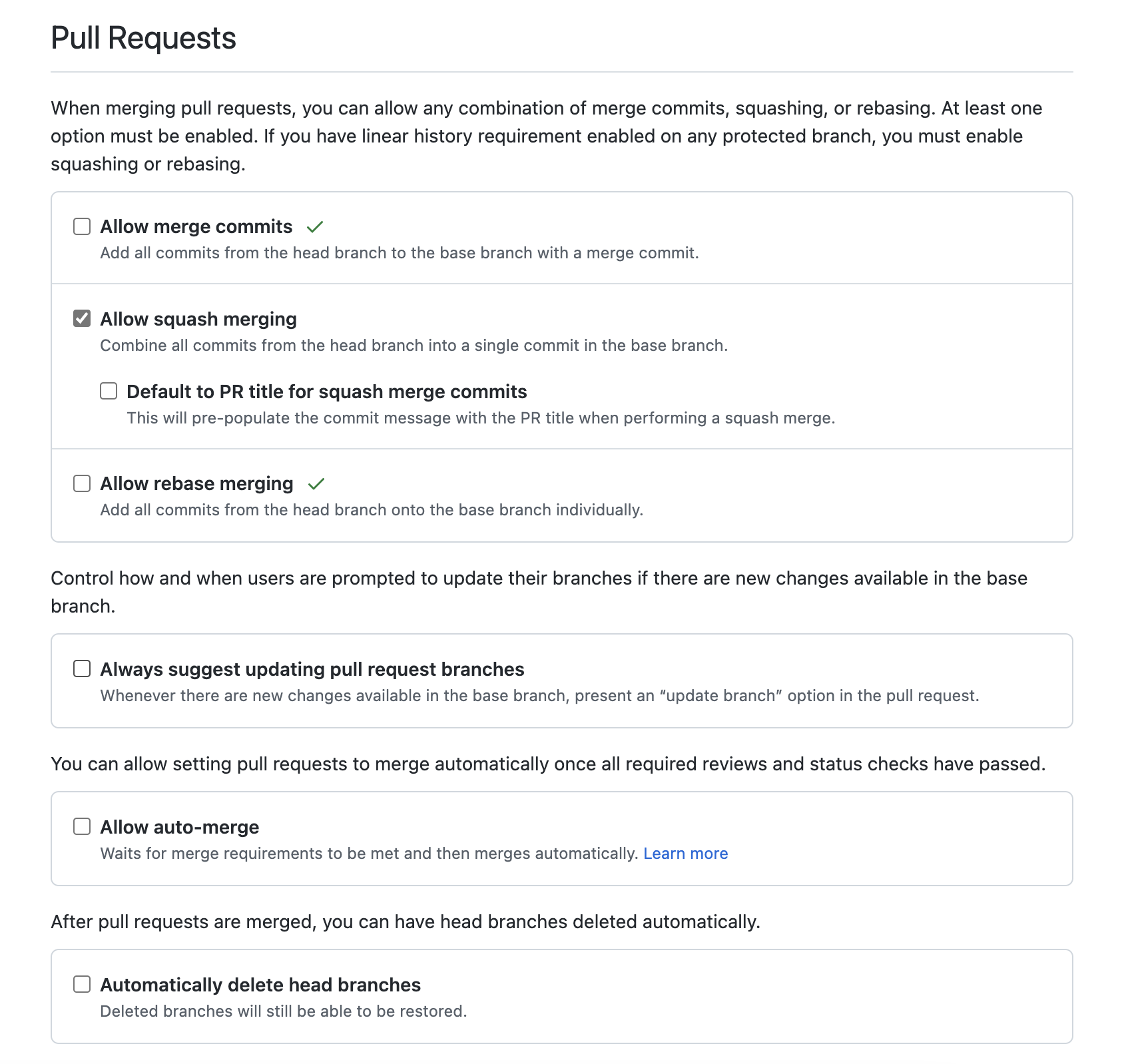
Allow merge commitsandAllow rebase mergingunder Settings -> General -> Pull Requests - Under Settings -> Actions -> General -> Workflow permissions, grant the workflow
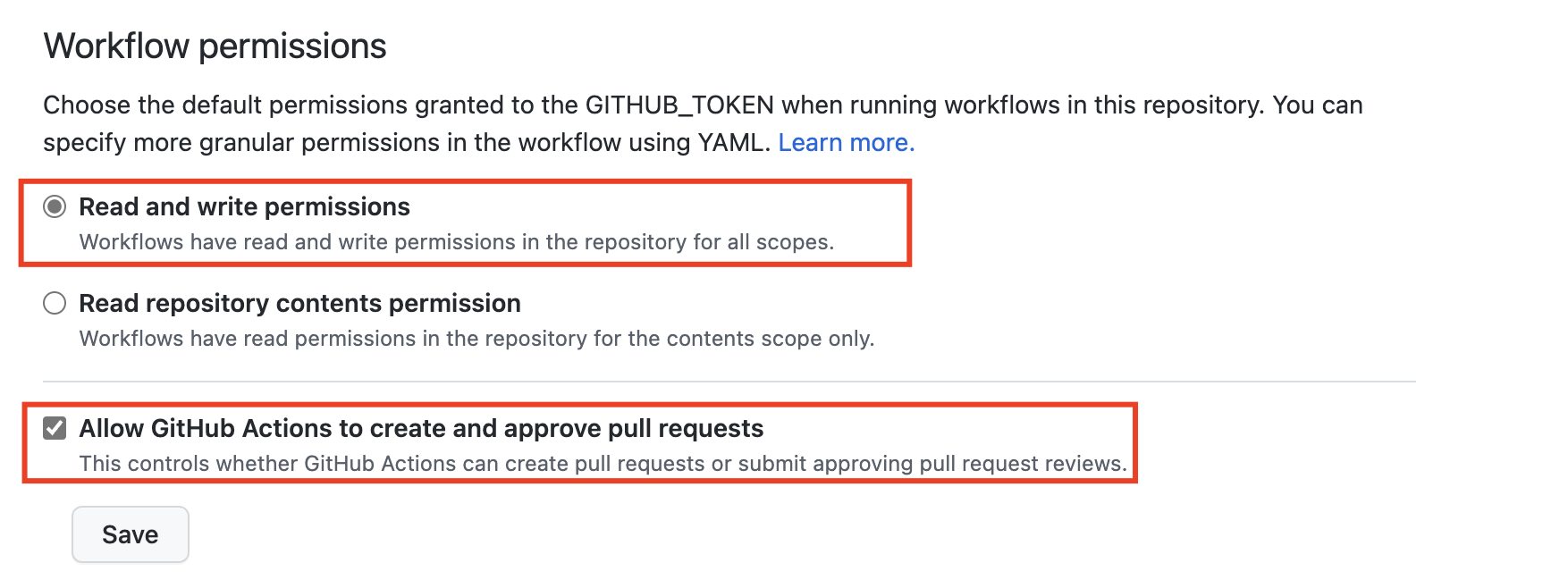
Read and write permissionsas well asAllow GitHub Actions to create and approve pull requests - Navigate to Actions and run the
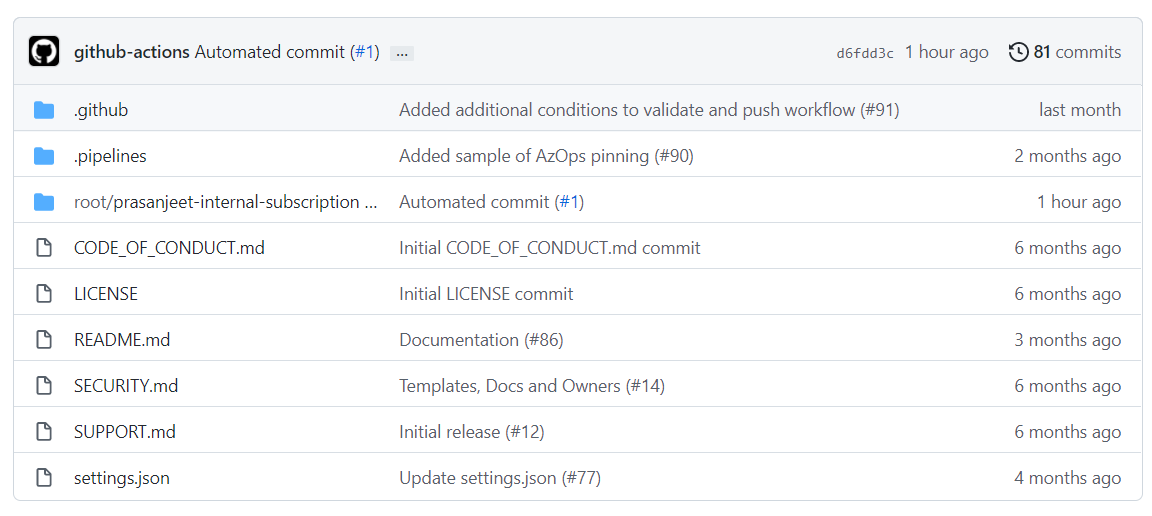
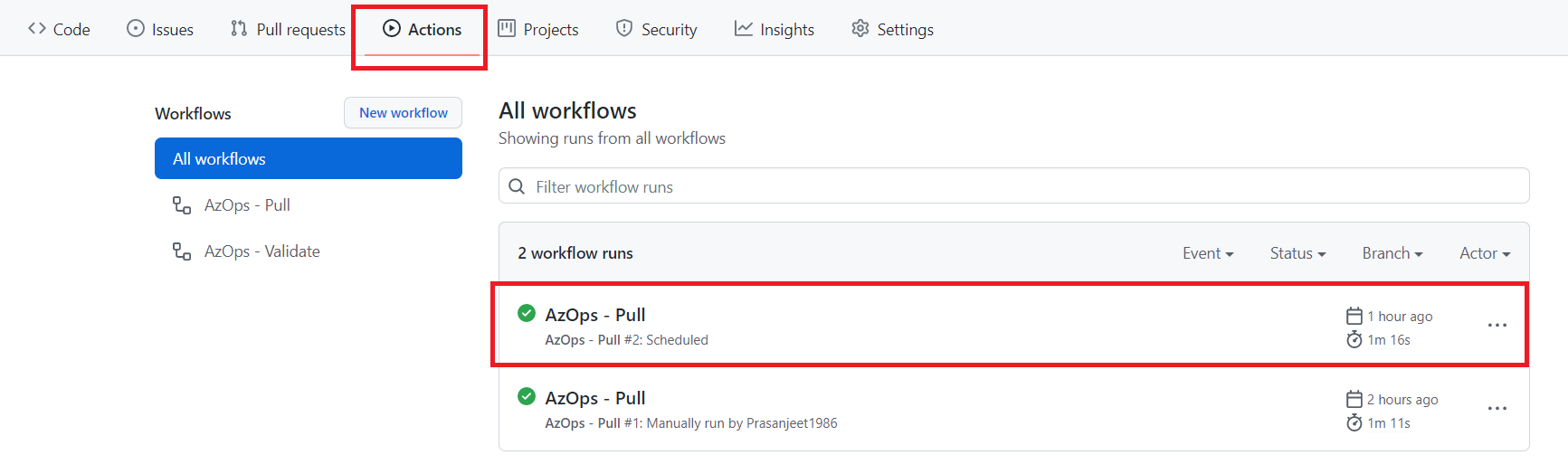
AzOps - Pullworkflow to create a representation of the existing Azure environment/scopes in the repository. The artifacts will by default be stored under therootfolder.Note: All the configuration values can be modified through the
settings.jsonfile to change the default behavior of AzOps. The settings are documented under settings - The repository is now ready for use. Creating a Pull Request with changes to the
rootfolder will trigger the validate pipeline. The validate pipeline will then perform a What-If deployment of the changes and post the results as a comment on the pull request.- Merging the pull request will rigger the push pipeline and deploy the changes to Azure.
- Create the repository from the predefined template
gh repo create '<Name>' --template azure/azops-accelerator --private --confirm
- Add the repository secrets
gh secret set 'ARM_TENANT_ID' -b "<Secret>"
gh secret set 'ARM_SUBSCRIPTION_ID' -b "<Secret>"
gh secret set 'ARM_CLIENT_ID' -b "<Secret>"
gh secret set 'ARM_CLIENT_SECRET' -b "<Secret>" # Not required when using federated credentials((https://github.com/azure/azops/wiki/oidc)
- Disable Allow Merge commits and Allow rebase merging
gh api -X PATCH /repos/{owner}/{repo} -f allow_rebase_merge=false
gh api -X PATCH /repos/{owner}/{repo} -f allow_merge_commit=false
- Grant workflow "Read and write permissions" and "Allow GitHub Actions to create and approve pull requests" permissions
gh api -X PUT /repos/{owner}/{repo}/actions/permissions/workflow -f default_workflow_permissions='write'
gh api -X PUT /repos/{owner}/{repo}/actions/permissions/workflow -F can_approve_pull_request_reviews=true
- Initiate the first Pull workflow
gh api -X POST /repos/{owner}/{repo}/dispatches -f event_type='Enterprise-Scale Deployment'