Containerization vs Virtualization - 180D-FW-2024/Knowledge-Base-Wiki GitHub Wiki

Improvements in traditional computing architecture have made single physical machines extremely powerful. However, most applications rarely utlize the entire stack of hardware resources. In recent years, virtualization and containerization have become key technologies in revolutionizing modern computing environments. Both technologies have become the backbone of large cloud data centers, improving resource utilization and the organization’s return-on-investment. This article provides a detailed overview of virtualization and containerization, comparing their architecture, use cases, and benefits.
Virtualization, in an early form, emerged on IBM mainframes in the 1960s, where system administrators used logical partitions to run multiple instances of operating systems on a single set of hardware. This approach allowed organizations to maximize the use of costly mainframe resources. Over time, virtualization gained traction with VMware in the late 1990s and subsequent open-source hypervisors such as Xen and KVM.
The precursor to modern containerization can be traced back to Unix-like systems, specifically the chroot process introduced in the 1970s. Chroot allowed administrators to isolate a process by changing its root directory. Building on these ideas, tools like LXC (Linux Containers) emerged, eventually leading to the popularity of Docker in 2013. Docker introduced a more user-friendly approach to container management, layering images, and packaging applications along with their dependencies in an easily deployable format. Today, orchestration tools like Kubernetes further streamline container deployment and management, illustrating how containerization has evolved into a foundational technology for modern cloud-native architectures.
Virtualization is a technology that enables the creation of multiple simulated environments or "virtual machines" (VMs) on a single physical machine. These virtual machines operate as independent systems, with their own operating systems, applications, and resources. Virtualization abstracts the hardware, allowing multiple VMs to share the same underlying physical hardware without interfering with each other. When discussing VMs, its important to define what the hypervisor is. A hypervisor, or virtual machine monitor (VMM), is software that creates and manages VMs by separating the operating system and applications from the physical hardware. They can be either ran on the host’s hardware or on top of an existing operating system.

Furthermore, Virtualization can be divided into two types: full and para virtualization. As the name suggest, full virtualization creates virtual versions of the processor, memory, storage device, and network resource to run on their own dedicated guest OS such that the virtualized environments are unaware they are being virtualized. The goal here is to run binaries from the OSs as userlevel processes on top of the hypervisor. On the other hand, para virtualization essentially lets the guest OS see the real hardware underneath the hypervisor and by relation, access and utilize the real hardware resources. If you would like to dive into the technical details on how this is done, look into how Xen employs tricks like page coloring and exploiting the characteristics of the underlying hardware to achieve this type of virtualization. [4]
Containerization, often associated with technologies like Docker, is a lightweight form of virtualization. Containers virtualize the operating system rather than the hardware, sharing the host OS’s kernel and, in many cases, other components. It promises same level of isolation and security as a virtual machine and is more tightly integrated with the host operating system. Container contains only the application and its dependencies, making it a lightweight and highly portable environment. The key components associated with containerization is a container engine to create and deploy containers, the containers itself that run on the host OS, and possibly an orchestration tool to help manage and scale containerized applications across multiple hosts.

LXC, Docker, and rkt are the leading container technologies each with their own specialties. To summarize, LXC allows multiple running applications on a single OS, Docker does not and instead builds a single application environment. Rkt was built on top of Docker to fix security issues pertaining to root-level access using image signature verification. [3]
| Feature | Virtualization | Containerization |
|---|---|---|
| Technology | Hypervisor (e.g., VMware, Hyper-V) | Container Engine (e.g., Docker) |
| Isolation Level | Hardware-level isolation (VMs) | OS-level isolation (Containers) |
| Boot Time | Minutes (OS boot required) | Seconds (Shares host OS kernel) |
| Resource Usage | High (includes full OS per VM) | Low (lightweight and efficient) |
| OS Compatibility | Runs different OS types per VM | Typically uses the host OS kernel |
| Portability | Less portable due to OS dependencies | Highly portable across environments |
| Security | Strong isolation (dedicated OS) | Weaker isolation (shared kernel) |
| Performance | Lower due to hypervisor overhead | Near-native performance |
| Use Case | Legacy applications, full OS needs | Microservices, cloud-native apps |
| Management Tools | VMware vSphere, Microsoft SCVMM | Docker, Kubernetes |
| Resource Overhead | Higher (CPU, RAM) | Lower (shares binaries/libraries) |
| Scalability | Moderate scalability | High scalability and flexibility |
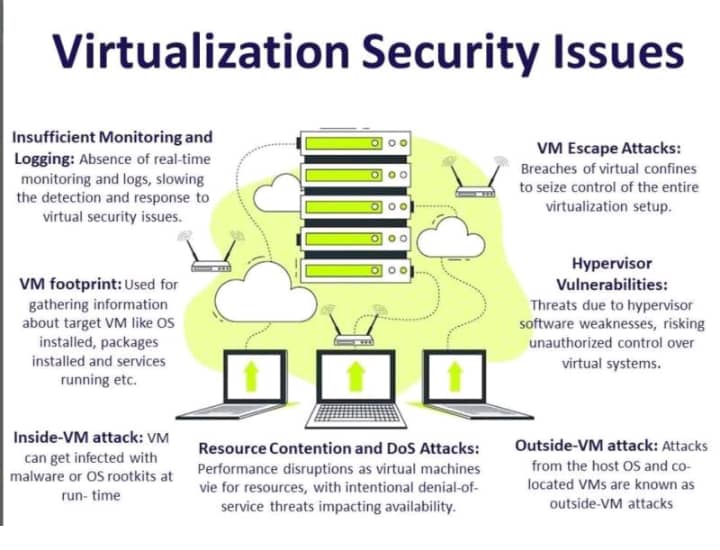
Security is a critical factor when choosing between containerization and virtualization. VMs provide a robust isolation layer because each virtual machine runs its own operating system, reducing the risk of cross-VM attacks. If a VM is compromised, the attacker would find it more challenging to breach the underlying hypervisor or other VMs, assuming proper configurations are in place.
Containers, however, share the host OS kernel. A flaw in the kernel or a misconfiguration in container runtime settings could potentially affect all containers on that host. Despite this, the container ecosystem offers numerous security enhancements, such as mandatory access controls (MAC) with SELinux or AppArmor, and container-specific security profiles. Following best practices, like running containers with the least privileged user, regularly updating images, and scanning for vulnerabilities can greatly reduce risks. In highly regulated environments where stringent isolation is required, a layered security approach may involve combining containers and VMs to achieve both agility and robust protection.
Many organizations implement container image scanning in their DevSecOps pipelines, ensuring vulnerabilities are caught before production. Additionally, networking policies can limit traffic to the minimum necessary paths, thereby reducing the attack surface. Encryption, both at rest and in transit, is widely recommended, alongside proper secrets management solutions. Meanwhile, virtual machines provide a reliable “hard barrier,” but they too can be mismanaged if patching and hypervisor configurations are neglected. Multi-factor authentication (MFA), role-based access control (RBAC), and continuous security monitoring are best practices for both container-based and VM-based environments.
This article will discuss virtualization and containerization in the context of cloud computation as these tend to be the leading industrial application. To do this, we first need to define the 3 critical cloud architectures: Infrastructure as a service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Infrastructure as a Service is a cloud computing service that provides on-demand access to computing resources such as servers, storage, or networking solutions. Platform as a Service provides a complete environment for developing, running, and managing applications. Developers can build an entire software “platform” on the cloud with common providers such as AWS, GCP, or Azure. Finally, Software as a Service allows users to access and use software applications seamlessly over the internet, where the entire software usually runs natively within a browser. [1]

IaaS tend to prefer robustness over portability. It should not be a surprise that the better alternative for IaaS is virtualization. Since containers lack OS flexibility, it is difficult to provide a variety of infrastructure to developers if physical machines are broken up into containers. Furthermore, containers, unlike VMs, share a host OS, making them inherently weaker than VMs in terms of security. [3]
With SaaS, containers tend to be more capable of handling multiple request per second compared to its virtualized counterparts. This lends itself to the fact that SaaS runs as a complete package without the need for changes in the semantics. The product therefore can reach a wider audience and its performance in dealing with this influx of users would determine the quality of the product. [1]
With PaaS it not quite as simple. Since it exhibits half of each quality from both side of the architecture extremes, PaaS can be built either with a VM or container with equal success. There are three proven ways to implement PaaS:
- An application runs in an application level container directly on the host OS (containers)
- An application runs in a VM, with each application on its own VM (virtual machines)
- Each application runs in a containers which is ran on a VM that is meant to host applications
A middle-of-the-road architecture requires a middle-of-the-road approach to best optimize performance. That is why option 3 is the most common implementation choice for PaaS vendors. This extra layer of complexity allows applications to be isolated but also utilize and distribute a fair share of CPU time to all applications running on the VM. [2]
Deciding between containerization and virtualization depends on individual or company needs, application requirements, and organizational goals. If an application needs rapid horizontal scaling, microservices architecture, and efficient resource usage, containers are the right choice. They allow for continuous integration and delivery, giving system admins the power to roll out updates frequently. Additionally, containers integrate well with cloud-native tools such as Kubernetes, Docker Swarm, and various managed services.
Virtualization can be more suitable for legacy applications and scenarios requiring complete OS-level isolation or support for multiple different operating systems on the same hardware. For example, certain enterprise applications that demand a Windows environment alongside Linux-based systems might need distinct virtual machines to ensure compatibility. A hybrid approach may also be adopted, where VMs serve as secure, isolated hosts for container clusters.
- Download and install VirtualBox from the official website (https://www.virtualbox.org/).
- Download an installation media. Example: Ubuntu (https://ubuntu.com/download/desktop)
- Open VirtualBox and click New.
- Enter the name and choose the operating system you installed.
- Set the memory and disk space allocation based on requirements.
- On Linux: Install Docker via the package manager (e.g., sudo apt install docker on Ubuntu).
- On Windows/Mac: Download Docker Desktop from https://www.docker.com/ and install it.
- Open the terminal and use the following command to pull a simple web server container
docker run -d -p 8080:80 nginx - Access the web server by navigating to http://localhost:8080 in your browser.
Both virtualization and containerization have revolutionized computing, offering unique advantages depending on application needs. Virtualization provides robust isolation and compatibility, while containerization excels in efficiency, portability, and speed. Understanding the differences in the context of cloud architectures helps organizations optimize resources. Whether deploying VMs or containers, each technology is a key enabler in today’s cloud and data center environments.
- A. M, A. Dinkar, S. C. Mouli, S. B and A. A. Deshpande, "Comparison of Containerization and Virtualization in Cloud Architectures," 2021 IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 2021, pp. 1-5, doi: 10.1109/CONECCT52877.2021.9622668. keywords: {Cloud computing;Conferences;Architecture;Computer architecture;Containers;Market research;Robustness;cloud architectures;SaaS;PaaS;IaaS;Virtualization},
- R. Dua, A. R. Raja and D. Kakadia, "Virtualization vs Containerization to Support PaaS," 2014 IEEE International Conference on Cloud Engineering, Boston, MA, USA, 2014, pp. 610-614, doi: 10.1109/IC2E.2014.41. keywords: {Containers;Linux;Kernel;Virtual machining;Security;Resource management;File systems;container;virtualization;paas},
- Bhardwaj, A., Krishna, C.R. Virtualization in Cloud Computing: Moving from Hypervisor to Containerization—A Survey. Arab J Sci Eng 46, 8585–8601 (2021). https://doi.org/10.1007/s13369-021-05553-3
- J. Watada, A. Roy, R. Kadikar, H. Pham and B. Xu, "Emerging Trends, Techniques and Open Issues of Containerization: A Review," in IEEE Access, vol. 7, pp. 152443-152472, 2019, doi: 10.1109/ACCESS.2019.2945930. keywords: {Containers;Virtualization;Security;Cloud computing;Virtual machine monitors;Linux;Tools;Virtualization;containerization;management and orchestration;isolation and security},